Forgive the following explanation, I know it's long.
There are three ways to configure an adapters DNS servers. (1). By configuring it directly on the NIC. (2). Using the DNS servers as specified on the WAN page of the router configuration and (3). Configuring the DNS servers on the DHCP tab of the LAN page of the router configuration.
If the PCs (local) NIC is configured with known DNS servers belonging to a VPN provider I get a DNS leak off and on VPN. If I specify the block-outside-dns directive in the openVPN config file I plug the leak when connected to the VPN. The DNS server is shown as the VPN server. However, this does not resolve the leak when not connected to the VPN.
If I use a public DNS server on the NIC (configured via any of the three above methods), such as cloudflare, Google, OpenDNS, or my ISPs DNS servers I do not see the leak. ipeak.net reports the DNS servers are those of the public DNS (in some cases, as with google, I get up to 32 DNS server addresses according to ipleak.net and dnsleaktes.com). This is true off VPN and on VPN without the block-oustide-dns. With a public DNS server and on VPN with block-outside-dns I see only the VPN server.
I guess technically there's a fourth method; Automatic config on the NIC and no router configuration at all. In this case I get the ISP DNS.
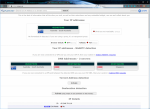
I see identical behavior on two different ISPs. The behavior is so identical (including the DNS Servers selected - 89.187.162.162 and 89.187.162.215), that it's creepy and makes the hairs on the back of my neck stand up.
Using ipconfig /all...
The VPN (TAP), connection always shows the VPN DNS servers. The local NIC will show IP addresses depending on how the DNS servers are configured.
(1). If the DNS server is configured on the NIC as the routers address I will see the routers IP if the DNS Servers are specified on the WAN Page.
(2). If I specify nothing on the local NIC (automatic config), it will show the DNS Servers on the WAN page.
(3). Unless I also specify DNS servers on the LAN page, which always overrides the server configured on the WAN page.
In cases (2) and (3). ipconfig /all will show the configured DNS Servers.
The results are the same for both UDP and TCP VPN connections.
This is all with just the OpenVPN software installed. (
https://openvpn.net/community-downloads/)
If I install the NordVPN app I do not get a leak regardless of the configuration. It's proprietry software so I don't know what it's doing but it "appears" to be specifying block-outside-dns since the symptoms look identical with the block-outside-dns with the OpenVPN config. I;'ve asked Nord to confirm this, but given this is closed software I doubt they'll disclose what the app is doing.
However, the app is junk (imho). I can't disable auto update. It takes between 23-30 seconds to connect to a server. "Pick best" always picks worst, though I can configure it to pick a specific server. I am always on VPN as soon as the PC boots. With VPN the connect takes 3-8 seconds. The app also has annoying advertising. So using it is not a preference.
Since the app can prevent leaks I figure it might be possible to fix them without the app, I just don't know what the app is doing.
The attached images show what leak test sites report when connected to the VPN with the VPN DNS Servers configured on the local NIC (via any of the three methods), and without the block-outside-dns directive.