I have a spare AC68U and want to use it to allow wifi users to only access the internet. Can I connect the AC68U's WAN port to my LAN, set it's subnet to be different from my LAN's, and have the users only be able to access the Internet but have no access to my LAN? I guess I basically want those users to not be able to access anything on my LAN except for the LAN gateway. The AC68U will have it's own DHCP server for the wifi users but the WAN port's ip will come from the LAN's DHCP server.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Block wireless users from wan subnet?
- Thread starter badbob001
- Start date
CaptainSTX
Part of the Furniture
This will only work the way you want if the AC68 is the first router. And any device connected to the second router will be able able to see all devices on the first router even though they are in a different subnet.
Sent from my 9024W using Tapatalk
Sent from my 9024W using Tapatalk
L&LD
Part of the Furniture
You can plug in a LAN cable from your main router's LAN port to the WAN port on the spare RT-AC68U and use it in router mode (double nat) and only use the Guest WiFi with full isolation enabled.
If your main network is in the 192.168.x.x range, I suggest to use the 10.x.x.x or the 172.16.x.x - 172.31.x.x ranges.
Test to make sure that no Guest Network clients can connect to your main network and you should be set.
HTH.
If your main network is in the 192.168.x.x range, I suggest to use the 10.x.x.x or the 172.16.x.x - 172.31.x.x ranges.
Test to make sure that no Guest Network clients can connect to your main network and you should be set.
HTH.
ColinTaylor
Part of the Furniture
That doesn't isolate the guests from the main router's LAN. Quite the opposite in fact.You can plug in a LAN cable from your main router's LAN port to the WAN port on the spare RT-AC68U and use it in router mode (double nat) and only use the Guest WiFi with full isolation enabled.
To block access to the main LAN in this configuration the secondary router would need to have a Network Services Filter rule which blocked all traffic to the main LAN's subnet (e.g. 192.168.1.x).
Last edited:
L&LD
Part of the Furniture
@ColinTaylor, in my experience, that depends on the routers used. 
That is why I suggested testing to ensure no access. We could then respond further.
That is why I suggested testing to ensure no access. We could then respond further.
ColinTaylor
Part of the Furniture
Not really, it's basic networking.@ColinTaylor, in my experience, that depends on the routers used.
L&LD
Part of the Furniture
@ColinTaylor, I've stated this before but I will repeat it here (can't find that post right now).
With two RT-AC68U routers, being connected as ISP, R1main and R2secondary and R1main having an IP range of 192.168.1.x and R2secondary having an IP range of 192.168.2.x the following was observed.
The R2secondary routers' users could access the main routers' LAN.
The R1main routers' users could not access the secondary routers' LAN.
Both R1 and R2 routers are in Router mode. With a LAN port/cable of the R1 router plugged into the WAN cable of the R2 router.
This is repeatable across many networks for a few years now.
With two RT-AC68U routers, being connected as ISP, R1main and R2secondary and R1main having an IP range of 192.168.1.x and R2secondary having an IP range of 192.168.2.x the following was observed.
The R2secondary routers' users could access the main routers' LAN.
The R1main routers' users could not access the secondary routers' LAN.
Both R1 and R2 routers are in Router mode. With a LAN port/cable of the R1 router plugged into the WAN cable of the R2 router.
This is repeatable across many networks for a few years now.
ColinTaylor
Part of the Furniture
Agreed. That was exactly the point I was making. You appear to have been stating the opposite in post #3. Maybe I was misinterpreting what you wrote.With two RT-AC68U routers, being connected as ISP, R1main and R2secondary and R1main having an IP range of 192.168.1.x and R2secondary having an IP range of 192.168.2.x the following was observed.
The R2secondary routers' users could access the main routers' LAN.
The R1main routers' users could not access the secondary routers' LAN.
The physical layout you described is what I'm envisioning. My R1 router is an AC86U connected to the IPS. The R2 router is my AC68U connected to the LAN of the AC86U.With two RT-AC68U routers, being connected as ISP, R1main and R2secondary and R1main having an IP range of 192.168.1.x and R2secondary having an IP range of 192.168.2.x the following was observed.
The R2secondary routers' users could access the main routers' LAN.
The R1main routers' users could not access the secondary routers' LAN.
Both R1 and R2 routers are in Router mode. With a LAN port/cable of the R1 router plugged into the WAN cable of the R2 router.
BUT I don't want R2 users to access the R1 LAN (except to get to the internet via the R1 router). I don't need or care about R1 users accessing R2's network.
I think I just need to be able to set outgoing firewall rules on the R2 router to block ip ranges used by the R1 LAN. But the firewall options are limited to:
- inbound rules
- url filter
- keyword filter
- network services filter (port ranges)
Would it help if I don't put any users on R2's LAN ports?
ColinTaylor
Part of the Furniture
Creating a black hole route would work (provided it doesn't conflict with the default route). As I suggested above you can achieve the same result with the Network Services Filter. You don't have to specify ports with the NSF. If you leave that field blank it will apply to all ports. You will have to create one rule for UDP and another for TCP.
With NSF, depending on which firmware version you're using you can specify the entire upstream subnet as either 192.168.1.0/24 or 192.168.1.*.
With NSF, depending on which firmware version you're using you can specify the entire upstream subnet as either 192.168.1.0/24 or 192.168.1.*.
