1. Install WireGuard
You need Entware-aarch64-3.10 to use wireguard without a new firmware build.
ㅡ Kernel Module ㅡ
RT-AC86U, GT-AC2900 - 4.1.27
RT-AX88U, GT-AX11000 - 4.1.51
RT-AX68U, RT-AX86U - 4.1.52
ㅡ User space tool ㅡ
2. as Client configuration setting.
nano /opt/etc/init.d/S50wireguard
Init file has 5 options.
Mode=client
LocalIP is provided by VPN provider (e.g. AzireVPN, Mullvad) or your VPS.
default route will redirect your all internet traffic to VPN server.
policy work like Policy Rules (strict) on Merlin.
wgdns is option to change dns server.
Nipset is the name of ipset for ipset based policy routing.
AzireVPN, Mullvad, IVPN, TorGuard support WireGuard servers.
AzireVPN https://www.azirevpn.com/cfg/wg
Mullvad https://mullvad.net/en/servers/#wireguard
IVPN https://www.ivpn.net/wireguard
TorGuard https://torguard.net/knowledgebase.php?action=displayarticle&id=250
nano /opt/etc/wireguard/wg0.conf (example of AzireVPN)
AzireVPN's config file looks like above one.
Fill the Address 10.40.12.49 at LocalIP of init file.
And comment out Address and DNS in the config file.
Then config file should looks like this. (I highly recommend you add keepalive.)
Done. Start WireGuard.
3. Advanced client settings.
For using Route=policy, wg-policy script has some rules.
Adjust to your situation.
Default table is 117.
nano /opt/etc/wireguard/wg-policy
4. as Server configuration setting.
nano /opt/etc/init.d/S50wireguard (example)
nano /opt/etc/wireguard/wg1.conf (Server uses wg1)
Done. Start WireGuard.
4.5 Generate client QRcode.
Generator script will generate QRcode image for Android or iOS.
You need to install qrencode first.
If you want to use your host address (192.168.50.1) as DNS server,
you have to add wg interface to Dnsmasq listening interface list.
This script will ask you 3 options.
1. client name 2. client address 3. client DNS server
-------------------------------------------------------------------------
WireGuard use iptables so when the firewall is restarted, the rules will gone.
Please add this in nat-start script.
nano /jffs/scripts/nat-start
5. Remove WireGuard
Scripts are not beautiful. They just work. Sorry, this is my best.
They have some rules to prevent duplicate.
The error messages (e.g. iptables) are not real error.
Don't worry.
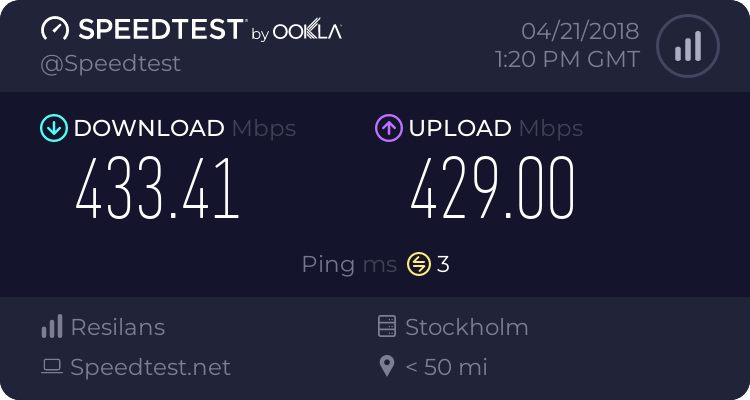
Edit: iperf benchmark result.
WireGuard server on RT-AC86U. Windows 10 Tunsafe client. (https://tunsafe.com/download)
WireGuard author does not assure Tunsafe security. I just used it for benchmark purpose.
You need Entware-aarch64-3.10 to use wireguard without a new firmware build.
