Rubenel
Occasional Visitor
Hey guys, I'm using my Asus AC68u with 380.69 firmware.
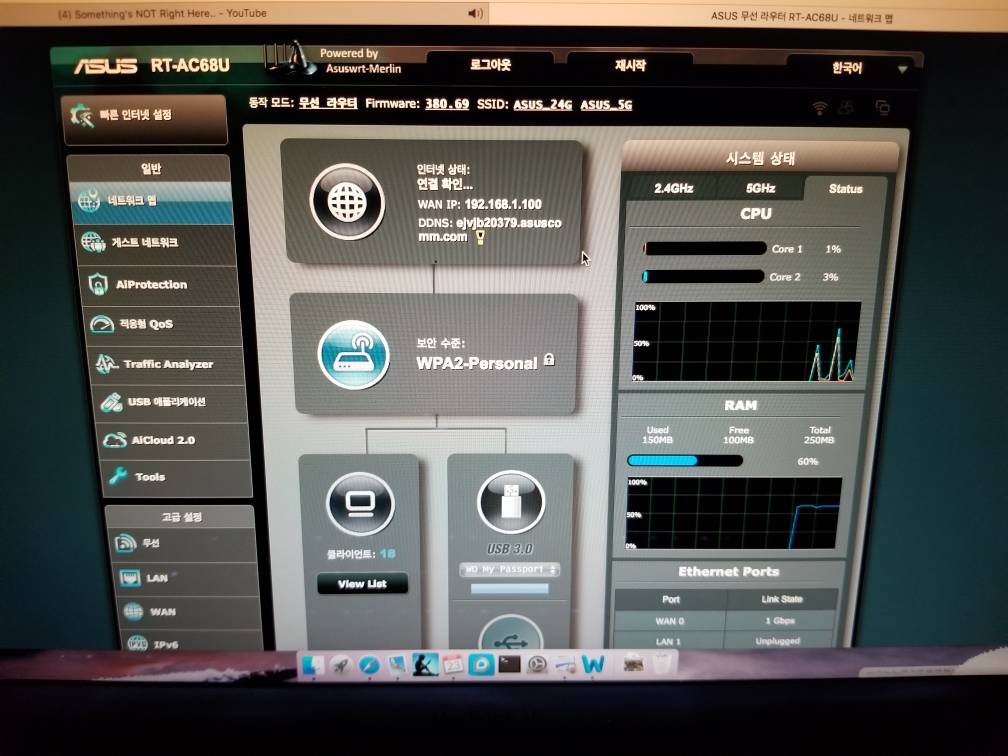
I've logged on today and noticed my language was changed to the Asian region.
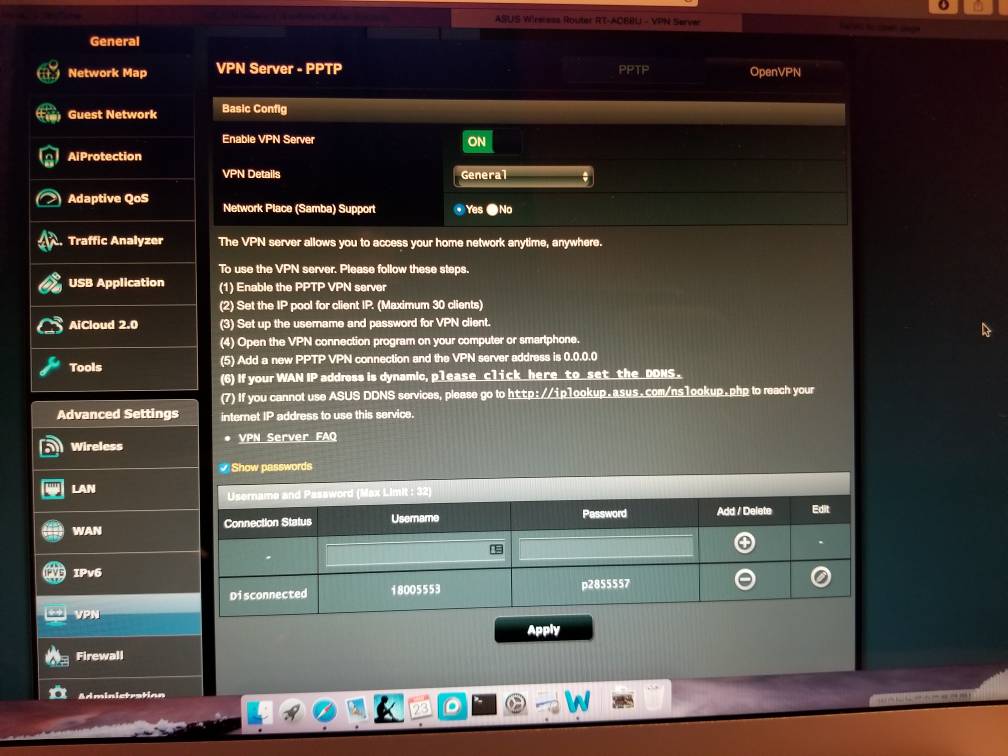
Someone also set up a PPTP and a DDNS.
I have the router offline, but I haven't altered anything.
Can someone assist me. I can send logs and other info to help chase this issue.
Sent from my SM-G950U using Tapatalk
I've logged on today and noticed my language was changed to the Asian region.
Someone also set up a PPTP and a DDNS.
I have the router offline, but I haven't altered anything.
Can someone assist me. I can send logs and other info to help chase this issue.


Sent from my SM-G950U using Tapatalk

