ragnaroknroll
Regular Contributor
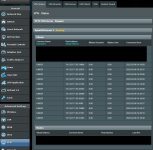
I'm running an OpenVPN server on my Asus RT-AC86U router running Merlin v386.4. Just a short while ago, I observed a large number of connections with UNDEF common name in the VPN Status page of my GUI. Screenshot is attached. I think I just happened to open this status page in the middle of some kind of attack. The log files I pulled up from /jffs/syslog and /jffs/syslog-1 appear to be full of (hopefully) failed attempts. These log files only cover the last hour though, and I can't seem to be able to find the log files from earlier. I'm freaking out a bit at the moment. Could anyone please help me understand if I've been hacked? Anything I can do to protect myself?