ㅡ Kernel Module ㅡ
RT-AC86U, GT-AC2900 - 4.1.27
Code:
opkg install /path/wireguard-kernel_1.0.20210219-k27_1_aarch64-3.10.ipkRT-AX88U, GT-AX11000 - 4.1.51
Code:
opkg install /path/wireguard-kernel_1.0.20210219-k51_1_aarch64-3.10.ipkRT-AX68U, RT-AX86U - 4.1.52
Code:
opkg install /path/wireguard-kernel_1.0.20210219-k52_1_aarch64-3.10.ipkㅡ User space tool ㅡ
Code:
opkg install /path/wireguard-tools_1.0.20210315-1_aarch64-3.10.ipk
cp /opt/etc/wireguard/S50wireguard /opt/etc/init.d2. as Client configuration setting.
nano /opt/etc/init.d/S50wireguard
Code:
Mode=client
export LocalIP=
Route=default #default or policy
export wgdns=
export Nipset=wgvpnInit file has 5 options.
Mode=client
LocalIP is provided by VPN provider (e.g. AzireVPN, Mullvad) or your VPS.
default route will redirect your all internet traffic to VPN server.
policy work like Policy Rules (strict) on Merlin.
wgdns is option to change dns server.
Nipset is the name of ipset for ipset based policy routing.
AzireVPN, Mullvad, IVPN, TorGuard support WireGuard servers.
AzireVPN https://www.azirevpn.com/cfg/wg
Mullvad https://mullvad.net/en/servers/#wireguard
IVPN https://www.ivpn.net/wireguard
TorGuard https://torguard.net/knowledgebase.php?action=displayarticle&id=250
nano /opt/etc/wireguard/wg0.conf (example of AzireVPN)
Code:
[Interface]
PrivateKey = -------
Address = 10.40.12.49/19
DNS = 192.211.0.2
[Peer]
PublicKey = ----------
AllowedIPs = 0.0.0.0/0
Endpoint = IP:PORTAzireVPN's config file looks like above one.
Fill the Address 10.40.12.49 at LocalIP of init file.
Code:
export LocalIP=10.40.12.49 (without prefix)
export wgdns=192.211.0.2And comment out Address and DNS in the config file.
Then config file should looks like this. (I highly recommend you add keepalive.)
Code:
[Interface]
PrivateKey = -------
#Address = 10.40.12.49/19
#DNS = 192.211.0.2
[Peer]
PublicKey = -------
AllowedIPs = 0.0.0.0/0
Endpoint = IP:PORT
PersistentKeepalive = 25Done. Start WireGuard.
Code:
/opt/etc/init.d/S50wireguard start3. Advanced client settings.
For using Route=policy, wg-policy script has some rules.
Adjust to your situation.
Default table is 117.
nano /opt/etc/wireguard/wg-policy
Code:
#
##For ipset based Policy Routing
#
#ipset -N $Nipset hash:ip
#ip rule del prio 9997 2>/dev/null
#ip rule add fwmark 0x7000 table 117 prio 9997
#iptables -t mangle -D PREROUTING -m set --match-set $Nipset dst -j MARK --set-mark 0x7000/0x7000 2>/dev/null
#iptables -t mangle -A PREROUTING -m set --match-set $Nipset dst -j MARK --set-mark 0x7000/0x7000
#service restart_dnsmasq4. as Server configuration setting.
Code:
(umask 077 && printf "[Interface]\nPrivateKey = " | tee /opt/etc/wireguard/wg1.conf > /dev/null)
wg genkey | tee -a /opt/etc/wireguard/wg1.conf | wg pubkey | tee /opt/etc/wireguard/server-publickeynano /opt/etc/init.d/S50wireguard (example)
Code:
Mode=server
export Subnet=10.50.50.1/24 #e.g.)10.50.50.1/24
export wgport=51820nano /opt/etc/wireguard/wg1.conf (Server uses wg1)
Code:
[Interface]
PrivateKey = ----------
ListenPort = 51820
[Peer]
PublicKey = ----------
AllowedIPs = 10.50.50.2/32Done. Start WireGuard.
Code:
/opt/etc/init.d/S50wireguard start4.5 Generate client QRcode.
Generator script will generate QRcode image for Android or iOS.
You need to install qrencode first.
Code:
opkg install qrencodeIf you want to use your host address (192.168.50.1) as DNS server,
you have to add wg interface to Dnsmasq listening interface list.
