I want to know how merlin got the dns to work automatically in the openconfig. I had a 86u, setting it up with the openvpn config files was super easy and you would get your ip and dns automatically served from your vpn provider without issues. In the pursuit of performance I switched to a custom box. I have tried both pfsense and untangle with expressvpn and cannot for the life of me get their dns to ever work, I get dns leaks per se. How did you do it?
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
OpenVPN Question
- Thread starter vpn4life
- Start date
john9527
Part of the Furniture
It's handled in one of Merlin's scripts. When I was experimenting with pfsense I tried to port it over, but some of the code wasn't compatible with the FreeBSD shell, and I never got back to it.I have tried both pfsense and untangle with expressvpn and cannot for the life of me get their dns to ever work
It's handled in one of Merlin's scripts. When I was experimenting with pfsense I tried to port it over, but some of the code wasn't compatible with the FreeBSD shell, and I never got back to it.
Is there no workaround? I've messaged expressvpn and they wont give me their dns listening addresses. The only DNS they provide openly is for streaming devices and game consoles. I'm honestly considering dropping express, and thinking of mullvad with wireshark, or protonvpn. To me, a dns leak is a big deal.
st3v3n
Very Senior Member
(L&LD, Magic, indeed. I believe in Magic, as released in '65 by the Lovin Spoonful.
vpn4, you could always try to ask Merlin for the secrets to the magic DNS sauce Rather than messaging Express, you might try to restate your issue to company management. Without a better description of your configuration and systems setup, it's not likely Express is the cause of the DNS leaks you're experiencing. Anything's possible but they'd know if they were leaking. If you're using the Express app or client configs, they'd know if that was causing. Your post opens the deep, dark VPN rabbit-hole.
Rather than messaging Express, you might try to restate your issue to company management. Without a better description of your configuration and systems setup, it's not likely Express is the cause of the DNS leaks you're experiencing. Anything's possible but they'd know if they were leaking. If you're using the Express app or client configs, they'd know if that was causing. Your post opens the deep, dark VPN rabbit-hole.
Most VPNs are sensitive to their customer's issues, but have no control over router, system or device configuration problems which are where most DNS leaks originate (browser also contribute to leaks). VPNs want to protect their company infrastructure and customer's bits and bytes. If a provider mishandles customer's traffic, they'll lose those customers, hardly in their or their customer's best interests. Mitnick wannabes, script kiddies and the ever-growing legions of hostile state hackers and common crooks have always loved misusing the same VPNs everyone else now uses, only they still like paying with stolen financial data, an old story. There aren't as many quality, verifiable domestic VPN providers in free countries as there once were; none exit in Putin's Russia or in their best friends list, nor in red china or other like-minded controlled states, where all VPNs are outlawed. Detection of any attempted use of non-state controlled VPN apps have resulted in quite a few arrests and disappearances.
In many countries state agents present security letters or warrants to a VPN owner, along with an gag order never to reveal their plight. Regardless of countless promises made by all VPNs to their customers, to end or relocate their business rather than compromise customer's privacy, never monitoring traffic, etc, VPNs aren't a silver bullet. No owner will risk immediate arrest and imprisonment, with an indefinite cramped prison lifestyle, camping with a new large, lonely cellmate. Customers may not learn of an incident for many years, if ever. The other VPNs you mention have their fans and a decent reputation. Any service advertising world-wide virtual servers is questionable so perform research before you really leave Express. It's difficult to locate most VPN's CEOs (they like their privacy too, even the legitimate guys), in order to sent them a proper letter to further explain your issues.
