Hello,
I have encountered guest Wi-Fi connection issues when trying to use YazFi in combination with custom scripts for VLAN creation on RT-AC86U: the Wi-Fi devices (phone and laptop) connect for a short time (8 seconds max) to the guest network and are disconnected; they appear for a short time in the Connected guests list, but on the device themselves they do not appear as having established a successful connection. On the main networks there is no problem, and the devices are in close proximity to the router (1-2 meters max, open air).
The vlan configuration scripts were modified from the ones presented here: RT-86U - vlanctl & ethctl usage puzzle
Environment:
HW : RT-AC86U ; SW: Asuswrt-Merlin 386.5_2; Yaz-Fi 4.4.2
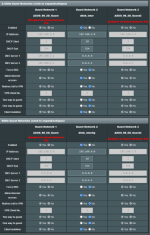
Yaz-Fi network config: See attached YazFi_GuiCFG photo.
Modified scripts:
Bridges configuration:
Wireless log snippet:
I have encountered guest Wi-Fi connection issues when trying to use YazFi in combination with custom scripts for VLAN creation on RT-AC86U: the Wi-Fi devices (phone and laptop) connect for a short time (8 seconds max) to the guest network and are disconnected; they appear for a short time in the Connected guests list, but on the device themselves they do not appear as having established a successful connection. On the main networks there is no problem, and the devices are in close proximity to the router (1-2 meters max, open air).
The vlan configuration scripts were modified from the ones presented here: RT-86U - vlanctl & ethctl usage puzzle
Environment:
HW : RT-AC86U ; SW: Asuswrt-Merlin 386.5_2; Yaz-Fi 4.4.2
Yaz-Fi network config: See attached YazFi_GuiCFG photo.
Modified scripts:
#!/bin/sh
/jffs/scripts/YazFi startup & # YazFi
/jffs/scripts/scmerlin startup & # scMerlin
sleep 30s
/jffs/scripts/vlan-isol-final & # setup vlan ctl rules
/jffs/scripts/fw-vlan-isol-final & # setup vlan ipconfig rules
/jffs/scripts/YazFi startup & # YazFi
/jffs/scripts/scmerlin startup & # scMerlin
sleep 30s
/jffs/scripts/vlan-isol-final & # setup vlan ctl rules
/jffs/scripts/fw-vlan-isol-final & # setup vlan ipconfig rules
#!/bin/sh
# Physical port to interface map for RT-AC86U:
# eth0 WAN
# eth1 LAN 4
# eth2 LAN 3
# eth3 LAN 2
# eth4 LAN 1
# eth5 2.4 GHz Radio
# eth6 5 GHz Radio
logger -t "vlan-isol" "Entered vlan-isol"
brctl delif br0 eth4
brctl delif br0 eth3
# management network
vlanctl --mcast --if-create eth4 1
vlanctl --if eth4 --rx --tags 1 --filter-vid 1 0 --pop-tag --set-rxif eth4.v1 --rule-append
vlanctl --if eth4 --tx --tags 0 --filter-txif eth4.v1 --push-tag --set-vid 1 0 --rule-append
ifconfig eth4.v1 up
# home network vlan
vlanctl --mcast --if-create eth4 10
vlanctl --if eth4 --rx --tags 1 --filter-vid 10 0 --pop-tag --set-rxif eth4.v10 --rule-append
vlanctl --if eth4 --tx --tags 0 --filter-txif eth4.v10 --push-tag --set-vid 10 0 --rule-append
ifconfig eth4.v10 up
# work network vlan
vlanctl --mcast --if-create eth4 20
vlanctl --if eth4 --rx --tags 1 --filter-vid 20 0 --pop-tag --set-rxif eth4.v20 --rule-append
vlanctl --if eth4 --tx --tags 0 --filter-txif eth4.v20 --push-tag --set-vid 20 0 --rule-append
ifconfig eth4.v20 up
vlanctl --if eth4 --set-if-mode-rg
vlanctl --if eth4 --tx --tags 0 --default-miss-drop
brctl addif br0 eth4.v1
brctl addbr br10
brctl addif br10 eth4.v10
brctl addbr br20
brctl addif br20 eth4.v20
brctl addbr br100
brctl stp br100 on
brctl addif br100 eth3
brctl setfd br100 2
ifconfig br10 192.168.10.1 netmask 255.255.255.0 up
ifconfig br20 192.168.20.1 netmask 255.255.255.0 up
ifconfig br100 192.168.100.1 netmask 255.255.255.0 up
nvram set lan_ifnames="eth1 eth2 eth4.v1 eth5 eth6"
nvram set br0_ifnames="eth1 eth2 eth4.v1 eth5 eth6"
nvram set br10_ifname=br10
nvram set br10_ifnames="eth4.v10"
nvram set lan1_ifname=br10
