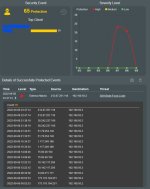
Seeing a very big increase in SSH login attempts caught in Turris Honeypot.
This IP has made 5000+ attempts today : 104.248.89.194
This session by 104.244.76.203 is more interesting as you'll see a string of 45 commands issued .
>> Honeypot session. <<
This IP has made 5000+ attempts today : 104.248.89.194
This session by 104.244.76.203 is more interesting as you'll see a string of 45 commands issued .
>> Honeypot session. <<