Greeting everyone.
I'm trying to configure a small home network with VLAN spanning across two switches.
My setup is a much simpler version than the setup explained here: http://www.smallnetbuilder.com/lanw...segment-a-small-lan-using-tagged-vlans-part-2
This link is also quite relevant, http://www.eetimes.com/document.asp?doc_id=1272019 and this http://kb.netgear.com/app/answers/d...wo-netgear-switches-to-exchange-multiple-vlan
I have studied these, as well as the manuals and done a lot of trial and error. I feel I've reached the point where it seems fair to ask for advice from someone experienced. Any help would be appreciated.
This is purely a layer 2/VLAN problem. The computers involved all have static IP addresses and can communicate perfectly fine when the VLAN settings are disabled.
The setup:
Switch 1 is a Cisco 200-08.
Switch 2 is a Zyxel GS1900.
I have the standard VLAN 1 and I have defined my own VLAN 2.
The switches are connected together like this: Switch 1 is connected by port 4 to switch 2. Switch 2 is connected to switch 1 also by port 4.
Switch 1 has a computer A connected on port 1.
Switch 1 has a computer B connected on port 2.
Switch 2 has a computer C connected on port 2.
Switch 2 has a computer D connected on port 3.
Computer A and D should be on VLAN 2.
Computer B and C should be on VLAN 1.
What I want:
Computer B, being on VLAN 1, should not be able to reach computer D on VLAN 2.
Computer A, being on VLAN 2 should be able to reach computer C, as they are both on the same VLAN (2).
I can get this to work on the same switch, but the moment I try to "propagate" the VLAN across the switches, nothing makes sense any longer.
My question:
* Is this even possible given the switches that I have? They should both support 802.1q.
* What is the correct configuration to make this work?
What I've tried:
I've followed this exact setup:
http://kb.netgear.com/app/answers/d...wo-netgear-switches-to-exchange-multiple-vlan
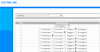
Configuration for computer A and D:
Membership: VLAN 2
PVID: 2
Tagging: Untagged
Configuration for switch A and B port 4 (port 4 is the port used to connect them):
Membership: VLAN 1 and 2.
PVID: Not relevant, set to 1.
Tagging: VLAN 1 tagged, VLAN 2 tagged.
This results in computer A not being able to reach computer D at all.
I've tried a lot of different configurations, either I cannot reach D or everyone can reach D.
My test setup is basically just running ping continuously from computer A and B to see who can talk to who while I try different setups.
I'm trying to configure a small home network with VLAN spanning across two switches.
My setup is a much simpler version than the setup explained here: http://www.smallnetbuilder.com/lanw...segment-a-small-lan-using-tagged-vlans-part-2
This link is also quite relevant, http://www.eetimes.com/document.asp?doc_id=1272019 and this http://kb.netgear.com/app/answers/d...wo-netgear-switches-to-exchange-multiple-vlan
I have studied these, as well as the manuals and done a lot of trial and error. I feel I've reached the point where it seems fair to ask for advice from someone experienced. Any help would be appreciated.
This is purely a layer 2/VLAN problem. The computers involved all have static IP addresses and can communicate perfectly fine when the VLAN settings are disabled.
The setup:
Switch 1 is a Cisco 200-08.
Switch 2 is a Zyxel GS1900.
I have the standard VLAN 1 and I have defined my own VLAN 2.
The switches are connected together like this: Switch 1 is connected by port 4 to switch 2. Switch 2 is connected to switch 1 also by port 4.
Switch 1 has a computer A connected on port 1.
Switch 1 has a computer B connected on port 2.
Switch 2 has a computer C connected on port 2.
Switch 2 has a computer D connected on port 3.
Computer A and D should be on VLAN 2.
Computer B and C should be on VLAN 1.
What I want:
Computer B, being on VLAN 1, should not be able to reach computer D on VLAN 2.
Computer A, being on VLAN 2 should be able to reach computer C, as they are both on the same VLAN (2).
I can get this to work on the same switch, but the moment I try to "propagate" the VLAN across the switches, nothing makes sense any longer.
My question:
* Is this even possible given the switches that I have? They should both support 802.1q.
* What is the correct configuration to make this work?
What I've tried:
I've followed this exact setup:
http://kb.netgear.com/app/answers/d...wo-netgear-switches-to-exchange-multiple-vlan
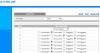
Configuration for computer A and D:
Membership: VLAN 2
PVID: 2
Tagging: Untagged
Configuration for switch A and B port 4 (port 4 is the port used to connect them):
Membership: VLAN 1 and 2.
PVID: Not relevant, set to 1.
Tagging: VLAN 1 tagged, VLAN 2 tagged.
This results in computer A not being able to reach computer D at all.
I've tried a lot of different configurations, either I cannot reach D or everyone can reach D.
My test setup is basically just running ping continuously from computer A and B to see who can talk to who while I try different setups.
Last edited: