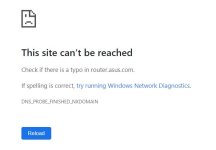
OK, I've upgraded the firmware again, carried out two resets using the button on the router (the WPS method wouldn't work) and set up a minimal configuration (no scripts, no Trend Micro, etc). I am now back to the situation where I can't access the router's GUI if using OpenVPN. Also, I noted that unlike the last time I exported the configuration file (several months ago), the one I exported today didn't have the DDNS information at the top. I added it manually, just in case that had anything to do with this problem, but it still wouldn't let me access the router's GUI. I can however, as before, access the network shares on my Synology NAS. Very frustrating.
Here's part of my last attempt to connect to the router (at exactly 16:44):-
Jun 28 16:40:00 rc_service: service 8166:notify_rc restart_letsencrypt
Jun 28 16:40:00 Let's_Encrypt: Err, DDNS update failed.
Jun 28 16:40:59 wlceventd: wlceventd_proc_event(469): eth7: Deauth_ind 34:CF:F6:E2:BF:76, status: 0, reason: Unspecified reason (1)
Jun 28 16:40:59 hostapd: eth7: STA 34:cf:f6:e2:bf:76 IEEE 802.11: disassociated
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 TLS: Initial packet from [AF_INET]109.249.181.125:65457 (via [AF_INET]86.151.218.133%ppp0), sid=3c703275 7a7c0af9
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 VERIFY OK: depth=1, C=TW, ST=TW, L=Taipei, O=ASUS, OU=Home/Office, CN=RT-AX88U, emailAddress=
me@asusrouter.lan
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 VERIFY OK: depth=0, C=TW, ST=TW, L=Taipei, O=ASUS, OU=Home/Office, CN=client, emailAddress=
me@asusrouter.lan
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_VER=2.5.7
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_PLAT=win
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_PROTO=6
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_NCP=2
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:AES-256-CBC:AES-128-CBC
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_LZ4=1
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_LZ4v2=1
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_LZO=1
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_COMP_STUB=1
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_COMP_STUBv2=1
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_TCPNL=1
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_GUI_VER=OpenVPN_GUI_11
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 peer info: IV_SSO=openurl,crtext
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 PLUGIN_CALL: POST /usr/lib/openvpn-plugin-auth-pam.so/PLUGIN_AUTH_USER_PASS_VERIFY status=0
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 TLS: Username/Password authentication succeeded for username 'Brian'
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1557', remote='link-mtu 1541'
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 1024 bit RSA, signature: RSA-SHA256
Jun 28 16:42:13 ovpn-server1[4903]: 109.249.181.125:65457 [client] Peer Connection Initiated with [AF_INET]109.249.181.125:65457 (via [AF_INET]86.151.218.133%ppp0)
Jun 28 16:42:13 ovpn-server1[4903]: client/109.249.181.125:65457 MULTI_sva: pool returned IPv4=10.8.0.2, IPv6=(Not enabled)
Jun 28 16:42:13 ovpn-server1[4903]: client/109.249.181.125:65457 MULTI: Learn: 10.8.0.2 -> client/109.249.181.125:65457
Jun 28 16:42:13 ovpn-server1[4903]: client/109.249.181.125:65457 MULTI: primary virtual IP for client/109.249.181.125:65457: 10.8.0.2
Jun 28 16:42:13 ovpn-server1[4903]: client/109.249.181.125:65457 Data Channel: using negotiated cipher 'AES-256-GCM'
Jun 28 16:42:13 ovpn-server1[4903]: client/109.249.181.125:65457 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jun 28 16:42:13 ovpn-server1[4903]: client/109.249.181.125:65457 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jun 28 16:42:13 ovpn-server1[4903]: client/109.249.181.125:65457 SENT CONTROL [client]: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0 vpn_gateway 500,redirect-gateway def1,route-gateway 10.8.0.1,topology subnet,ping 15,ping-restart 60,ifconfig 10.8.0.2 255.255.255.0,peer-id 0,cipher AES-256-GCM' (status=1)
Jun 28 16:45:00 rc_service: service 8915:notify_rc restart_letsencrypt
Jun 28 16:45:00 Let's_Encrypt: Err, DDNS update failed.
Jun 28 16:45:23 wlceventd: wlceventd_proc_event(505): eth7: Auth 82:C0:FA:28:67:C9, status: Successful (0)
Jun 28 16:45:23 wlceventd: wlceventd_proc_event(534): eth7: Assoc 82:C0:FA:28:67:C9, status: Successful (0)
Jun 28 16:45:23 hostapd: eth7: STA 82:c0:fa:28:67:c9 IEEE 802.11: associated
Jun 28 16:45:23 kernel: CFG80211-ERROR) wl_cfg80211_change_station : WLC_SCB_AUTHORIZE sta_flags_mask not set
Jun 28 16:45:23 hostapd: eth7: STA 82:c0:fa:28:67:c9 RADIUS: starting accounting session B4A1B9A5C1585942
Jun 28 16:45:23 hostapd: eth7: STA 82:c0:fa:28:67:c9 WPA: pairwise key handshake completed (RSN)
Jun 28 16:45:23 dnsmasq-dhcp[2614]: DHCPREQUEST(br0) 192.168.1.194 82:c0:fa:28:67:c9
Jun 28 16:45:23 dnsmasq-dhcp[2614]: DHCPACK(br0) 192.168.1.194 82:c0:fa:28:67:c9 Brian-s-A22
Jun 28 16:46:25 wlceventd: wlceventd_proc_event(505): eth7: Auth 34:CF:F6:E2:BF:76, status: Successful (0)
Jun 28 16:46:25 wlceventd: wlceventd_proc_event(534): eth7: Assoc 34:CF:F6:E2:BF:76, status: Successful (0)