Dear Community,
I try now for some time to connect to my home-network with an Android-Smartphone by establishing a VPN-tunnel. Somehow it doesn't work and therefore I hope, you can help me.
I have an Asus RT-AC88U with Merlin Firmeware version 384.7_2.
My Network-Setup is the following:
(Internet) ---> WAN(Fritzbox)LAN ---> WAN(Asus RT-AC88U)LAN/WLAN ---> (Home-Network-Devices)
Fritzbox-LAN: 192.168.1.XXX
Asus RT-AC88U-LAN: 192.112.1.XXX
I did the following:
Fritzbox: On the Fritzbox I set up a port-forwarding to the Asus-Router for the VPN-Port I use. Also on the Fritzbox I set up a DynDNS to be reachable over the internet.
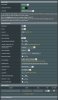
Asus-Router: Here I turned the VPN-Server-option on. I tried severals options. For this post, I take the default-options as a foundation (see screenshot (I uploaded it as an attachement, I hope, thats ok)). I then exported the cerfiticate and manually changed the IP-adress in the remote-line of the certificate to the DynDNS-address.
Smartphone (Android): I downloaded the OpenVPN-Connect-App and imported the certificate. Then I started the connection and typed in my credentials.
Asus Router: The Router does establish a VPN-tunnel to the phone (-> it shows the username in the table as connected). But I can not reach any devices inside the home-network. This (I think) is because in my understanding the Asus-Router creates a new subnet (10.8.0.0) and separate this strictly from the home-network (I cannot define the home-network as VPN-Subnet).
I tried many different options (I cannot recall all of them), but nothing seems to work.
So my question is: Do you know, how I can either put my VPN-tunnel directly into the home-network or how to create kind of a tunnel between the two subnets?
This seems to be a common problem, because I found quite some issues like this one in the internet. Yet nothing really helped me. What confuse me, is, that the possible options and configurations differ among each other and from mine (maybe because of different firmware-versions and/or devices?!). For example, I don't have the option "Push LAN to clients" that many others have. I did not find any post or tutorial, that has my possible options.
Sorry for language mistakes for I am not a native speaker. Also I may know some stuff about IT, but I am no network specialist.
I hope someone can help me.
Thank you in advance,
Lambda
I try now for some time to connect to my home-network with an Android-Smartphone by establishing a VPN-tunnel. Somehow it doesn't work and therefore I hope, you can help me.
I have an Asus RT-AC88U with Merlin Firmeware version 384.7_2.
My Network-Setup is the following:
(Internet) ---> WAN(Fritzbox)LAN ---> WAN(Asus RT-AC88U)LAN/WLAN ---> (Home-Network-Devices)
Fritzbox-LAN: 192.168.1.XXX
Asus RT-AC88U-LAN: 192.112.1.XXX
I did the following:
Fritzbox: On the Fritzbox I set up a port-forwarding to the Asus-Router for the VPN-Port I use. Also on the Fritzbox I set up a DynDNS to be reachable over the internet.
Asus-Router: Here I turned the VPN-Server-option on. I tried severals options. For this post, I take the default-options as a foundation (see screenshot (I uploaded it as an attachement, I hope, thats ok)). I then exported the cerfiticate and manually changed the IP-adress in the remote-line of the certificate to the DynDNS-address.
Smartphone (Android): I downloaded the OpenVPN-Connect-App and imported the certificate. Then I started the connection and typed in my credentials.
Asus Router: The Router does establish a VPN-tunnel to the phone (-> it shows the username in the table as connected). But I can not reach any devices inside the home-network. This (I think) is because in my understanding the Asus-Router creates a new subnet (10.8.0.0) and separate this strictly from the home-network (I cannot define the home-network as VPN-Subnet).
I tried many different options (I cannot recall all of them), but nothing seems to work.
So my question is: Do you know, how I can either put my VPN-tunnel directly into the home-network or how to create kind of a tunnel between the two subnets?
This seems to be a common problem, because I found quite some issues like this one in the internet. Yet nothing really helped me. What confuse me, is, that the possible options and configurations differ among each other and from mine (maybe because of different firmware-versions and/or devices?!). For example, I don't have the option "Push LAN to clients" that many others have. I did not find any post or tutorial, that has my possible options.
Sorry for language mistakes for I am not a native speaker. Also I may know some stuff about IT, but I am no network specialist.
I hope someone can help me.
Thank you in advance,
Lambda