Dear forum
Hopefully you can help me. This should be so simple but I have been stuck with this for 2 days now.
And I cannot be the one person wanting to do this.
I am running 386.1_2 on RT-AC86U and my goal is to setup 2 OpenVPN servers.
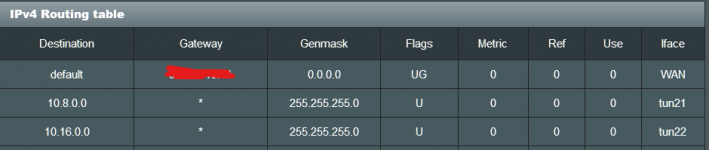
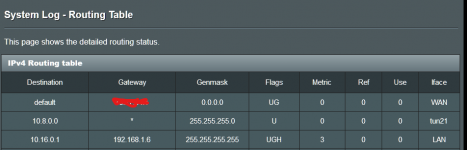
Server1 (ip pool: 10.8.0.0) : access to all LAN (192.168.1.*)
Server2 (ip pool: 10.16.0.0): access to singe static IP in LAN (192.168.1.6)
Both servers work now providing access to all LAN like show in IPv4 routing table.
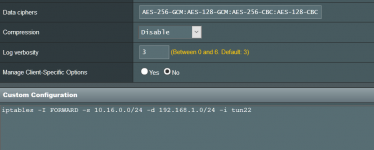
The question is this simple, how do I change the routing so that all traffic from 10.16.0.0 goes to 192.168.1.6?
Thank you for helping a newbie.
Pekka
Hopefully you can help me. This should be so simple but I have been stuck with this for 2 days now.
And I cannot be the one person wanting to do this.
I am running 386.1_2 on RT-AC86U and my goal is to setup 2 OpenVPN servers.
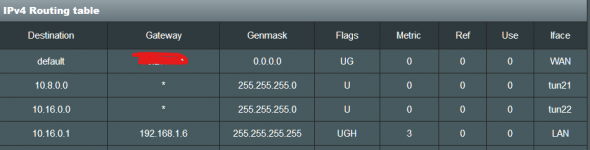
Server1 (ip pool: 10.8.0.0) : access to all LAN (192.168.1.*)
Server2 (ip pool: 10.16.0.0): access to singe static IP in LAN (192.168.1.6)
Both servers work now providing access to all LAN like show in IPv4 routing table.
The question is this simple, how do I change the routing so that all traffic from 10.16.0.0 goes to 192.168.1.6?
Thank you for helping a newbie.
Pekka
Attachments
Last edited: