skilsprism
New Around Here
Hi!
Need your help guys. I have an N66U running Merlin 380.65 . I would like to create a VPN chain.
ISP-> VPN Client1->VPNClient2->Internet.
I would like my VPN Client2 never to touch my ISP. Can I add a specific rule in place, that says VPNclient2 will not connect unless VPN Client1 is connected?
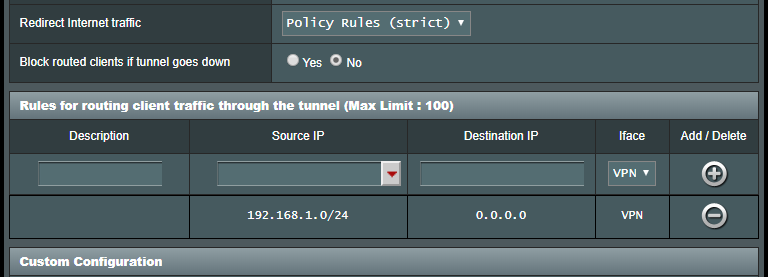
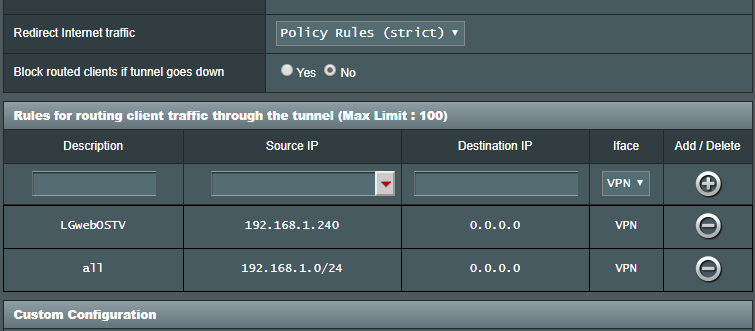
So far, I have configured VP1 correctly. I have added Policy Rules on both VPN Clients that say Source IP: 192.168.1.0/24 to VPN
and added a Kill Switch for both VP1 and VPN2. I figure the kill switch will keep VPN2 from touching the ISP?
VPN Client 2 is not working right now... Log says "Tunnel down - VPN client access blocked". Working to fix this.
Any help with this would be greatly appreciated.
Cheers!
Need your help guys. I have an N66U running Merlin 380.65 . I would like to create a VPN chain.
ISP-> VPN Client1->VPNClient2->Internet.
I would like my VPN Client2 never to touch my ISP. Can I add a specific rule in place, that says VPNclient2 will not connect unless VPN Client1 is connected?
So far, I have configured VP1 correctly. I have added Policy Rules on both VPN Clients that say Source IP: 192.168.1.0/24 to VPN
and added a Kill Switch for both VP1 and VPN2. I figure the kill switch will keep VPN2 from touching the ISP?
VPN Client 2 is not working right now... Log says "Tunnel down - VPN client access blocked". Working to fix this.
Any help with this would be greatly appreciated.
Cheers!