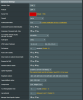
Hello all,
Recently discovered that my RT-N66U has OpenVPN capability built in. I decided I would like to be able to tunnel all my traffic in public WiFi through my home router as well as access folder shares.
I have never worked with VPNs before and wanted to check about your thoughts for security
- Is the Asus OpenVPN implementation safe to use, or do you guys use any additional security features?
- Should I change the default port from 1194 to avoid port scanners?
- I noticed that 'admin' is a user on the OpenVPN that I cannot get rid of - does this mean I should change the router admin password to something only a password manager would remember? Or does the admin user not actually log onto the VPN
Thanks in advance
Recently discovered that my RT-N66U has OpenVPN capability built in. I decided I would like to be able to tunnel all my traffic in public WiFi through my home router as well as access folder shares.
I have never worked with VPNs before and wanted to check about your thoughts for security
- Is the Asus OpenVPN implementation safe to use, or do you guys use any additional security features?
- Should I change the default port from 1194 to avoid port scanners?
- I noticed that 'admin' is a user on the OpenVPN that I cannot get rid of - does this mean I should change the router admin password to something only a password manager would remember? Or does the admin user not actually log onto the VPN
Thanks in advance