Marty
Occasional Visitor
Intro: I know now that this is not a new issue but I just ran into it and I don't think ASUS is going to resolve it so thought I post here in case someone found a solution. I know the work around is just to use a lower security level in the OpenVPN phone app, I'll default to that for now if I have to but would rather find a better solution until I can replace my router.
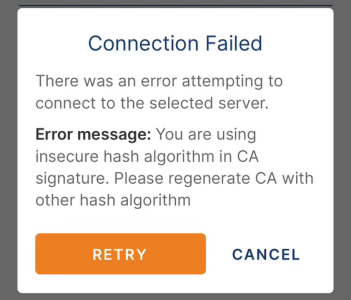
Issue: I have just run across this after updating the OpenVPN app on my phone to 3.4.1. I have spent time discussing this with OpenVPN, who were very helpful and ASUS who were not helpful. I have the ASUS RT-AC87U (yeah its old) and am running the latest firmware (yeah, that's old too After realizing that the 3.4.1 version of the OpenVPN app's default security level was causing the "You are using insecure hash algorithm in CA signature." error, I went into my router and changed the Encryption cipher to AES 256 CBC in combination with using SHA256 for the HMAC Authentication and then created a new client.opvn file. However that did not work, got the same error.
After realizing that the 3.4.1 version of the OpenVPN app's default security level was causing the "You are using insecure hash algorithm in CA signature." error, I went into my router and changed the Encryption cipher to AES 256 CBC in combination with using SHA256 for the HMAC Authentication and then created a new client.opvn file. However that did not work, got the same error.
The OpenVPN tech looked at my log files from the phone and found the following.. .. "[Jan 17, 2024, 13:38:47] EVENT: WARN TLS: received certificate signed with SHA1. Please inform your admin to upgrade to a stronger algorithm. Support for SHA1 signatures will be dropped in the future"
The OpenVPN tech said... "In the case of your server (my router), the encryption cipher and the hash are using secure options, but the signature in the certificate is using a weak one." This matches what the error msg says on my phone. My router does not offer me the "Renew Certificate" button like some ASUS router screens I've seen on the internet while searching for a solution, maybe that due to me running ASUS firmware and not Merlin, I don’t know. It doesn't seem to matter which ciper or HMAC authentication I use, when applying my changes and then clicking Export, the file is signed with SHA1 and the new OpenVPN app rejects it. Sure I can use the lowest security option in the phone app but I would rather solve this issue instead and I don't have time right now to look for a new router and set it up as I'm about to go on travel and wanted to use the VPN on my phone. - ugh.
Does anyone know a way to get my router to sign with a more secure algorithm, like SHA254 or?
Issue: I have just run across this after updating the OpenVPN app on my phone to 3.4.1. I have spent time discussing this with OpenVPN, who were very helpful and ASUS who were not helpful. I have the ASUS RT-AC87U (yeah its old) and am running the latest firmware (yeah, that's old too
The OpenVPN tech looked at my log files from the phone and found the following.. .. "[Jan 17, 2024, 13:38:47] EVENT: WARN TLS: received certificate signed with SHA1. Please inform your admin to upgrade to a stronger algorithm. Support for SHA1 signatures will be dropped in the future"
The OpenVPN tech said... "In the case of your server (my router), the encryption cipher and the hash are using secure options, but the signature in the certificate is using a weak one." This matches what the error msg says on my phone. My router does not offer me the "Renew Certificate" button like some ASUS router screens I've seen on the internet while searching for a solution, maybe that due to me running ASUS firmware and not Merlin, I don’t know. It doesn't seem to matter which ciper or HMAC authentication I use, when applying my changes and then clicking Export, the file is signed with SHA1 and the new OpenVPN app rejects it. Sure I can use the lowest security option in the phone app but I would rather solve this issue instead and I don't have time right now to look for a new router and set it up as I'm about to go on travel and wanted to use the VPN on my phone. - ugh.
Does anyone know a way to get my router to sign with a more secure algorithm, like SHA254 or?