Hi,
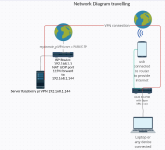
I have a router ASUS RT-A86U running with Asuswrt-Merlin FW 384.19. I have a client OpenVPN connection on my ASUS router so all traffic go through the VPN tunnel to my VPN server (raspberry PI with piVPN)
My setup is quite simple, I always connect my latptop to ASUS router , at home or travelling, so all my traffic always go the the same internet connection point, my VPN server.
At home I have a standard ISP's router, and connected to this ISP's router the VPN server (raspberry PI with piVPN) with ethernet cable. When I'm travelling, router get internet through a 4G-USB modem and at home it's connected to the same ISP's router with ethernet cable.
This setup has work for 2 years without any single issue. Suddendly, at home, 3 days ago OpenVPN client on ASUS wasn't available to connect with VPN server. It stopped working during the night without any update on router ASUS or raspberry server.
After several checks, I realize client connect with server as UNDEF user and logs show handshake problem on both side, so only partial connection established.
If ASUS router is connect at internet with 4G-modem it works perfecty but at home I need to insert private LAN IP address of the server 192.168.1.144 instead mydomain_piVPN.com to be available to connect. Note ISP's router has subnet 192.168.1.xxx and Asus router has subnet 192.168.2.xxx
In the past I remind to see in system register of router: dmask changing mydomain_piVPN.com public IP 213.xxx.xxx.xxx to IP 192.168.1.144, like router realize public IP has an equivalent IP lan, so it use LAN IP private address.
Now when I'm at home I need to enter address of server as 192.168.1.144 and when travelling I need to change address to mydomain_piVPN.com It's not so annoying but what f*** me it's that I don't know what happened and how to fix it.
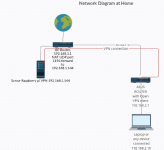
I have a router ASUS RT-A86U running with Asuswrt-Merlin FW 384.19. I have a client OpenVPN connection on my ASUS router so all traffic go through the VPN tunnel to my VPN server (raspberry PI with piVPN)
My setup is quite simple, I always connect my latptop to ASUS router , at home or travelling, so all my traffic always go the the same internet connection point, my VPN server.
At home I have a standard ISP's router, and connected to this ISP's router the VPN server (raspberry PI with piVPN) with ethernet cable. When I'm travelling, router get internet through a 4G-USB modem and at home it's connected to the same ISP's router with ethernet cable.
This setup has work for 2 years without any single issue. Suddendly, at home, 3 days ago OpenVPN client on ASUS wasn't available to connect with VPN server. It stopped working during the night without any update on router ASUS or raspberry server.
After several checks, I realize client connect with server as UNDEF user and logs show handshake problem on both side, so only partial connection established.
If ASUS router is connect at internet with 4G-modem it works perfecty but at home I need to insert private LAN IP address of the server 192.168.1.144 instead mydomain_piVPN.com to be available to connect. Note ISP's router has subnet 192.168.1.xxx and Asus router has subnet 192.168.2.xxx
In the past I remind to see in system register of router: dmask changing mydomain_piVPN.com public IP 213.xxx.xxx.xxx to IP 192.168.1.144, like router realize public IP has an equivalent IP lan, so it use LAN IP private address.
Now when I'm at home I need to enter address of server as 192.168.1.144 and when travelling I need to change address to mydomain_piVPN.com It's not so annoying but what f*** me it's that I don't know what happened and how to fix it.