outlaw78
Regular Contributor
Hello all!
I just started messing with OpenVPN on the latest merlin build. I am hosting a VPN server to access my home network devices and use its internet. Got it all set up and working on my AC5300. I was surprised at how fast it was. I was using it on a Galaxy S9+ on Sprint LTE+ when it was working. Then all of a sudden it quit working on LTE+. It would still connect to the VPN but I could not access home network devices (when it did, it was like it wouldn't load completely), nor could I access the router thru its local IP address. It looked like packets were still flowing in and out. IPV6 is disabled on my home router although its available from my internet provider.
I have been working with Sprint but they can't find an issue on their side. However, when I connect to CDMA (3G) or external Wi-Fi network, it works flawlessly again.
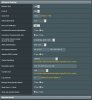
I am using the OpenVPN app from the play store which is 3.0.5.(1816). I imported the generated .OVPN to the app and set the app, under settings, to:
Reconnect on Reboot on
Seamless Tunnel on
VPN Protocol UDP
IPV6- IPV4-Only Tunnel
Connection Timeout - 1 Min
Compression - Full
AES-CBC cipher algorithm Off
Use insecure algorithms Off
Minimum TLS Version TLS 1.2
DNS Fallback On
Shortcut Minimize On
Show Notifications Off
I noticed that sometimes when I check the connection status, it shows me connected with an IPV6 even though the app is set to IPV4 only tunnel.
If I need to post any more information to help with this, let me know. I just can figure out why one minute it was working great and the next minute it wasn't. I rebooted all devices (cable modem, router, phone) and even set VPN server to "defaults" and started over to no avail. I googled the problem but anything I found, I tried and the only thing to work was "Switch to CDMA" but that really isn't an option due to speed.
Also, I can't seem to access the NAS web-gui. I get an error "Forbidden", you don't have permission to access /UI on this server. Additionally, a 404 not found error was encountered while trying to use an ErrorDocument to handle the request. When I am physically on the LAN without VPN, I can access those pages just fine.
Thank you in advance!
UPDATE: I can access the shares on the NAS using Solid File Explorer and I can SSH into router (Set for LAN only), but I can not access any web-gui on the router (just hangs there but works fine from behind the router), printer or NAS devices using their LAN IP when on VPN. Speedtest app says "Error, test failed to complete. Please check your connection and try again."
I just started messing with OpenVPN on the latest merlin build. I am hosting a VPN server to access my home network devices and use its internet. Got it all set up and working on my AC5300. I was surprised at how fast it was. I was using it on a Galaxy S9+ on Sprint LTE+ when it was working. Then all of a sudden it quit working on LTE+. It would still connect to the VPN but I could not access home network devices (when it did, it was like it wouldn't load completely), nor could I access the router thru its local IP address. It looked like packets were still flowing in and out. IPV6 is disabled on my home router although its available from my internet provider.
I have been working with Sprint but they can't find an issue on their side. However, when I connect to CDMA (3G) or external Wi-Fi network, it works flawlessly again.
I am using the OpenVPN app from the play store which is 3.0.5.(1816). I imported the generated .OVPN to the app and set the app, under settings, to:
Reconnect on Reboot on
Seamless Tunnel on
VPN Protocol UDP
IPV6- IPV4-Only Tunnel
Connection Timeout - 1 Min
Compression - Full
AES-CBC cipher algorithm Off
Use insecure algorithms Off
Minimum TLS Version TLS 1.2
DNS Fallback On
Shortcut Minimize On
Show Notifications Off
I noticed that sometimes when I check the connection status, it shows me connected with an IPV6 even though the app is set to IPV4 only tunnel.
If I need to post any more information to help with this, let me know. I just can figure out why one minute it was working great and the next minute it wasn't. I rebooted all devices (cable modem, router, phone) and even set VPN server to "defaults" and started over to no avail. I googled the problem but anything I found, I tried and the only thing to work was "Switch to CDMA" but that really isn't an option due to speed.
Also, I can't seem to access the NAS web-gui. I get an error "Forbidden", you don't have permission to access /UI on this server. Additionally, a 404 not found error was encountered while trying to use an ErrorDocument to handle the request. When I am physically on the LAN without VPN, I can access those pages just fine.
Thank you in advance!
UPDATE: I can access the shares on the NAS using Solid File Explorer and I can SSH into router (Set for LAN only), but I can not access any web-gui on the router (just hangs there but works fine from behind the router), printer or NAS devices using their LAN IP when on VPN. Speedtest app says "Error, test failed to complete. Please check your connection and try again."
Last edited: