dugaduga
Senior Member
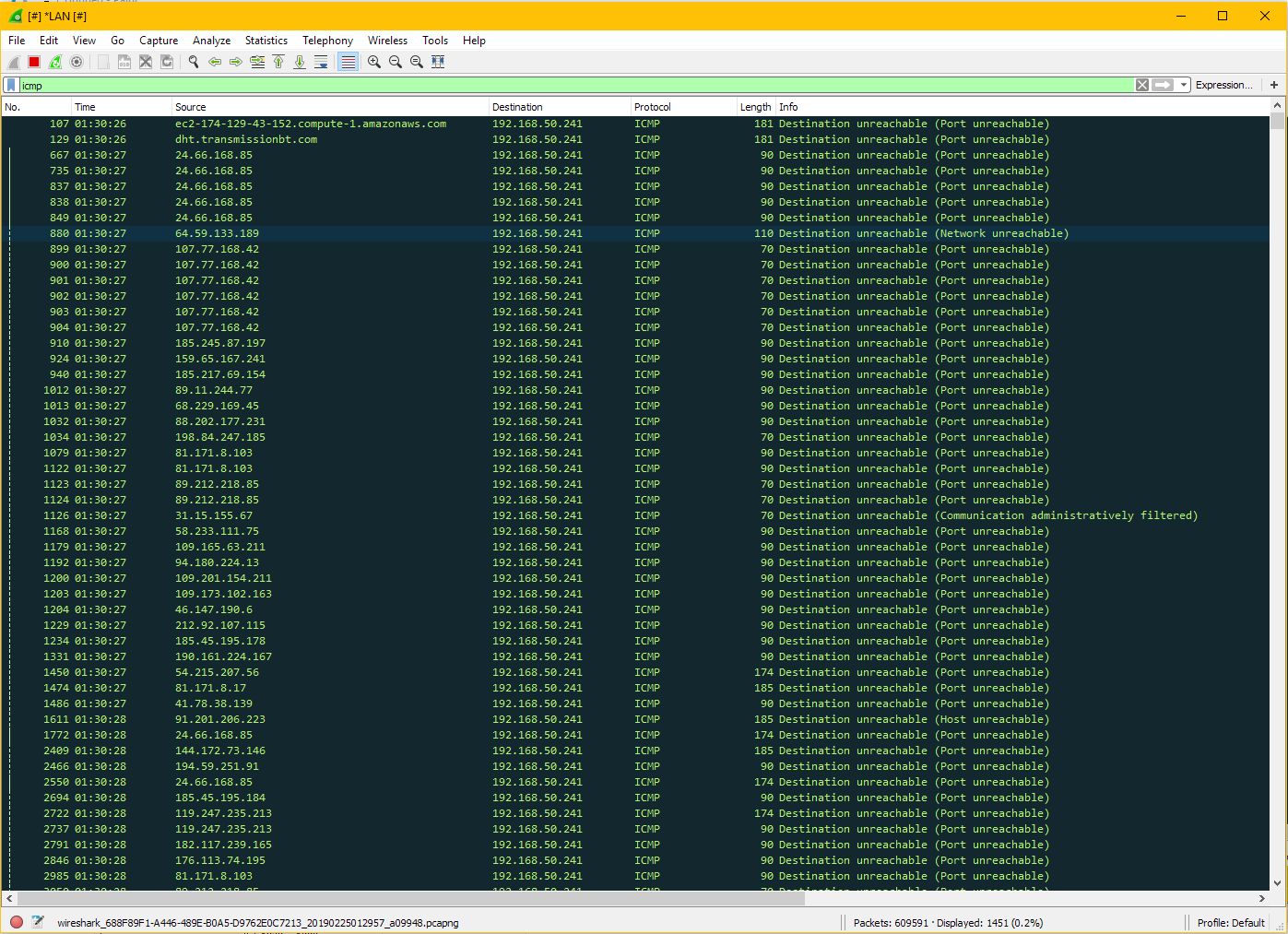
Win 10 X64. I notice this particularly when using bittorrent; Why is the router letting this through? Oddly for a while I noticed my PC was responding to these pings for 10 minutes after shutting down bittorrent. In windows 7 everything shut up after closing bittorrent. A reboot of the router stopped it. Block (ALL) incoming was enabled in group policy, "no ICMP exceptions" enabled in group policy. Added an extra block incoming (all) firewall rule to block everything just for extra measure... and yet this was all happening. After a reboot my firewall started dropping them again.
I was also seeing a lot of ICMP incoming from my WAN IP to my subnet IP. Perhaps packets that were generated to look like my wan IP anyway; given anything could get through, it could be foreign too. There were incoming Wan to Subnet IP ICMP + UDP 8999 bittorrent packets.
@RMerlin is this normal AsusWRT-Merlin behavior? "Respond ICMP Echo (ping) Request from WAN" is disabled on the router, is it supposed to silently allow those packets through?
I've also got a machine arping to 127.0.0.0 on the lan XArp is flagging.
Using 384.10_BcraFFY-test2-geb1052481b
I was also seeing a lot of ICMP incoming from my WAN IP to my subnet IP. Perhaps packets that were generated to look like my wan IP anyway; given anything could get through, it could be foreign too. There were incoming Wan to Subnet IP ICMP + UDP 8999 bittorrent packets.
@RMerlin is this normal AsusWRT-Merlin behavior? "Respond ICMP Echo (ping) Request from WAN" is disabled on the router, is it supposed to silently allow those packets through?
I've also got a machine arping to 127.0.0.0 on the lan XArp is flagging.
Using 384.10_BcraFFY-test2-geb1052481b
Last edited: