You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
leak vpn with 386.5
- Thread starter AsusRog
- Start date
already published in englishNo hablo espanol aqui.
dave14305
Part of the Furniture
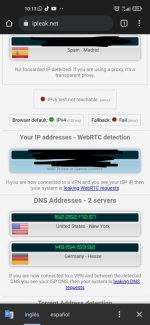
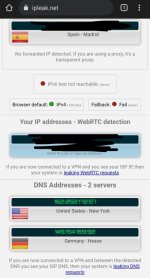
Both IPs belong to Surfshark VPN.
Both IPs belong to Surfshark VPN.
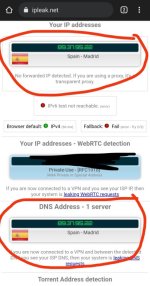
yes correct but it should give the same ip above it should be like this photo which is also from surfshark but the difference is that 386.3.2 directs traffic to the same ip Spain and in 386.5 it sends ip to another location that is a leakBoth IPs belong to Surfshark VPN.
Attachments
eibgrad
Part of the Furniture
Hard to be sure without having details about the OP's DNS and VPN configuration, but one difference between 386.4 and beyond, compare to everything prior to 386.4, is that ASUS now statically binds your DNS as defined on the WAN, to the WAN! And that could result in DNS leaks given certain DNS and VPN configuration settings. But it's impossible to know without having all those other details.
Also, considering using my DNS leak testing tool.

 www.snbforums.com
www.snbforums.com
As I explain in that link, trying to assess the results of DNS leak testing tools *outside* your own environment can be very difficult. At the very least, you should now what's happening *within* the confines of your router first, since that's the one thing you can control. Worry about what these online DNS leak testing tools are telling you later (many times they are just plain wrong).
Also, considering using my DNS leak testing tool.

Tutorial - How to monitor DNS traffic in real-time
Been following this thread. I recall many questions about leaving DNS Server 1/DNS Server 2 blank was answered moons ago. @RMerlin 's guidance was: "do not leave'm blank or NTP and other time dependent services (VPNs, ...) cannot start properly." What did I miss? We are concerned that the...
As I explain in that link, trying to assess the results of DNS leak testing tools *outside* your own environment can be very difficult. At the very least, you should now what's happening *within* the confines of your router first, since that's the one thing you can control. Worry about what these online DNS leak testing tools are telling you later (many times they are just plain wrong).
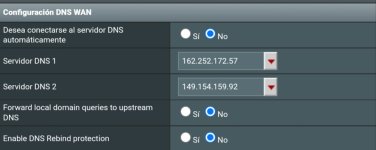
I send you how I have configured the dns in wan and lan look like this I have it and in 386.3.2 there is no problem and in 386.4 onwards something changes in the asus merlin source code.Hard to be sure without having details about the OP's DNS and VPN configuration, but one difference between 386.4 and beyond, compare to everything prior to 386.4, is that ASUS now statically binds your DNS as defined on the WAN, to the WAN! And that could result in DNS leaks given certain DNS and VPN configuration settings. But it's impossible to know without having all those other details.
Also, considering using my DNS leak testing tool.

Tutorial - How to monitor DNS traffic in real-time
Been following this thread. I recall many questions about leaving DNS Server 1/DNS Server 2 blank was answered moons ago. @RMerlin 's guidance was: "do not leave'm blank or NTP and other time dependent services (VPNs, ...) cannot start properly." What did I miss? We are concerned that the...www.snbforums.com
As I explain in that link, trying to assess the results of DNS leak testing tools *outside* your own environment can be very difficult. At the very least, you should now what's happening *within* the confines of your router first, since that's the one thing you can control. Worry about what these online DNS leak testing tools are telling you later (many times they are just plain wrong).
Attachments
eibgrad
Part of the Furniture
I send you how I have configured the dns in wan and lan look like this I have it and in 386.3.2 there is no problem and in 386.4 onwards something changes in the asus merlin source code.
As I said, NOW ASUS is statically binding whatever DNS you have defined on the WAN, to the WAN! And that has the potential to lead to DNS leaks. But I can only say *potential* at this point since I have NO IDEA how you configured DNS wrt your OpenVPN client!
