sam_semillia
New Around Here
Hi,
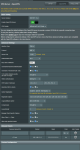
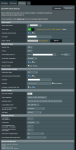
I am running 2 Asus Routers (RT-AC88U and RT-AX88U) on 2 different geographical locations. Both routers running ASUSWRT-Merlin 384.19_0.
Both routers are running a running DHCP server for their respective location: 1392.168.1.0/24 for first location and 192.168.2.0/24 for second location.
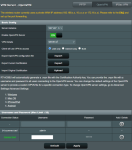
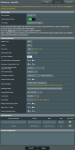
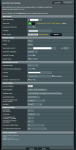
Please see atatched network diagram for details:

What I now would like to accomplish via VPN is the following:
Thanks and BR
I am running 2 Asus Routers (RT-AC88U and RT-AX88U) on 2 different geographical locations. Both routers running ASUSWRT-Merlin 384.19_0.
Both routers are running a running DHCP server for their respective location: 1392.168.1.0/24 for first location and 192.168.2.0/24 for second location.
Please see atatched network diagram for details:
What I now would like to accomplish via VPN is the following:
- Clients should be able to connect to each other by IP
- IE: 192.168.1.199 should be able to connect to 192.168.2.150 and vice versa.
- Clients should be able to connect to each other by NAME
- IE: Clientname2 should be able to connect to Client123 and vice versa.
Thanks and BR