adid
New Around Here
Hi,
I have Asus Merlin 384.13 on a RT-AC68U.
My LAN network is 192.168.2.0/24
I have two other networks created by YazFi (192.168.3.0/24 and 192.168.4.0/24) and they are used for VNP.
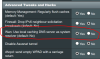
I have installed diversion and I have followed the recommendation from merlin page
to use DNS configuration strict and add a DNS in the settings like
dhcp-option DNS 1.1.1.1 (in fact I used my VPN's DNS servers instead of 1.1.1.1).
All works well and ads are blocked for both VPN and non-vpn clients but there is an issue.
The non-VPN clients with the above configuration, they get as DNS the VPN DNS when I test the ip and DNS server.
I tried to switch to 1.1.1.1 but again the non-VPN clients get the VPN DNS!
I can not understand how this is possible and I suspect some issue with strict not working correctly?
Generally I wouldn't mind this happening (like the non VPN clients using the VPN DNS) but the issue is that in this case Netflix doesn't work for some reason (all other sites works fine).
Any help would be really appreciated
I have Asus Merlin 384.13 on a RT-AC68U.
My LAN network is 192.168.2.0/24
I have two other networks created by YazFi (192.168.3.0/24 and 192.168.4.0/24) and they are used for VNP.
I have installed diversion and I have followed the recommendation from merlin page
to use DNS configuration strict and add a DNS in the settings like
dhcp-option DNS 1.1.1.1 (in fact I used my VPN's DNS servers instead of 1.1.1.1).
All works well and ads are blocked for both VPN and non-vpn clients but there is an issue.
The non-VPN clients with the above configuration, they get as DNS the VPN DNS when I test the ip and DNS server.
I tried to switch to 1.1.1.1 but again the non-VPN clients get the VPN DNS!
I can not understand how this is possible and I suspect some issue with strict not working correctly?
Generally I wouldn't mind this happening (like the non VPN clients using the VPN DNS) but the issue is that in this case Netflix doesn't work for some reason (all other sites works fine).
Any help would be really appreciated