Leguar
Occasional Visitor
RT-AX88U Merlin v. 386.2_4
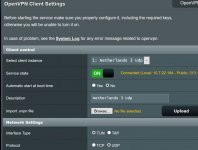
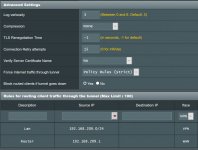
As you can see, I have a VPN Client running. Service state is ON (picture 1 and 2).
Now and then I have to close the tunnel, and go back to my normal Lan.
If I disable the Service state (OFF), my whole Lan goes down and I have to reboot
the router to get connected to the internet again (without VPN).
I think, that when I decide to stop the service, the kill switch should not break in,
and turn my Lan down.
Am I right or not ??
As you can see, I have a VPN Client running. Service state is ON (picture 1 and 2).
Now and then I have to close the tunnel, and go back to my normal Lan.
If I disable the Service state (OFF), my whole Lan goes down and I have to reboot
the router to get connected to the internet again (without VPN).
I think, that when I decide to stop the service, the kill switch should not break in,
and turn my Lan down.
Am I right or not ??