abraxas86
Occasional Visitor
Not too sure where to post this, hopefully this is the right place...
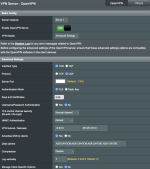
I'm doing my best to follow the tutorials to get an OpenVPN server going for intermittent use on my home router. I'm up to my neck in documentation for everything, but I'm reaching a point where I'm not sure how much more I can branch out before I start losing everything I've gathered.
I'm trying to use the easy-rsa package that comes with the router (for the sake of consistency with the wiki tutorial)
After setting up the vars and trying to run
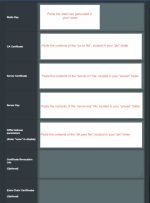
I read the script to see what it was doing - it's checking the version of OpenSSL that's installed, and tries to call the appropriate .cnf file based on the version, however there is no openssl-1.1.1.cnf. The only .cnf that comes with the package is openssl-1.0.0.cnf
I'm not confident enough that I can just rename the 1.0.0 to make it work, and I'm not sure I'd be able to troubleshoot any further to make sense of anything that goes wrong at that point. I don't even know how many people use this script often - I could likely do it from my Linux computer without issue, but the vars file I got there was much different from the one in the tutorial and I didn't want to mess it up...
No rush on a solution, I'm gonna take a nap for a bit and maybe take another swing at this all later with a refreshed mind, but if anybody could point me in the right direction I would be grateful.
Thanks in advance.
[EDIT] Realized I should probably check the easy-rsa side of things. Looks like the package included with the router is the older version. It should be updated to version 3 which I think includes support for OpenSSL 1.1.1. It's also why the vars file I had locally looked so much different from the one on the router. Anyway, gonna get some sleep - I'll take another crack at it later.
I'm doing my best to follow the tutorials to get an OpenVPN server going for intermittent use on my home router. I'm up to my neck in documentation for everything, but I'm reaching a point where I'm not sure how much more I can branch out before I start losing everything I've gathered.
I'm trying to use the easy-rsa package that comes with the router (for the sake of consistency with the wiki tutorial)
After setting up the vars and trying to run
source ./vars, I encountered an error that it couldn't find the .cnf file (specifically, "No /mnt/sda1/easy-rsa/openssl.cnf file could be found")I read the script to see what it was doing - it's checking the version of OpenSSL that's installed, and tries to call the appropriate .cnf file based on the version, however there is no openssl-1.1.1.cnf. The only .cnf that comes with the package is openssl-1.0.0.cnf
I'm not confident enough that I can just rename the 1.0.0 to make it work, and I'm not sure I'd be able to troubleshoot any further to make sense of anything that goes wrong at that point. I don't even know how many people use this script often - I could likely do it from my Linux computer without issue, but the vars file I got there was much different from the one in the tutorial and I didn't want to mess it up...
No rush on a solution, I'm gonna take a nap for a bit and maybe take another swing at this all later with a refreshed mind, but if anybody could point me in the right direction I would be grateful.
Thanks in advance.
[EDIT] Realized I should probably check the easy-rsa side of things. Looks like the package included with the router is the older version. It should be updated to version 3 which I think includes support for OpenSSL 1.1.1. It's also why the vars file I had locally looked so much different from the one on the router. Anyway, gonna get some sleep - I'll take another crack at it later.
Last edited: