sinshiva
Very Senior Member
Hi all,
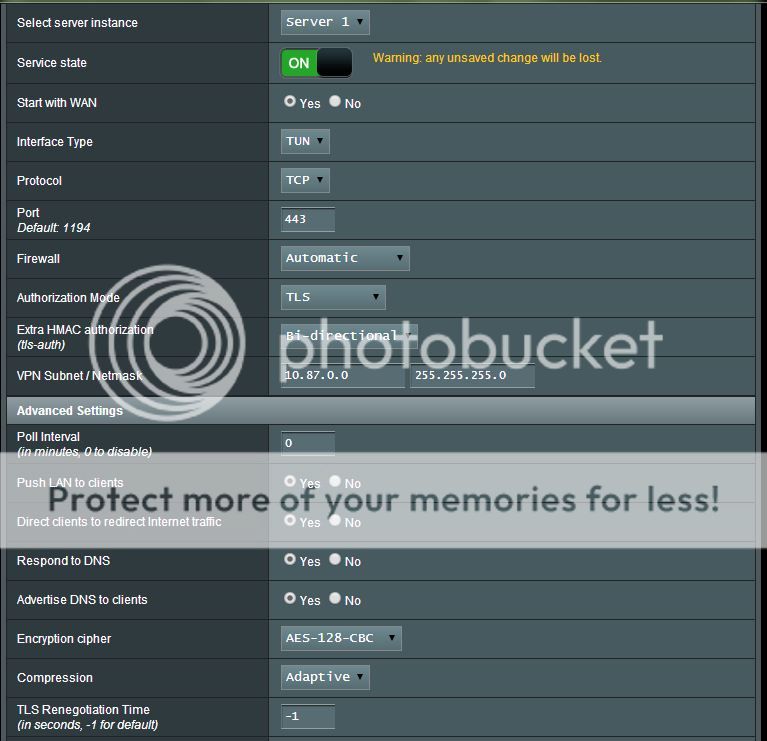
Been playing with my RT-N66R. So, i got OpenVPN working for the first time. Always had trouble getting things to accept certificates before and ended up blowing it off.
Anyway, i did lots of testing of the performance variety. I am running the service on 443/tcp. So for my tests, i'm possibly losing out on any benefits offered for UDP streams.
The final result is thus;
4096bit RSA keys (should be strong enough?)
6144bit DH 'modulus'
192bit AES CBC
with the below added to the 'Custom configuration' field.
For the 4096bit RSA keys, this is good enough? For the Diffie Hellman modulus, i started out low and worked up to generating this 8192bit modulus (single core (can this be multithreaded for a single modulus?), about 6 hours on an Athlon 2 x4 645), obviously now free to the public domain.
Unfortunately, this was too slow/whatever for the router, i think. nothing would handshake, just time out. I generated a 6144bit DH mod and while a little slow handshaking, once connected everything operates very quick.
I ended up with using the cipher aes-192-cbc because on my single core devices, i saw great bandwidth improvements testing over my wifi compared to 256bit, and according to this guy, it looks like it would require a 16384-bit DH mod for aes-256-cbc.
Sorry for the lack of pretty graphics, but my primary method of testing was using a netbook with a single core hyperthreaded Atom processor (running winxp) and a 1ghz single core Android phone. Only the Android was connected over wifi and bandwidth was tested using the Speed Test application by ping-test.net with 10mbit/768kbit DSL.
My vpn throughput over both devices was higher with aes-192-cbc than aes-256-cbc and bf-cbc. At less than half wifi strength, i was getting 1-3mbit with bf-cbc, 1-2mbit with aes-256-cbc, but with aes-192-cbc, i am getting 7-8mbit.
Anyway, remember, this all was with using the RT-N66R for my OpenVPN server.
comments appreciated
Been playing with my RT-N66R. So, i got OpenVPN working for the first time. Always had trouble getting things to accept certificates before and ended up blowing it off.
Anyway, i did lots of testing of the performance variety. I am running the service on 443/tcp. So for my tests, i'm possibly losing out on any benefits offered for UDP streams.
The final result is thus;
4096bit RSA keys (should be strong enough?)
6144bit DH 'modulus'
192bit AES CBC
with the below added to the 'Custom configuration' field.
Code:
tls-cipher DHE-RSA-AES256-SHA //this whole field is outdated, read on
auth sha512For the 4096bit RSA keys, this is good enough? For the Diffie Hellman modulus, i started out low and worked up to generating this 8192bit modulus (single core (can this be multithreaded for a single modulus?), about 6 hours on an Athlon 2 x4 645), obviously now free to the public domain.