Last edited:
I tried the black hole route method first and at first it seemed to work but then it didn't after I switched my client's ip from between the two subnets a few times.Creating a black hole route would work (provided it doesn't conflict with the default route). As I suggested above you can achieve the same result with the Network Services Filter. You don't have to specify ports with the NSF. If you leave that field blank it will apply to all ports. You will have to create one rule for UDP and another for TCP.
With NSF, depending on which firmware version you're using you can specify the entire upstream subnet as either 192.168.1.0/24 or 192.168.1.*.
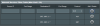
View attachment 24356
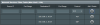
View attachment 24357
On R2 router:
Then I tried NSF and it does seem to work! At first I ignored it because I thought it was limited to just port ranges but it's not (just like you said). This is what I used (R1 ip range is 192.168.1.* and R2 ip range is 192.168.100.*):- In Lan > Lan IP, change router ip to 192.168.100.15. Note that subnet of R1 router is 192.168.1.x.
- In Lan > Route, add
- network/ip: 192.168.1.1
- netmask: 255.255.255.0
- Gateway: 127.0.0.1
- Metric: blank
- Interface: LAN
- Filter table type: Black List
- Filtered ICMP packet types: 0 8
- Rule 1: Destination IP: 192.168.1.* TCP
- Rule 2: Destination IP: 192.168.1.* UDP
If this is really the answer, then asus should implement it for guest networks under aimesh/multiple-ap.
Thanks!
Last edited:
Also, tried to block wifi users from accessing R2 router's management interfaces but NSF rules don't seem to work for that. Maybe Asus don't want us to accidentally block ourselves from the router, though I do have enabled management from WAN (which is R1's LAN)?
NSF rules I tried:
NSF rules I tried:
- Destination: 192.168.100.15, Port Range: 80, Protocol: TCP
- Destination: 192.168.100.15, Port Range: 8443, Protocol: TCP
- Destination: 192.168.100.15, Port Range: 22, Protocol: TCP
ColinTaylor
Part of the Furniture
The clients still need to be able to talk to the router otherwise they can't get DHCP and DNS (and as you say, the ability to make changes to the router). Trying to block the access with NSF won't work as NSF only effects LAN to WAN and you are trying to block LAN to LAN.Also, tried to block wifi users from accessing R2 router's management interfaces but NSF rules don't seem to work for that.
To create a more fine-grained access to the router from its LAN you could create a custom firewall script (if you're using Merlin's firmware). YazFi already has an option that does that for you for guest WiFi networks.
P.S. You can restrict access to the router by IP address using the Access restriction list in the webUI. So you could restrict web/ssh/telnet access from only 192.168.1.0/24.
Last edited:
L&LD
Part of the Furniture
Agreed. That was exactly the point I was making. You appear to have been stating the opposite in post #3. Maybe I was misinterpreting what you wrote.
I guess I didn't make it clear enough (sorry).
Using a higher IP address for the main router will give the OP what he wants.
Specifically, if the main router had a "192.168.(greater than '1' range).x" IP range and the secondary router's Guest network was used with a "192.168.(less than '2').x" range.
ColinTaylor
Part of the Furniture
Sorry, I don't follow this at all. Are you talking about something different from the original question now?Using a higher IP address for the main router will give the OP what he wants.
Specifically, if the main router had a "192.168.(greater than '1' range).x" IP range and the secondary router's Guest network was used with a "192.168.(less than '2').x" range.
I can't see why the IP address ranges would be relevant (provided they don't overlap), and what you're saying is the opposite of the example you gave in post #7.
Last edited:
L&LD
Part of the Furniture
@ColinTaylor, sorry, really busy these past few days.
The example is different because of the information I provided later.
When I had a 'main' router with a higher IP address, a secondary router with a lower IP address wasn't able to access it (but the main router could access the secondary router though).
From what I remember, right now.
The example is different because of the information I provided later.
When I had a 'main' router with a higher IP address, a secondary router with a lower IP address wasn't able to access it (but the main router could access the secondary router though).
From what I remember, right now.
ColinTaylor
Part of the Furniture
It doesn't matter whether subnets are numerically higher or lower than each other. The only thing that matters is the routing and firewall rules.When I had a 'main' router with a higher IP address, a secondary router with a lower IP address wasn't able to access it (but the main router could access the secondary router though).
ColinTaylor
Part of the Furniture
And yet that is how the OP has got his setup working now (primary=192.168.1.x, secondary=192.168.100.x). There are also numerous other posts in these forums where Asus users have configured their primary router as 192.168.1.x and the secondary as 192.168.2.x. I myself was running exactly this setup for a while with my AC68U and N66U.I would agree with you that is how it should work. But that is not my experience. At least, not with Asus routers.
Similar threads
- Replies
- 1
- Views
- 227
- Replies
- 22
- Views
- 1K
- Replies
- 6
- Views
- 480
- Replies
- 5
- Views
- 881
Similar threads
Similar threads
-
How to block certain DNS sites specifically Samsung to avoid update pushes
- Started by Gravityz
- Replies: 15
-
-
How To Block/Unblock Internet Access For A Single Device/IP via Command Line on AsusWRT?
- Started by dwp
- Replies: 6
-
How to block a range of local client (LAN) IP's from WAN/Internet
- Started by Spere
- Replies: 11
-
RT-AC66U B1 (Firmware 386.51255) - is there a way to block incoming IP address?
- Started by Zolt
- Replies: 9
-
-
Apparent problem when using the Wireless MAC Filter
- Started by TheLyppardMan
- Replies: 1
Latest threads
-
-
-
-
Firmware version clarification
- Started by gogreen1
- Replies: 3
-
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 627 (members: 10, guests: 617)

