nsomnac
New Around Here
I've got an RT-N66U running the latest Asus distributed firmware.
I recently updated TunnelBlick on my Mac, of which other forums suggested to replace the DH params with a 1024bit prime. I did, but I think there is a bug in the certificate admin form, as it munged all the existing ca, cert, and key.
I tried replacing those again but from the existing client ovpn file I have, and now, while the server doesn't complain of errors, the client does.
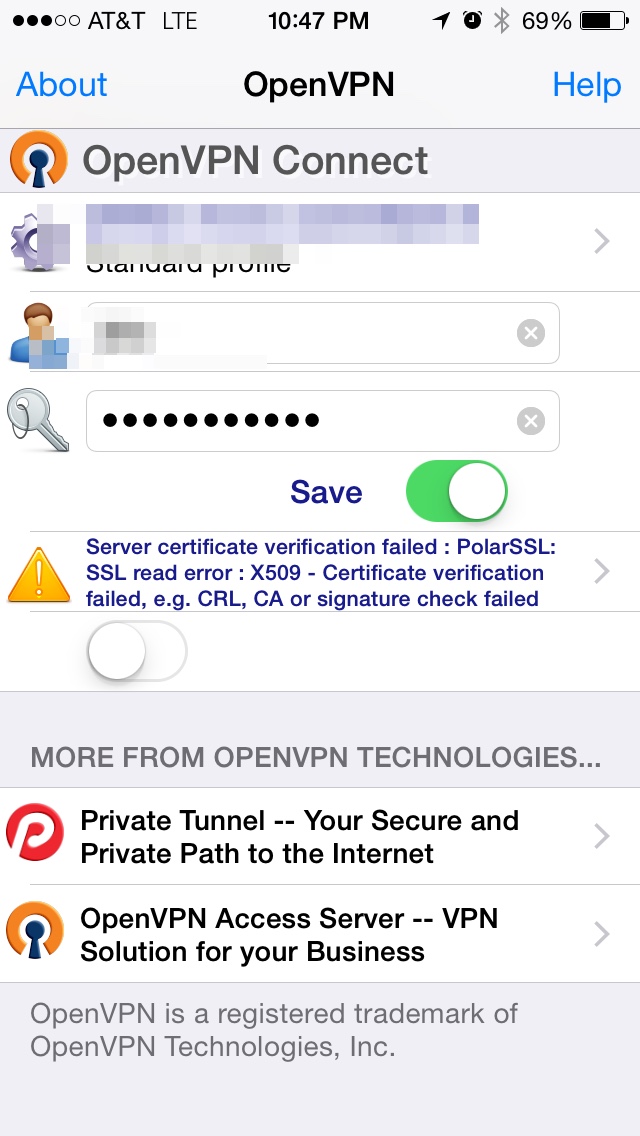
Can anyone assist?
I'm happy to just regenerate my own CA, cert, and key - I'm just not sure how to do this. I kinda see how to do this from the easy-rsa tool, but not sure how to go from the dozen or so files to 3 fields in the firmware screens.
Thanks for any direction and pointers.
BTW: everything was working fine until I upgraded TunnelBlick and subsequently modified all the certs and dh params.
Jim
I recently updated TunnelBlick on my Mac, of which other forums suggested to replace the DH params with a 1024bit prime. I did, but I think there is a bug in the certificate admin form, as it munged all the existing ca, cert, and key.
I tried replacing those again but from the existing client ovpn file I have, and now, while the server doesn't complain of errors, the client does.

Can anyone assist?
I'm happy to just regenerate my own CA, cert, and key - I'm just not sure how to do this. I kinda see how to do this from the easy-rsa tool, but not sure how to go from the dozen or so files to 3 fields in the firmware screens.
Thanks for any direction and pointers.
BTW: everything was working fine until I upgraded TunnelBlick and subsequently modified all the certs and dh params.
Jim

