Hi All,
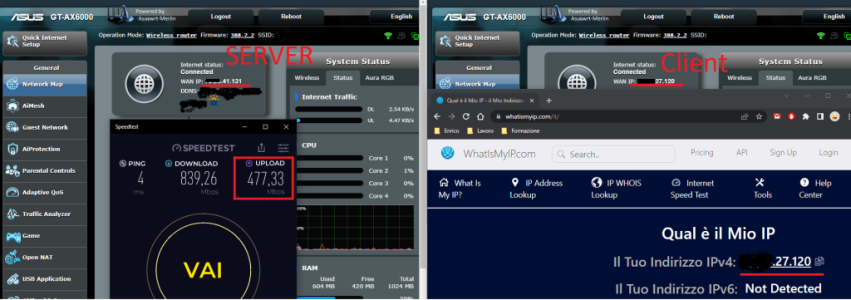
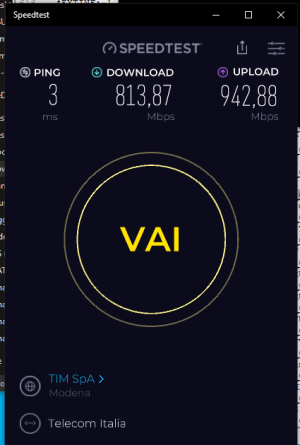
I am having 2 x AX88U routers running Merlin FW, installed in 2 remote locations and I was using OVPN server+client on both sides with NAT to enable site to site connectivity for connected LAN devices and occasional routing of both segments to Internet via different ISPs connected to WANs. This configuration was working, but local-to-local performance was not great.
I know there was a comprehensive manual on SNB to configure site-to-site VPN without NAT, but it was requiring some extensive config via shell and it was not so critical so I have lived without it.
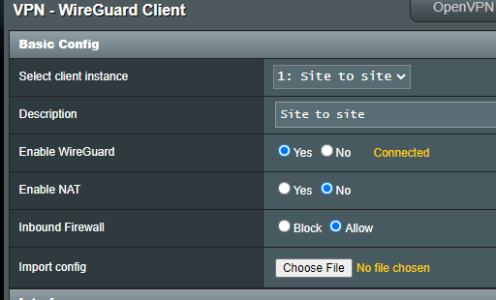
Now with 388.1 and Wireguard support being added, I have taken a try to migrate from Openvpn to Wireguard.
First observation:
I have followed this guide: https://www.asus.com/support/FAQ/1048281 (Scenario 3, two-way communication) but connected LANs routing was not working until I have added the VPN director rule on the client side to route local subnet to remote server local subnet over this WG tunnel.

On the server side, no rules were created, remote LAN segment appears to be routed to client without any extra rules.
I can see in the announcement that
Second observation: NAT is disabled as per instructions but access to remote WAN of the server is still working (if routing is configured by the additional rule), so it seems remote server is doing NAT for local network clients. Is that a correct understanding?
Third observation: If I need to route some clients on both sides to the WAN interface of the opposite side - do I need to create another pair of Wireguard server + client with NAT enabled and add some rules in VPN director to route the traffic to remote (Scenario 2, one-way communication)?
When I do this, should I change the default settings of wireguard server from 10.6.0.1/32 to some other subnet to avoid same subnet running on WG servers which are interconnected?

I am having 2 x AX88U routers running Merlin FW, installed in 2 remote locations and I was using OVPN server+client on both sides with NAT to enable site to site connectivity for connected LAN devices and occasional routing of both segments to Internet via different ISPs connected to WANs. This configuration was working, but local-to-local performance was not great.
I know there was a comprehensive manual on SNB to configure site-to-site VPN without NAT, but it was requiring some extensive config via shell and it was not so critical so I have lived without it.
Now with 388.1 and Wireguard support being added, I have taken a try to migrate from Openvpn to Wireguard.
First observation:
I have followed this guide: https://www.asus.com/support/FAQ/1048281 (Scenario 3, two-way communication) but connected LANs routing was not working until I have added the VPN director rule on the client side to route local subnet to remote server local subnet over this WG tunnel.
On the server side, no rules were created, remote LAN segment appears to be routed to client without any extra rules.
I can see in the announcement that
So I assume I did everything right and one VPN rule is required on the client side, but NOT required on the server side (actually there is no rule possible while there is no WG client running). Is that correct understanding or did I miss anything?Also, by default, no traffic is routed through WireGuard, you need to configure rules in VPNDirector. This is identical to the stock firmware which requires you to create VPN Fusion rules to handle WireGuard client traffic.
Second observation: NAT is disabled as per instructions but access to remote WAN of the server is still working (if routing is configured by the additional rule), so it seems remote server is doing NAT for local network clients. Is that a correct understanding?
Third observation: If I need to route some clients on both sides to the WAN interface of the opposite side - do I need to create another pair of Wireguard server + client with NAT enabled and add some rules in VPN director to route the traffic to remote (Scenario 2, one-way communication)?
When I do this, should I change the default settings of wireguard server from 10.6.0.1/32 to some other subnet to avoid same subnet running on WG servers which are interconnected?
Last edited: