Chuckles67
Regular Contributor
After installing YazFi the Guest Network has two tabs: Guest Network and YazFi.
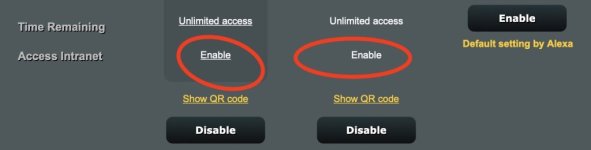
Before installing YazFi the Guest Network tab showed Access Intranet as Disable.
After installing YazFi the same Guest Network tab shows Access Intranet as Enable - though I did not change this setting in this tab (nor did I enable Two-way to Guest in YazFi tab). I want guest network clients to have no access to intranet. Is this expected UI after installing YazFi?
(apologies if this was already posted: I couldn't find)
Before installing YazFi the Guest Network tab showed Access Intranet as Disable.
After installing YazFi the same Guest Network tab shows Access Intranet as Enable - though I did not change this setting in this tab (nor did I enable Two-way to Guest in YazFi tab). I want guest network clients to have no access to intranet. Is this expected UI after installing YazFi?
(apologies if this was already posted: I couldn't find)