Sébastien GEOFFROY
Occasional Visitor
Hi all,
I configured out VPN server on my Asus router (Merlin fw).
I exported openvpn file from it and then I imported this file to my Android smartphone (openvpn client installed).
Connection is ok but when launching apps to connect to some of my LAN devices (cam, asus router app,..), I'm not able to have those app working (connexion ko).
I suppose it's something related to proxy or route settings. I tried to add a static route but I lost connection to my router (I had to reset it and reinstall firmware...I suppose I did something wrong).
My infra is :
ISP router (192.168.0.1 / wifi off / Asus router set up as DMZ host) ---> Asus Router (192.168.0.2 / 192.168.1.1) --> LAN devices (192.168.1.0/24)
Can you please help me in making my VPN configuration working ?
Regards.
Sebastien
Here below my settings.


On client side (android smartphone connected to GSM / Wifi off):

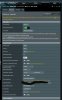
I did the setup for port fowarding:

IFCONFIG shows:
=> Asus LAN network
br0 Link encap:Ethernet HWaddr 04 4:C4:46:15:A8
4:C4:46:15:A8
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
UP BROADCAST RUNNING ALLMULTI MULTICAST MTU:1500 Metric:1
RX packets:1924667 errors:0 dropped:500 overruns:0 frame:0
TX packets:7074642 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:274554439 (261.8 MiB) TX bytes:9136506930 (8.5 GiB)
=> ISP LAN
eth0 Link encap:Ethernet HWaddr 04 4:C4:46:15:A8
4:C4:46:15:A8
inet addr:192.168.0.2 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING ALLMULTI MULTICAST MTU:1500 Metric:1
RX packets:7038830 errors:0 dropped:3464 overruns:0 frame:0
TX packets:1732704 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:9134578510 (8.5 GiB) TX bytes:262497817 (250.3 MiB)
=> VPN VLAN
tun21 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 -00
inet addr:10.8.0.1 P-t-P:10.8.0.1 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP PROMISC MULTICAST MTU:1500 Metric:1
RX packets:431 errors:0 dropped:0 overruns:0 frame:0
TX packets:477 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:71519 (69.8 KiB) TX bytes:127536 (124.5 KiB)
ROUTE shows:
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 192.168.0.1 0.0.0.0 UG 0 0 0 eth0
10.8.0.0 * 255.255.255.0 U 0 0 0 tun21
127.0.0.0 * 255.0.0.0 U 0 0 0 lo
192.168.0.0 * 255.255.255.0 U 0 0 0 eth0
192.168.0.1 * 255.255.255.255 UH 0 0 0 eth0
192.168.1.0 * 255.255.255.0 U 0 0 0 br0
IPTABLE stuff (what I did):
iptables -I INPUT 2 -p udp --dport 1194 -j ACCEPT
iptables -I FORWARD -i br0 -o tun21 -j ACCEPT
iptables -I FORWARD -i tun21 -o br0 -j ACCEPT
OPENVPN config file (Asus side) :
# Automatically generated configuration
daemon ovpn-server1
topology subnet
server 10.8.0.0 255.255.255.0
proto udp
port 1194
dev tun21
txqueuelen 1000
ncp-ciphers AES-256-GCM:AES-128-GCM:AES-256-CBC:AES-128-CBC
cipher AES-128-CBC
keepalive 15 60
verb 3
push "route 192.168.1.0 255.255.255.0 vpn_gateway 500"
client-config-dir ccd
client-to-client
duplicate-cn
push "redirect-gateway def1"
plugin /usr/lib/openvpn-plugin-auth-pam.so openvpn
ca ca.crt
dh dh.pem
cert server.crt
key server.key
script-security 2
up updown.sh
down updown.sh
status-version 2
status status 5
I configured out VPN server on my Asus router (Merlin fw).
I exported openvpn file from it and then I imported this file to my Android smartphone (openvpn client installed).
Connection is ok but when launching apps to connect to some of my LAN devices (cam, asus router app,..), I'm not able to have those app working (connexion ko).
I suppose it's something related to proxy or route settings. I tried to add a static route but I lost connection to my router (I had to reset it and reinstall firmware...I suppose I did something wrong).
My infra is :
ISP router (192.168.0.1 / wifi off / Asus router set up as DMZ host) ---> Asus Router (192.168.0.2 / 192.168.1.1) --> LAN devices (192.168.1.0/24)
Can you please help me in making my VPN configuration working ?
Regards.
Sebastien
Here below my settings.
On client side (android smartphone connected to GSM / Wifi off):
I did the setup for port fowarding:
IFCONFIG shows:
=> Asus LAN network
br0 Link encap:Ethernet HWaddr 04
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
UP BROADCAST RUNNING ALLMULTI MULTICAST MTU:1500 Metric:1
RX packets:1924667 errors:0 dropped:500 overruns:0 frame:0
TX packets:7074642 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:274554439 (261.8 MiB) TX bytes:9136506930 (8.5 GiB)
=> ISP LAN
eth0 Link encap:Ethernet HWaddr 04
inet addr:192.168.0.2 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING ALLMULTI MULTICAST MTU:1500 Metric:1
RX packets:7038830 errors:0 dropped:3464 overruns:0 frame:0
TX packets:1732704 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:9134578510 (8.5 GiB) TX bytes:262497817 (250.3 MiB)
=> VPN VLAN
tun21 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 -00
inet addr:10.8.0.1 P-t-P:10.8.0.1 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP PROMISC MULTICAST MTU:1500 Metric:1
RX packets:431 errors:0 dropped:0 overruns:0 frame:0
TX packets:477 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:71519 (69.8 KiB) TX bytes:127536 (124.5 KiB)
ROUTE shows:
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 192.168.0.1 0.0.0.0 UG 0 0 0 eth0
10.8.0.0 * 255.255.255.0 U 0 0 0 tun21
127.0.0.0 * 255.0.0.0 U 0 0 0 lo
192.168.0.0 * 255.255.255.0 U 0 0 0 eth0
192.168.0.1 * 255.255.255.255 UH 0 0 0 eth0
192.168.1.0 * 255.255.255.0 U 0 0 0 br0
IPTABLE stuff (what I did):
iptables -I INPUT 2 -p udp --dport 1194 -j ACCEPT
iptables -I FORWARD -i br0 -o tun21 -j ACCEPT
iptables -I FORWARD -i tun21 -o br0 -j ACCEPT
OPENVPN config file (Asus side) :
# Automatically generated configuration
daemon ovpn-server1
topology subnet
server 10.8.0.0 255.255.255.0
proto udp
port 1194
dev tun21
txqueuelen 1000
ncp-ciphers AES-256-GCM:AES-128-GCM:AES-256-CBC:AES-128-CBC
cipher AES-128-CBC
keepalive 15 60
verb 3
push "route 192.168.1.0 255.255.255.0 vpn_gateway 500"
client-config-dir ccd
client-to-client
duplicate-cn
push "redirect-gateway def1"
plugin /usr/lib/openvpn-plugin-auth-pam.so openvpn
ca ca.crt
dh dh.pem
cert server.crt
key server.key
script-security 2
up updown.sh
down updown.sh
status-version 2
status status 5