IOW, we can't just look at the tiny bit of information you've provided and draw any hard conclusions as to why these online DNS leak testing tools are reporting a problem. We have to see how you configured the OpenVPN, esp. the "Accept DNS Configuration" option.
Did you follow a specific set of instructions from SurfShark? Do you have the link?
Yes, to the letter, I configured everything correctly and that is why when I am in version 386.3.2 everything is correct and when with the same configuration it goes to version 386.5 there is already a leak""" that you need to find one solution?As I said, NOW ASUS is statically binding whatever DNS you have defined on the WAN, to the WAN! And that has the potential to lead to DNS leaks. But I can only say *potential* at this point since I have NO IDEA how you configured DNS wrt your OpenVPN client!
IOW, we can't just look at the tiny bit of information you've provided and draw any hard conclusions as to why these online DNS leak testing tools are reporting a problem. We have to see how you configured the OpenVPN, esp. the "Accept DNS Configuration" option.
Did you follow a specific set of instructions from SurfShark? Do you have the link?
eibgrad
Part of the Furniture
Yes, to the letter, I configured everything correctly and that is why when I am in version 386.3.2 everything is correct and when with the same configuration it goes to version 386.5 there is already a leak""" that you need to find one solution?
I will assume you used the following link when configuring SurfShark.
I don't see anywhere where it tells you to assign those (apparently) SurfShark DNS servers to the WAN. But we'll put that aside for the moment.
As I keep saying, since 386.4, those DNS servers will be *BOUND TO THE WAN*! So that's something NEW you have to take into consideration that wasn't a problem before.
Are you presently using the VPN Director to manage access to the OpenVPN client?
I configured as indicated by a surfshark agent, he said he should use his dns in the wan and lan. that asus change only affects asus merlin for example the gs-ax3000 router with vpn fusion this error does not occur. if i use vpn managerI will assume you used the following link when configuring SurfShark.
I don't see anywhere where it tells you to assign those (apparently) SurfShark DNS servers to the WAN. But we'll put that aside for the moment.
As I keep saying, since 386.4, those DNS servers will be *BOUND TO THE WAN*! So that's something NEW you have to take into consideration that wasn't a problem before.
Are you presently using the VPN Director to manage access to the OpenVPN client?
eibgrad
Part of the Furniture
P.S. I should make clear that *I* consider it a DNS leak if your preferred DNS servers are accessed over the WAN. IOW, it's NOT enough (imo) to just avoid using the ISP's DNS servers. If you use alternative DNS servers from the VPN provider, but they are accessed over the WAN rather than the VPN, then the ISP can still eavesdrop on your DNS traffic, or worse, hijack it back to his own DNS servers. That's why I keep harping on this issue of the WAN DNS servers being statically bound to the WAN.
I already found the problem now in wan you cannot use manual dns you have to leave it in automatic at last.P.S. I should make clear that *I* consider it a DNS leak if your preferred DNS servers are accessed over the WAN. IOW, it's NOT enough (imo) to just avoid using the ISP's DNS servers. If you use alternative DNS servers from the VPN provider, but they are accessed over the WAN rather than the VPN, then the ISP can still eavesdrop on your DNS traffic, or worse, hijack it back to his own DNS servers. That's why I keep harping on this issue of the WAN DNS servers being statically bound to the WAN.
eibgrad
Part of the Furniture
I configured as indicated by a surfshark agent, he said he should use his dns in the wan and lan. that asus change only affects asus merlin for example the gs-ax3000 router with vpn fusion this error does not occur. if i use vpn manager
You're in the Merlin forum, so presumably using Merlin firmware. AFAIK, *all* routers supporting Merlin have this change that binds the DNS servers defined on the WAN to the WAN, including my own ASUS RT-AC68U.