Your situation seems complicated, but remain thankful you're not trying to exist in Venezuela. Their electrical grid failed catastrophically two weeks ago with no power, internet or other forms of communications services. No fuel is reaching the population, though a few news outlets are risking their sat-phones driving around to uplink video recorded by non-transmitting smart-phones (no cell service). All their electronics are recharged by their car or a small portable solar panel, and no adequate sanitary conditions exist anywhere. Except for the small amount of food and water the news folk bring in with them for their needs, no food, water, medicine, hospital or other medical services are available. An active war zone elsewhere isn't equal to the instant devastation that a complete power grid collapse brings to an otherwise modern country. An EMP attack as depicted in the novel, 'One Second After' would be the only way short of nuclear war, to send a 21st century country back to the dark ages, with the same amount of anarchy. Not a rant, and best of luck resolving your DNS leaks.
vpn4, you could always try to ask Merlin for the secrets to the magic DNS sauce
Most VPNs are sensitive to their customer's issues, but have no control over router, system or device configuration problems which are where most DNS leaks originate (browser also contribute to leaks). VPNs want to protect their company infrastructure and customer's bits and bytes. If a provider mishandles customer's traffic, they'll lose those customers, hardly in their or their customer's best interests. Mitnick wannabes, script kiddies and the ever-growing legions of hostile state hackers and common crooks have always loved misusing the same VPNs everyone else now uses, only they still like paying with stolen financial data, an old story. There aren't as many quality, verifiable domestic VPN providers in free countries as there once were; none exit in Putin's Russia or in their best friends list, nor in red china or other like-minded controlled states, where all VPNs are outlawed. Detection of any attempted use of non-state controlled VPN apps have resulted in quite a few arrests and disappearances.
In many countries state agents present security letters or warrants to a VPN owner, along with an gag order never to reveal their plight. Regardless of countless promises made by all VPNs to their customers, to end or relocate their business rather than compromise customer's privacy, never monitoring traffic, etc, VPNs aren't a silver bullet. No owner will risk immediate arrest and imprisonment, with an indefinite cramped prison lifestyle, camping with a new large, lonely cellmate. Customers may not learn of an incident for many years, if ever. The other VPNs you mention have their fans and a decent reputation. Any service advertising world-wide virtual servers is questionable so perform research before you really leave Express. It's difficult to locate most VPN's CEOs (they like their privacy too, even the legitimate guys), in order to sent them a proper letter to further explain your issues.
Your situation seems complicated, but remain thankful you're not trying to exist in Venezuela. Their electrical grid failed catastrophically two weeks ago with no power, internet or other forms of communications services. No fuel is reaching the population, though a few news outlets are risking their sat-phones driving around to uplink video recorded by non-transmitting smart-phones (no cell service). All their electronics are recharged by their car or a small portable solar panel, and no adequate sanitary conditions exist anywhere. Except for the small amount of food and water the news folk bring in with them for their needs, no food, water, medicine, hospital or other medical services are available. An active war zone elsewhere isn't equal to the instant devastation that a complete power grid collapse brings to an otherwise modern country. An EMP attack as depicted in the novel, 'One Second After' would be the only way short of nuclear war, to send a 21st century country back to the dark ages, with the same amount of anarchy. Not a rant, and best of luck resolving your DNS leaks.
Last edited:
This is a relatively easy problem to fix. You do not have to use your provider's DNS. You can (should) use dnscrypt or other encrypted DNS options like DNS-over-TLS these days. That will work with any VPN service, ISP or your own VPS.
Trickier problems are things like kill switches or failover ...
Trickier problems are things like kill switches or failover ...
Last edited:
This is a relatively easy problem to fix. You do not have to use your provider's DNS. You can (should) use dnscrypt or other encrypted DNS options like DNS-over-TLS these days. That will work with any VPN service, ISP or your own VPS.
Trickier problems are things like kill switches or failover ...
I understand and had been using DoT with pfsense but switched to untangle and they have yet to support it. I would prefer to use my VPN providers DNS though.
Zonkd
Very Senior Member
I understand and had been using DoT with pfsense but switched to untangle and they have yet to support it. I would prefer to use my VPN providers DNS though.