Code:
sed -i '1s/^/interface=wg* \n/' /jffs/configs/dnsmasq.conf.add
service restart_dnsmasqThis script will ask you 3 options.
1. client name 2. client address 3. client DNS server
-------------------------------------------------------------------------
WireGuard use iptables so when the firewall is restarted, the rules will gone.
Please add this in nat-start script.
nano /jffs/scripts/nat-start
Code:
#!/bin/sh
WVPNROUTE=`ip route show | grep -i -a "dev wg"`
logger -s -t "($(basename $0))" $$ "Checking if WireGuard is UP...."$WVPNROUTE
if [ "$WVPNROUTE" != "" ];then
logger -s -t "($(basename $0))" $$ "**Warning WireGuard is UP.... restarting WireGuard"
/opt/etc/init.d/S50wireguard restart
fi5. Remove WireGuard
Code:
/opt/etc/init.d/S50wireguard stop
opkg remove wireguard-kernel wireguard-tools
rm -r /opt/etc/wireguard
rm /opt/etc/init.d/S50wireguardScripts are not beautiful. They just work. Sorry, this is my best.
They have some rules to prevent duplicate.
The error messages (e.g. iptables) are not real error.
Don't worry.
Edit: iperf benchmark result.
WireGuard server on RT-AC86U. Windows 10 Tunsafe client. (https://tunsafe.com/download)
WireGuard author does not assure Tunsafe security. I just used it for benchmark purpose.
C:\iperf-2.0.9-win64>iperf -c 192.168.50.246 -N -M 1400 -t 20 -w 2M -P 5
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
------------------------------------------------------------
Client connecting to 192.168.50.246, TCP port 5001
TCP window size: 2.00 MByte
------------------------------------------------------------
[ 5] local 10.50.50.2 port 1911 connected with 192.168.50.246 port 5001
[ 7] local 10.50.50.2 port 1913 connected with 192.168.50.246 port 5001
[ 4] local 10.50.50.2 port 1910 connected with 192.168.50.246 port 5001
[ 6] local 10.50.50.2 port 1912 connected with 192.168.50.246 port 5001
[ 3] local 10.50.50.2 port 1909 connected with 192.168.50.246 port 5001
[ ID] Interval Transfer Bandwidth
[ 5] 0.0-20.0 sec 220 MBytes 92.4 Mbits/sec
[ 7] 0.0-20.0 sec 205 MBytes 86.1 Mbits/sec
[ 4] 0.0-20.1 sec 230 MBytes 96.1 Mbits/sec
[ 6] 0.0-20.0 sec 227 MBytes 95.2 Mbits/sec
[ 3] 0.0-20.0 sec 212 MBytes 89.1 Mbits/sec
[SUM] 0.0-20.1 sec 1.07 GBytes 457 Mbits/sec
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
WARNING: attempt to set TCP maximum segment size to 1400, but got 1281
------------------------------------------------------------
Client connecting to 192.168.50.246, TCP port 5001
TCP window size: 2.00 MByte
------------------------------------------------------------
[ 5] local 10.50.50.2 port 1911 connected with 192.168.50.246 port 5001
[ 7] local 10.50.50.2 port 1913 connected with 192.168.50.246 port 5001
[ 4] local 10.50.50.2 port 1910 connected with 192.168.50.246 port 5001
[ 6] local 10.50.50.2 port 1912 connected with 192.168.50.246 port 5001
[ 3] local 10.50.50.2 port 1909 connected with 192.168.50.246 port 5001
[ ID] Interval Transfer Bandwidth
[ 5] 0.0-20.0 sec 220 MBytes 92.4 Mbits/sec
[ 7] 0.0-20.0 sec 205 MBytes 86.1 Mbits/sec
[ 4] 0.0-20.1 sec 230 MBytes 96.1 Mbits/sec
[ 6] 0.0-20.0 sec 227 MBytes 95.2 Mbits/sec
[ 3] 0.0-20.0 sec 212 MBytes 89.1 Mbits/sec
[SUM] 0.0-20.1 sec 1.07 GBytes 457 Mbits/sec
Attachments
Last edited: