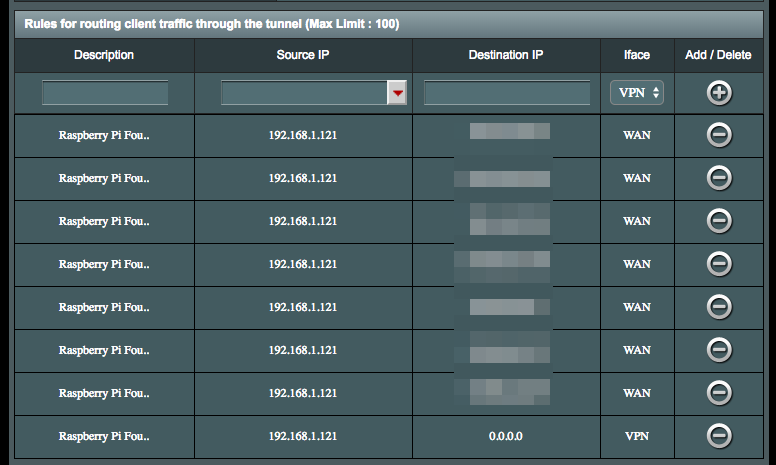
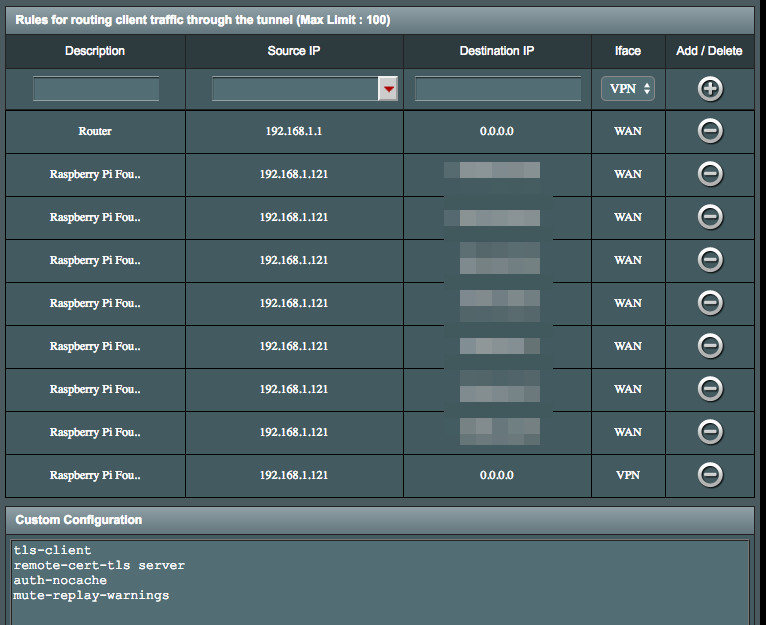
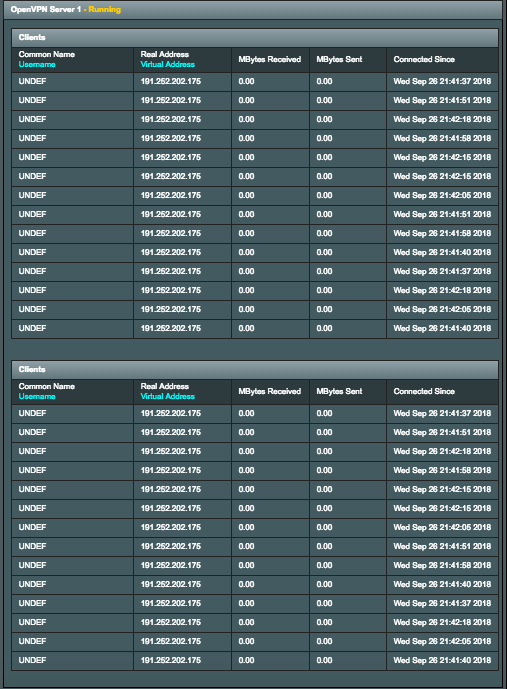
Ok, so hopefully I'm still following

Here's the output of "ip rule" - destination IPs masked
Code:
/tmp/home/root# ip rule
0: from all lookup local
10001: from 192.168.1.121 to 123.123.123.123 lookup main
10002: from 192.168.1.121 to 121.121.121.121 lookup main
10003: from 192.168.1.121 to 231.231.231.231. lookup main
10004: from 192.168.1.121 to 222.222.222.222 lookup main
10005: from 192.168.1.121 111.111.111.111.111 lookup main
10006: from 192.168.1.121 to 233.233.233.233 lookup main
10007: from 192.168.1.121 to 112.112.112.112 lookup main
10101: from 192.168.1.121 lookup ovpnc1
32766: from all lookup main
32767: from all lookup default
Output of "iptables --line -t nat -nvL DNSVPN1"
Code:
Chain DNSVPN1 (0 references)
num pkts bytes target prot opt in out source destination
Feels like something is missing here ^^ ?
Output of "iptables -nvL PREROUTING -t mangle --line"
Code:
Chain PREROUTING (policy ACCEPT 493K packets, 64M bytes)
num pkts bytes target prot opt in out source destination
1 1836 1637K MARK all -- tun11 * 0.0.0.0/0 0.0.0.0/0 MARK xset 0x1/0x7
2 20029 1973K MARK all -- tun21 * 0.0.0.0/0 0.0.0.0/0 MARK xset 0x1/0x7
Output of "iptables -nvL PREROUTING -t nat --line"
Code:
Chain PREROUTING (policy ACCEPT 23637 packets, 3359K bytes)
num pkts bytes target prot opt in out source destination
1 118K 4939K ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:1194
2 168K 9718K VSERVER all -- * * 0.0.0.0/0 MY.WAN.IP.NR
3 0 0 PCREDIRECT all -- br0 * 0.0.0.0/0 0.0.0.0/0 MAC MACADDRESSOFWANBLOCKEDDEVICE
4 0 0 PCREDIRECT all -- br0 * 0.0.0.0/0 0.0.0.0/0 MAC MACADDRESSOFWANBLOCKEDDEVICE
Yes, the device is assigned a static address in the network
Output "nvram show | grep vpn_clientX_rgw"
Code:
size: 73056 bytes (58016 left)
vpn_client1_rgw=3
I changed router log level to "debug" and tried accessing the IPs that should be routed through WAN but the log didn't show any new line.
It's still accessing the IPs using the VPN-tunnel
Not in the VPN section, only under NFS