Please answer questions below and provide more info:
1. You are using DoT? If so then it will circumvent ExpressVPN DNS thus dnsleak would happen.
2. Please use dnsleaktest.com to run an extended test then post your results here.
3. Please use expressvpn dns leak test page and post your full results here.
4. Have you manually configured the DNS servers on the device network settings? If so, to what?
5. How many different ways have you tried to observe and confirm dns leakage is actually happening? Have you tried inspecting dns traffic with Diversion by following the dnsmasq logs? Or in other words, have you used any form of network packet sniffing using a device not connected to vpn?
Source --- https://www.expressvpn.com/dns-leak-test
DNS leaks can happen for many reasons. Here are just a few:
- Your VPN is manually configured. If you’re manually configuring a VPN connection, the risk of DNS leaks is higher and depends on your exact operating system configuration. Using the ExpressVPN apps will eliminate many of these risks.
- An attacker controls your router, such as a malicious Wi-Fi operator at a coffee shop. An attacker may be able to trick your device into sending DNS traffic outside of the VPN tunnel. ExpressVPN apps offer DNS leak protection, but other apps and manual configurations might be vulnerable.
- Manual DNS setup. You (or software on your device) specifically told the operating system not to use DNS servers operated by ExpressVPN. Power users might require a particular DNS service, but for security reasons, it’s probably undesired for most people.
Some personal notes from my research:
ExpressVPN website claims they run their own DNS servers, however I'm unsure whether these are recursive dns servers or if these are fowarding dns servers. You can learn more about recursive servers here. Recursive causes only the vpn operated dns servers to appear in dnsleaktest results. You can test this using the IVPN public recursive DNS server. Forwarding on the other hand may cause all the upstream dns servers operated by third parties (eg google, opendns, cloudflare) to appear in dnsleaktest results. An example of this happening can be seen when using AdguardDNS, which uses forwarding, and someone raised this exact concern on their forums. The important thing to note is that so long as the dns queries are always sent through the vpn tunnel they will be encrypted and appear as originating from the IP address from your VPN provider and not attributable to your actual IP address. It's inevitable that your dns queries will be sent to an authoratative dns server not operated by your vpn.
No accusations but could ExpressVPN be using transparent DNS proxy to redirect customers dns queries to their own dns servers? I notice they have no public dns server to provide an IP for, I don't think they have a static IP to provide for all their internal dns server/s, and their support docs -- setup dns servers for dd-wrt routers (quoted below) --- advises customers to manually set the Google DNS servers (with a permanent IP address of 8.8.8.8 and 8.8.4.4) or Neustar or Level3, with no other option given for customers to choose expressvpn operated dns servers. Ofcourse if they were proxying dns queries anyway then it wouldn't matter what the customer set. That would be easier and more flexible for them, and better for the customer because dns wouldn't break when the customer stopped using their vpn.
Source --- https://www.expressvpn.com/support/troubleshooting/set-dns-servers-for-dd-wrt/
To manually configure your router with ExpressVPN’s DNS servers’ addresses, in DD-WRT:
On the Setup tab under Network Address Server Settings (DHCP), look for Static DNS 1 and Static DNS 2.Click Apply Settings.
If Google DNS is blocked for you, please try:
- Set Static DNS 1 to: 8.8.8.8
- Set Static DNS 2 to: 8.8.4.4
- Neustar DNS Advantage (156.154.70.1 and 156.154.71.1),
- Level3 DNS (4.2.2.1 and 4.2.2.2)
See below screenshot for reference:
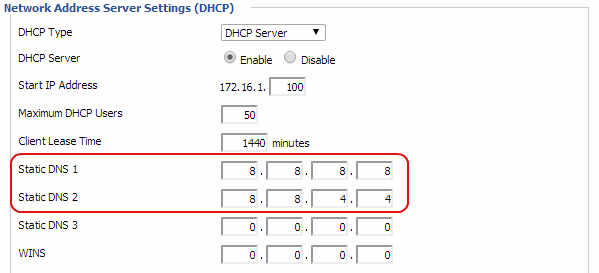
Last edited:
I figured it out, someone sent me an article that helped immensely but I still spent a few hours ironing some things out. Documentation is piss poor when it comes to vpn client setups on pfsense. I plan to make some videos detailing how to do it correctly.
