rugglebear
Occasional Visitor
Hello,
I used to use Stubby which I installed via Entware, but I believe that is now depreciated.
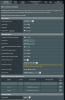
I now utilize the setting in Merlin within WAN > Internet Connection > DNS Privacy Protocol, set to 'DNS-over-TLS' (settings attached in a screenshot).
However, when I visit https://1.1.1.1/help it does not show DNS-over-TLS as active, whereas it used to with Stubby.
I also checked this page, which shows DoT as 'false', https://tenta.com/test/
Any assistance is appreciated. Thank you!
I used to use Stubby which I installed via Entware, but I believe that is now depreciated.
I now utilize the setting in Merlin within WAN > Internet Connection > DNS Privacy Protocol, set to 'DNS-over-TLS' (settings attached in a screenshot).
However, when I visit https://1.1.1.1/help it does not show DNS-over-TLS as active, whereas it used to with Stubby.
I also checked this page, which shows DoT as 'false', https://tenta.com/test/
Any assistance is appreciated. Thank you!