Router: RT-AX86U
WRT-Merlin: 388.1
VPN-service: Mullvad.net
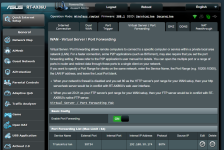
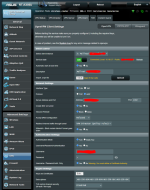
I have set VPN-client configuration for WireGuard in WRT-Merlin and successfully connected. I'm running a Rpi 4 connected through LAN port 3 on the RT-AX86U and the Rpi runs Transmission. Port was showing on Transmission as closed so I then opened port in RT-AX86U and also opened it in Mullvad settings for that connection. Disabling Mullvad made the port open again.
I then switched to OpenVPN-protocol, still Mullvad as provider, and that fixed the problem. The Rpi is behind Mullvad VPN service and the port shows in Transmission as open.
As you can see switching from WireGuard to OpenVPN fixed my problem but I suspect that WRT-Merlin (or ASUS OEM firmware) can't forward ports when using WireGuard from the router.
This post is not really a question as I'm satisfied with using OpenVPN but if for developing/bug searching purposes you need me to post further information or try other things, let me know!
/Proud WRT-Merlin user since 2018
WRT-Merlin: 388.1
VPN-service: Mullvad.net
I have set VPN-client configuration for WireGuard in WRT-Merlin and successfully connected. I'm running a Rpi 4 connected through LAN port 3 on the RT-AX86U and the Rpi runs Transmission. Port was showing on Transmission as closed so I then opened port in RT-AX86U and also opened it in Mullvad settings for that connection. Disabling Mullvad made the port open again.
I then switched to OpenVPN-protocol, still Mullvad as provider, and that fixed the problem. The Rpi is behind Mullvad VPN service and the port shows in Transmission as open.
As you can see switching from WireGuard to OpenVPN fixed my problem but I suspect that WRT-Merlin (or ASUS OEM firmware) can't forward ports when using WireGuard from the router.
This post is not really a question as I'm satisfied with using OpenVPN but if for developing/bug searching purposes you need me to post further information or try other things, let me know!
/Proud WRT-Merlin user since 2018