nvram set lan1_ifnames="eth4.v10"
nvram set br20_ifname=br20
nvram set br20_ifnames="eth4.v20"
nvram set lan2_ifname=br20
nvram set lan2_ifnames="eth4.v20"
nvram set br100_ifname=br100
nvram set br100_ifnames="eth3"
nvram set lan3_ifname=br100
nvram set lan3_ifnames="eth3"
nvram commit
killall eapd
eapd
ethswctl -c hw-switching -o disable
logger -t "vlan-isol" "Exited vlan-isol"
# Physical port to interface map for RT-AC86U:
# eth0 WAN
# eth1 LAN 4
# eth2 LAN 3
# eth3 LAN 2
# eth4 LAN 1
# eth5 2.4 GHz Radio
# eth6 5 GHz Radio
logger -t "vlan-isol" "Entered vlan-isol"
brctl delif br0 eth4
brctl delif br0 eth3
# management network
vlanctl --mcast --if-create eth4 1
vlanctl --if eth4 --rx --tags 1 --filter-vid 1 0 --pop-tag --set-rxif eth4.v1 --rule-append
vlanctl --if eth4 --tx --tags 0 --filter-txif eth4.v1 --push-tag --set-vid 1 0 --rule-append
ifconfig eth4.v1 up
# home network vlan
vlanctl --mcast --if-create eth4 10
vlanctl --if eth4 --rx --tags 1 --filter-vid 10 0 --pop-tag --set-rxif eth4.v10 --rule-append
vlanctl --if eth4 --tx --tags 0 --filter-txif eth4.v10 --push-tag --set-vid 10 0 --rule-append
ifconfig eth4.v10 up
# work network vlan
vlanctl --mcast --if-create eth4 20
vlanctl --if eth4 --rx --tags 1 --filter-vid 20 0 --pop-tag --set-rxif eth4.v20 --rule-append
vlanctl --if eth4 --tx --tags 0 --filter-txif eth4.v20 --push-tag --set-vid 20 0 --rule-append
ifconfig eth4.v20 up
vlanctl --if eth4 --set-if-mode-rg
vlanctl --if eth4 --tx --tags 0 --default-miss-drop
brctl addif br0 eth4.v1
brctl addbr br10
brctl addif br10 eth4.v10
brctl addbr br20
brctl addif br20 eth4.v20
brctl addbr br100
brctl stp br100 on
brctl addif br100 eth3
brctl setfd br100 2
ifconfig br10 192.168.10.1 netmask 255.255.255.0 up
ifconfig br20 192.168.20.1 netmask 255.255.255.0 up
ifconfig br100 192.168.100.1 netmask 255.255.255.0 up
nvram set lan_ifnames="eth1 eth2 eth4.v1 eth5 eth6"
nvram set br0_ifnames="eth1 eth2 eth4.v1 eth5 eth6"
nvram set br10_ifname=br10
nvram set br10_ifnames="eth4.v10"
nvram set lan1_ifname=br10
nvram set lan1_ifnames="eth4.v10"
nvram set br20_ifname=br20
nvram set br20_ifnames="eth4.v20"
nvram set lan2_ifname=br20
nvram set lan2_ifnames="eth4.v20"
nvram set br100_ifname=br100
nvram set br100_ifnames="eth3"
nvram set lan3_ifname=br100
nvram set lan3_ifnames="eth3"
nvram commit
killall eapd
eapd
ethswctl -c hw-switching -o disable
logger -t "vlan-isol" "Exited vlan-isol"
#!/bin/sh
# Make sure the script is indeed invoked
logger -t "br10" "firewall-start: applying fw rules for br10"
# limit br10 to wan access
iptables -I INPUT -i br10 -m state --state NEW -j ACCEPT
iptables -I FORWARD -i br10 -o ppp0 -j ACCEPT
iptables -I FORWARD -i br10 -o br10 -j ACCEPT
iptables -t nat -I POSTROUTING -o br10 -j MASQUERADE
# Make sure the script is indeed invoked
logger -t "br20" "firewall-start: applying fw rules for br20"
# limit br20 to wan access
iptables -I INPUT -i br20 -m state --state NEW -j ACCEPT
iptables -I FORWARD -i br20 -o ppp0 -j ACCEPT
iptables -I FORWARD -i br20 -o br20 -j ACCEPT
iptables -t nat -I POSTROUTING -o br20 -j MASQUERADE
# Make sure the script is indeed invoked
logger -t "br100" "firewall-start: applying fw rules for br100"
# limit br100 to wan access
iptables -I INPUT -i br100 -m state --state NEW -j ACCEPT
iptables -I FORWARD -i br100 -o ppp0 -j ACCEPT
iptables -I FORWARD -i br100 -o br100 -j ACCEPT
iptables -t nat -I POSTROUTING -o br100 -j MASQUERADE
service restart_dnsmasq
# Make sure the script is indeed invoked
logger -t "br10" "firewall-start: applying fw rules for br10"
# limit br10 to wan access
iptables -I INPUT -i br10 -m state --state NEW -j ACCEPT
iptables -I FORWARD -i br10 -o ppp0 -j ACCEPT
iptables -I FORWARD -i br10 -o br10 -j ACCEPT
iptables -t nat -I POSTROUTING -o br10 -j MASQUERADE