https://imgur.com/a/AAk1MQV
https://imgur.com/a/jNqLVP9

https://imgur.com/a/AAk1MQV
https://imgur.com/a/jNqLVP9

Last edited:
Xentrk
Part of the Furniture
The OpenVPN Client setup document that TorGuard has is also out of date. I emailed them about it nearly two years ago and it's still has not been updated. After I finish my current project on Asuswrt-Merlin, I plan to shift gears to pfSense how-to articles, including how to setup OpenVPN client and selective routing. But over the past 1.5 years, there have been some new blog posts on how to set up pfSense. Lawrence Systems has some great YouTube videos on pfSense that have helped me setup snort and other features. I highly recommend the videos. Check them out.I figured it out, someone sent me an article that helped immensely but I still spent a few hours ironing some things out. Documentation is piss poor when it comes to vpn client setups on pfsense. I plan to make some videos detailing how to do it correctly.
Here are some other links:
https://nguvu.org/pfsense/pfsense-baseline-setup/
https://turbofuture.com/computers/How-to-Install-pfSense-From-a-Bootable-USB-Stick
https://www.techhelpguides.com/2017/06/12/ultimate-pfsense-openvpn-guide/
https://www.infotechwerx.com/blog/Policy-Routing-Certain-Traffic-Through-OpenVPN-Client-Connection
https://www.linuxincluded.com/block-ads-malvertising-on-pfsense-using-pfblockerng-dnsbl/
http://supratim-sanyal.blogspot.com/2017/04/pfsense-pfblockerng-ultimate-list-of-ip.html
https://nguvu.org/pfsense/pfsense-baseline-setup/
Marin
Very Senior Member
The OpenVPN Client setup document that TorGuard has is also out of date. I emailed them about it nearly two years ago and it's still has not been updated. After I finish my current project on Asuswrt-Merlin, I plan to shift gears to pfSense how-to articles, including how to setup OpenVPN client and selective routing. But over the past 1.5 years, there have been some new blog posts on how to set up pfSense. Lawrence Systems has some great YouTube videos on pfSense that have helped me setup snort and other features. I highly recommend the videos. Check them out.
Here are some other links:
https://nguvu.org/pfsense/pfsense-baseline-setup/
https://turbofuture.com/computers/How-to-Install-pfSense-From-a-Bootable-USB-Stick
https://www.techhelpguides.com/2017/06/12/ultimate-pfsense-openvpn-guide/
https://www.infotechwerx.com/blog/Policy-Routing-Certain-Traffic-Through-OpenVPN-Client-Connection
https://www.linuxincluded.com/block-ads-malvertising-on-pfsense-using-pfblockerng-dnsbl/
http://supratim-sanyal.blogspot.com/2017/04/pfsense-pfblockerng-ultimate-list-of-ip.html
https://nguvu.org/pfsense/pfsense-baseline-setup/
I cannot wait to see your pFsense materials and thanks for sharing these!
Sent from my iPhone using Tapatalk
Similar threads
- Replies
- 6
- Views
- 645
- Replies
- 2
- Views
- 578
- Replies
- 1
- Views
- 146
Similar threads
Similar threads
-
-
-
OpenVPN / site to site with special security/routing constraints
- Started by MarkusI
- Replies: 7
-
-
-
-
-
-
-
For AX68U and AX86S Merlin users: openvpn server - max user qty?
- Started by mikepervert
- Replies: 1
Latest threads
-
RT-AX86U - Find Which Device is Connected to Which LAN Port
- Started by dsneed
- Replies: 2
-
-
CVE-2024-31497: PuTTY vulnerability vuln-p521-bias
- Started by XIII
- Replies: 1
-
-
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!

