YrbkMgr
Occasional Visitor
Last May I posted this thread AiProtection Alerts - Should I Be Concerned? Basically, I was told that since "The MAC address shown is outside your network , the sending device", not to worry about it as the protection was working.
Recently however, I've been getting alerts from a device on my LAN and even though it's being blocked, it's happening with such frequency, I want to see if I can eliminate the "cause".
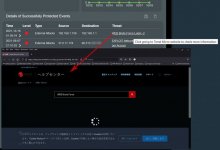
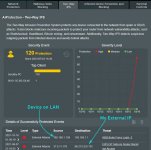
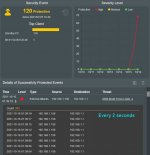
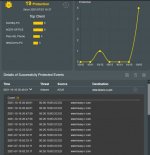
IPS Two Way Protection: The source of the attack is 192.168.1.158 which is a Win 7 HP Pavilion on my LAN and the destination is the AC3200. There were over 60 attempts blocked at 2 second intervals on 10/16/2021 alone, and over 300 entries in total from that source:
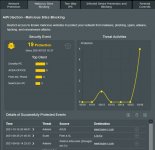
Malicious Site Blocking is blocking Adware from my AC3200 to Heavy-r, some porn site:
How do I track down what is causing this on the source machine (192.168.1.158)? Any thoughts?
Recently however, I've been getting alerts from a device on my LAN and even though it's being blocked, it's happening with such frequency, I want to see if I can eliminate the "cause".
IPS Two Way Protection: The source of the attack is 192.168.1.158 which is a Win 7 HP Pavilion on my LAN and the destination is the AC3200. There were over 60 attempts blocked at 2 second intervals on 10/16/2021 alone, and over 300 entries in total from that source:


Malicious Site Blocking is blocking Adware from my AC3200 to Heavy-r, some porn site:


How do I track down what is causing this on the source machine (192.168.1.158)? Any thoughts?