Code:
admin@lab-merlin1:/tmp/home/root# ip route
1.0.0.1 via 192.168.63.1 dev eth0 metric 1
1.1.1.1 via 192.168.63.1 dev eth0 metric 1
192.168.63.1 dev eth0 proto kernel scope link
192.168.4.0/24 dev wl0.3 proto kernel scope link src 192.168.4.1
10.8.0.0/24 dev tun21 proto kernel scope link src 10.8.0.1
192.168.1.0/24 dev br0 proto kernel scope link src 192.168.1.1
192.168.63.0/24 dev eth0 proto kernel scope link src 192.168.63.102
192.168.61.0/24 via 192.168.63.1 dev eth0 metric 1
127.0.0.0/8 dev lo scope link
default via 192.168.63.1 dev eth0In the above, 1.1.1.1 and 1.0.0.1 are my DNS servers defined on the WAN. Those have been statically bound to the WAN (eth0)!
eibgrad
Part of the Furniture
I already found the problem now in wan you cannot use manual dns you have to leave it in automatic at last.
Yes, because that way those Surfshark DNS servers are no longer statically bound to the WAN. Instead, you're using the ISP's DNS servers, and now they become bound to the WAN.
Even so, the use of Strict for "Accept DNS Configuration" does NOT guarantee against DNS leaks. The Strict option combines the ISP's (WAN's) DNS servers w/ those of the VPN, and only gives *priority* to the VPN provider's DNS servers. Given enough activity, eventually you'll find the ISP's DNS servers being used by DNSMasq from time to time (something my DNS utility would expose), and thus a DNS leak.
You didn't need to worry about this before since you only made Surfshark's DNS servers available, be it the WAN or VPN.
The only thing that guarantees against a DNS leak is Exclusive. But that comes w/ its own limitations (at least when using the VPN Director). It bypasses DNSMasq, so you lose access to local name resolution, caching, ad blocking, etc., at least for those WLAN/LAN clients bound to the VPN.
If it wasn't obvious before, it should be now ... DNS is complicated business.
Last edited:
Asus Rog,
Here's mine for Surfshark....I have no leaks.
WAN DNS Setting
Connect to DNS Server automatically Yes
Forward local domain queries to upstream DNS No
LAN DHCP SERVER
DNS and WINS Server Setting
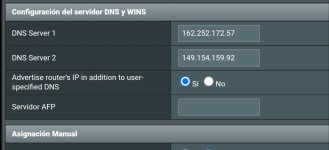
DNS Server 1 162.252.172.57
DNS Server 2 149.154.159.92
Network Settings (Under VPN CLIENT)
Interface Type TUN
Protocol UDP
Server Address and Port WHATEVER SERVER YOU WANT Address: Port: 1194
Create NAT on tunnel Yes
Inbound Firewall Block
Accept DNS Configuration EXCLUSIVE
Redirect Internet traffic through tunnel Yes(all)
Killswitch - Block routed clients if tunnel goes down Yes or No (Your choice)
Here's mine for Surfshark....I have no leaks.
WAN DNS Setting
Connect to DNS Server automatically Yes
Forward local domain queries to upstream DNS No
LAN DHCP SERVER
DNS and WINS Server Setting
DNS Server 1 162.252.172.57
DNS Server 2 149.154.159.92
Network Settings (Under VPN CLIENT)
Interface Type TUN
Protocol UDP
Server Address and Port WHATEVER SERVER YOU WANT Address: Port: 1194
Create NAT on tunnel Yes
Inbound Firewall Block
Accept DNS Configuration EXCLUSIVE
Redirect Internet traffic through tunnel Yes(all)
Killswitch - Block routed clients if tunnel goes down Yes or No (Your choice)
Similar threads
- Replies
- 5
- Views
- 578
- Replies
- 7
- Views
- 306
- Replies
- 5
- Views
- 379
Similar threads
Similar threads
-
-
-
Assigned IP address to the WAN interface via VPN director: no internet connection - why?
- Started by OB1
- Replies: 1
-
-
-
-
-
-
Two VPN connections from home network at the same time -> problems
- Started by vrapp
- Replies: 6
-
Latest threads
-
Release ASUS RT-AC68U Firmware version 3.0.0.4.386_51685 (2024/04/15)
- Started by Intrepid
- Replies: 5
-
RT-AX86U - Find Which Device is Connected to Which LAN Port
- Started by dsneed
- Replies: 2
-
-
CVE-2024-31497: PuTTY vulnerability vuln-p521-bias
- Started by XIII
- Replies: 1
-
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!