Alaska99
Occasional Visitor
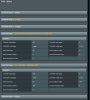
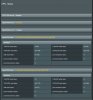
Hello, I use openvpn server to connect my iphone on my asus RT-AC68U and I use client openvpn to connect to my VPN provider.
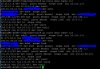
If I use only server or only client all run fine but when server openvpn is connected I can't connet to openvpn client with my iphone... There is special config to be able use client and server together?
I use latest firmware 378.50
Thank you.
If I use only server or only client all run fine but when server openvpn is connected I can't connet to openvpn client with my iphone... There is special config to be able use client and server together?
I use latest firmware 378.50
Thank you.
Last edited: