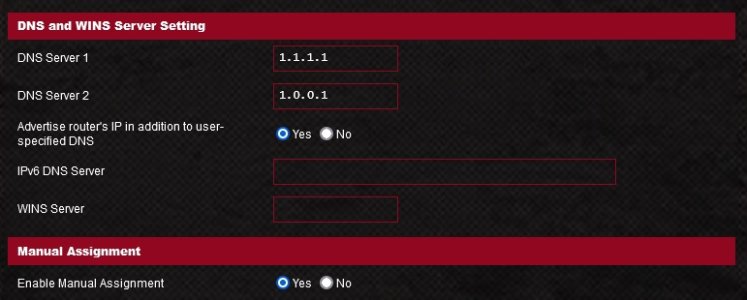
Running a AX6000 router and really no issue I am aware of. Also running Merlin firmware 388.2_2_rog. Under DNS and WINS Server Setting I have DNS Server 1 and 2 as 1.1.1.1/1.0.0.1. Then under Manual Assignment Enable Manual Assignment is checked YES.
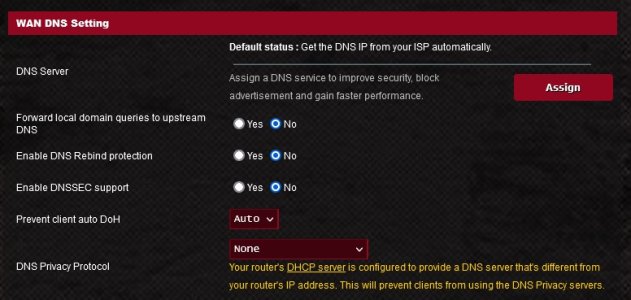
However under WAN DNS Setting under DNS Privacy Protocol I see a note that says "You router's DHCP server is configured to provide a DNS server that's different from your touter's IP address. This will prevent clients from using the DNS Privacy servers."
I'm not quite sure what that statement means.
However under WAN DNS Setting under DNS Privacy Protocol I see a note that says "You router's DHCP server is configured to provide a DNS server that's different from your touter's IP address. This will prevent clients from using the DNS Privacy servers."
I'm not quite sure what that statement means.