Code:
-----BEGIN DH PARAMETERS-----
MIIECAKCBAEA7Qk27H7hBvDdQESs+CDS5OKNqxjovkTgFmgPKX/jYBeqn1m+IF/z
yF85kU0VIMqR1W9xLGsCbUdQmZ110IXKzizjIGwTmEetoGfOFZp6cCyEcRuokt1H
9fk+KFw989L49PMa8Y4bK+LQlsWLmFZnWNtzRGQmX9xMSJi9ae3hHJIhD3mTLWQd
p2VYLOlpzySsxXKMlq4NZrqCJ+5b3HpqD90MWgL0f1Dn+wnL3/bqvrtSsNeICxZw
GBuXal2bfCrUZUrrskbdwReS9isrrW06oyjd8/0nnK/ryP+LdKTlY5Vokr8ncqia
7hxtUm1A1myZJqd4JJ2rJVJsuKIbgqKIKtukcSvqjDvxLpINNuke7WwA8OEPDOAq
T33cj5e6AUHwErFemFE7mLZb40XFppcBTluRxOtCBDUHE3IJitmbNWF85nOc5uK7
VNL1upx7rnwT94qcRNLyUzIT+3F/Gw5YR8lRryyaEjFoRlWkFVz3yO5VXluZeAsz
dYjkSrLi5eUHYBdUpRWraSSr6l6YTZjdxp4UUWwB/ulxA9Lneij+YJmdsThneQkp
2mmh7bxVi04uvzmrl6Mye3rUz0D9v7z6xIAz9IzTtRhrC2r5agQuyS16B17LvgwM
OMNecsuiscWARmN6HOouTqSz6+S5HPBBn6p0a177Ye0woKNTfzmdZsZDPcRad1R0
SUKLsWbtKcCODcY/LCisjfscrqM7uS3UZL26bDcYO4+GD3RgDo6unfFRlsB7UBSc
/aatIV3BuOJfCiBROAt6utAZscSi+5eby9+JPIDaAED0IOISgA6AKxbQdo8fjMxa
q9Wpp23kqQdpBKEO4tKOi+3yZc/8P3dHUXtOiSZzESB0WNG3yx2gGWd4+6DWCN2g
+QnBDzS0cHLihwUudcezbh1AinGaa0Eg8W+m0JyOQDgphVHaxYpf+9Gi7lDQZfqN
vPIFxeRsOv9B06YK/LweqaqafvF9yS4i9jZF7QfWA3JBswzl9Olh4CEzRUQw1Rw+
giSnu5hHKkk01hS6kJiRskJkHs8+agZe77po9W5+oJo/FViaL4oObpymSjsdz/PI
TYp0d3FqPGlQWCH9W18Rcggl8hCuUVLoh3VAKlpCB2ovS2c6nsiC7vqGZ9GRgO8W
pZWcBMnn2thUtSY0p4mJyeGdBxA+5gKoYvKznNljcpu5f4BgKGCYygrBRix3tEZv
Jcv0H4VoObAE5CjtXt23J/Aj0zKRSCLFX9TyuWVKUOY0YgE7dxt6TKjHCKY2ZYsx
v0NOJRORkuSXkdd2HvPR/WlGvIxSlvCOW/QSCfW4GGusRfQi5Ok9LDe7sVy1oqEK
wuxBCa1HWoDpXarRLtHVVgc1XW3SHVOUQwIBAg==
-----END DH PARAMETERS-----Unfortunately, this was too slow/whatever for the router, i think. nothing would handshake, just time out. I generated a 6144bit DH mod and while a little slow handshaking, once connected everything operates very quick.
I ended up with using the cipher aes-192-cbc because on my single core devices, i saw great bandwidth improvements testing over my wifi compared to 256bit, and according to this guy, it looks like it would require a 16384-bit DH mod for aes-256-cbc.
Sorry for the lack of pretty graphics, but my primary method of testing was using a netbook with a single core hyperthreaded Atom processor (running winxp) and a 1ghz single core Android phone. Only the Android was connected over wifi and bandwidth was tested using the Speed Test application by ping-test.net with 10mbit/768kbit DSL.
My vpn throughput over both devices was higher with aes-192-cbc than aes-256-cbc and bf-cbc. At less than half wifi strength, i was getting 1-3mbit with bf-cbc, 1-2mbit with aes-256-cbc, but with aes-192-cbc, i am getting 7-8mbit.
Anyway, remember, this all was with using the RT-N66R for my OpenVPN server.
comments appreciated
Last edited: