TheLyppardMan
Very Senior Member
I was curious to know why the FRITZ!Box 7530 AX router supplied by my ISP (which I'm keeping as a backup) failed the GRC ShieldsUP! port-scan test, while my RT-AX88U Pro passes the test.
I did receive a reply today from my ISP (Zen Internet), but it's in technical language, which I don't fully understand, so I was wondering if someone could offer me a simple summary of what it means?
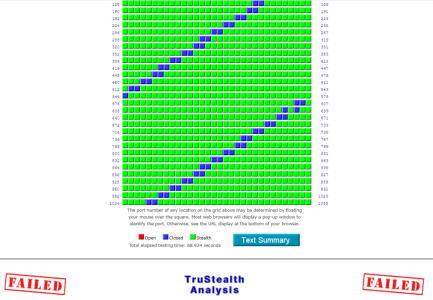
This is the message I received and the attachement I am uploading shows the result of the port-scan test.
"Thank you very much for the enquiry you sent to our AVM support team.
Some servers on the Internet send a reply request to the IP address of the client that has contacted them to verify that the client actually exists under this IP address.
The servers send TCP-SYN packets (TCP packets that initiate a connection) to the IP address of the client on port 113 and/or 1080. When the ports are completely blocked by the firewall of the client ("Stealthed" or "Secure"), theses TCP-SYN packets are blocked without the server receiving a reply. In this case, the server drops the connection.
Thus, the FRITZ!Box blocks TCP ports 113 and 1080 for TCP-SYN packets from the Internet, yet reply requests for these ports with an RST packet (TCP-Reset = rejected reply). In this case, no attack on the LAN via these TCP ports is possible, but the existence can be verified by a server on the Internet via a rejected reply.
The existence of the closed ports 113 and/or 1080 does not pose a security threat. Computers on the LAN cannot be accessed from the Internet via these ports.
If the FRITZ!Box should reject unsolicited requests from the internet instead of replying with ICMP control messages, enable the option "Firewall in stealth mode" under "Internet > Filters > Lists > Global Filter Settings" in the FRITZ!Box user interface."
I did follow the suggested procedure to set the firewall to stealth mode when I first got the FRITZ!Box, but even so, port 113 still remained as closed, rather than stealthed. Also, I'd forgotten that I had followed that procedure and when I reverted back from the latest beta firmware (which they call "Lab") once Wireguard became available on the latest official firmware. Doing so required the router to be reset to factory defaults, which I now know is why I lost the firewall stealth settings that I had previously enabled (my memory is quite flaky at times nowadays nd probably age-related).
I did receive a reply today from my ISP (Zen Internet), but it's in technical language, which I don't fully understand, so I was wondering if someone could offer me a simple summary of what it means?
This is the message I received and the attachement I am uploading shows the result of the port-scan test.
"Thank you very much for the enquiry you sent to our AVM support team.
Some servers on the Internet send a reply request to the IP address of the client that has contacted them to verify that the client actually exists under this IP address.
The servers send TCP-SYN packets (TCP packets that initiate a connection) to the IP address of the client on port 113 and/or 1080. When the ports are completely blocked by the firewall of the client ("Stealthed" or "Secure"), theses TCP-SYN packets are blocked without the server receiving a reply. In this case, the server drops the connection.
Thus, the FRITZ!Box blocks TCP ports 113 and 1080 for TCP-SYN packets from the Internet, yet reply requests for these ports with an RST packet (TCP-Reset = rejected reply). In this case, no attack on the LAN via these TCP ports is possible, but the existence can be verified by a server on the Internet via a rejected reply.
The existence of the closed ports 113 and/or 1080 does not pose a security threat. Computers on the LAN cannot be accessed from the Internet via these ports.
If the FRITZ!Box should reject unsolicited requests from the internet instead of replying with ICMP control messages, enable the option "Firewall in stealth mode" under "Internet > Filters > Lists > Global Filter Settings" in the FRITZ!Box user interface."
I did follow the suggested procedure to set the firewall to stealth mode when I first got the FRITZ!Box, but even so, port 113 still remained as closed, rather than stealthed. Also, I'd forgotten that I had followed that procedure and when I reverted back from the latest beta firmware (which they call "Lab") once Wireguard became available on the latest official firmware. Doing so required the router to be reset to factory defaults, which I now know is why I lost the firewall stealth settings that I had previously enabled (my memory is quite flaky at times nowadays nd probably age-related).