# Make sure the script is indeed invoked
logger -t "br20" "firewall-start: applying fw rules for br20"
# limit br20 to wan access
iptables -I INPUT -i br20 -m state --state NEW -j ACCEPT
iptables -I FORWARD -i br20 -o ppp0 -j ACCEPT
iptables -I FORWARD -i br20 -o br20 -j ACCEPT
iptables -t nat -I POSTROUTING -o br20 -j MASQUERADE
# Make sure the script is indeed invoked
logger -t "br100" "firewall-start: applying fw rules for br100"
# limit br100 to wan access
iptables -I INPUT -i br100 -m state --state NEW -j ACCEPT
iptables -I FORWARD -i br100 -o ppp0 -j ACCEPT
iptables -I FORWARD -i br100 -o br100 -j ACCEPT
iptables -t nat -I POSTROUTING -o br100 -j MASQUERADE
service restart_dnsmasq
interface=br10
dhcp-range=br10,192.168.10.10,192.168.10.254,255.255.255.0,24h
dhcp-option=br10,3,192.168.10.1
interface=br20
dhcp-range=br20,192.168.20.10,192.168.20.254,255.255.255.0,24h
dhcp-option=br20,3,192.168.20.1
interface=br100
dhcp-range=br100,192.168.100.10,192.168.100.254,255.255.255.0,24h
dhcp-option=br100,3,192.168.100.1
dhcp-range=br10,192.168.10.10,192.168.10.254,255.255.255.0,24h
dhcp-option=br10,3,192.168.10.1
interface=br20
dhcp-range=br20,192.168.20.10,192.168.20.254,255.255.255.0,24h
dhcp-option=br20,3,192.168.20.1
interface=br100
dhcp-range=br100,192.168.100.10,192.168.100.254,255.255.255.0,24h
dhcp-option=br100,3,192.168.100.1
Code:
username@RT-AC86U-2698:/tmp/home/root# brctl show
bridge name bridge id STP enabled interfaces
br0 8000.244bfebd2698 yes eth1
eth2
eth4.v1
eth5
eth6
wl0.2
wl1.2
br10 8000.244bfebd2698 no eth4.v10
br100 8000.244bfebd2698 yes eth3
br20 8000.244bfebd2698 no eth4.v20Wireless log snippet:
Code:
Aug 21 22:56:58 RT-AC86U-2698 wlceventd: wlceventd_proc_event(527): wl0.2: Auth AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 22:56:58 RT-AC86U-2698 wlceventd: wlceventd_proc_event(556): wl0.2: Assoc AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 22:57:06 RT-AC86U-2698 wlceventd: wlceventd_proc_event(491): wl0.2: Deauth_ind AC:57:75:10:EA:CB, status: 0, reason: Deauthenticated because sending station is leaving (or has left) IBSS or ESS (3), rssi:-43
Aug 21 22:59:47 RT-AC86U-2698 wlceventd: wlceventd_proc_event(527): wl0.2: Auth AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 22:59:47 RT-AC86U-2698 wlceventd: wlceventd_proc_event(556): wl0.2: Assoc AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 22:59:56 RT-AC86U-2698 wlceventd: wlceventd_proc_event(491): wl0.2: Deauth_ind AC:57:75:10:EA:CB, status: 0, reason: Deauthenticated because sending station is leaving (or has left) IBSS or ESS (3), rssi:-48
Aug 21 22:59:59 RT-AC86U-2698 wlceventd: wlceventd_proc_event(527): wl0.2: Auth AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 22:59:59 RT-AC86U-2698 wlceventd: wlceventd_proc_event(556): wl0.2: Assoc AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 23:00:07 RT-AC86U-2698 wlceventd: wlceventd_proc_event(491): wl0.2: Deauth_ind AC:57:75:10:EA:CB, status: 0, reason: Deauthenticated because sending station is leaving (or has left) IBSS or ESS (3), rssi:-46
Aug 21 23:00:17 RT-AC86U-2698 wlceventd: wlceventd_proc_event(527): wl0.2: Auth AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 23:00:17 RT-AC86U-2698 wlceventd: wlceventd_proc_event(556): wl0.2: Assoc AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 23:00:25 RT-AC86U-2698 wlceventd: wlceventd_proc_event(491): wl0.2: Deauth_ind AC:57:75:10:EA:CB, status: 0, reason: Deauthenticated because sending station is leaving (or has left) IBSS or ESS (3), rssi:-43
Aug 21 23:00:31 RT-AC86U-2698 wlceventd: wlceventd_proc_event(527): wl0.2: Auth AC:57:75:10:EA:CB, status: Successful (0), rssi:0
Aug 21 23:00:31 RT-AC86U-2698 wlceventd: wlceventd_proc_event(556): wl0.2: Assoc AC:57:75:10:EA:CB, status: Successful (0), rssi:0