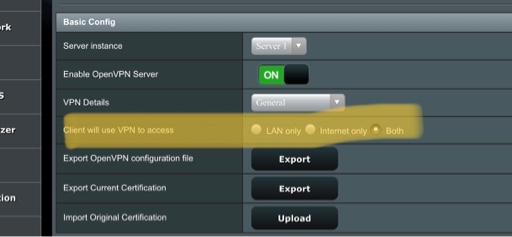
Hello
I have a Fritzbox on WAN port of a AC88U router which runs also an OpenVPN server.
I want to access the Fritzbox GUI from a client connected using OpenVPN.
Config is
Fritzbox: 10.10.10.1
Router WAN: 10.10.10.10
Router LAN: 10.10.1.0/255.255.255.0
Router OpenVPN subnet 10.10.0.0/255.255.255.0
OpenVPN client Router LAN 10.10.2.0/255.255.255.0
Currently I have access to the Fitzbox GUI from clients on the Router LAN port but it seems OpenVPN does not route it to the clients. I push the 10.10.10.0 to the client:
push "route 10.10.10.0 255.255.255.0"
additionally I also add the command:
route 10.10.10.0 255.255.255.0
but this give a fail in the log:
Ignore conflicted routing rule: 10.10.10.0 255.255.255.0
I need to route the Fritzbox at 10.10.10.1 to the clients.
Any help?
I have a Fritzbox on WAN port of a AC88U router which runs also an OpenVPN server.
I want to access the Fritzbox GUI from a client connected using OpenVPN.
Config is
Fritzbox: 10.10.10.1
Router WAN: 10.10.10.10
Router LAN: 10.10.1.0/255.255.255.0
Router OpenVPN subnet 10.10.0.0/255.255.255.0
OpenVPN client Router LAN 10.10.2.0/255.255.255.0
Currently I have access to the Fitzbox GUI from clients on the Router LAN port but it seems OpenVPN does not route it to the clients. I push the 10.10.10.0 to the client:
push "route 10.10.10.0 255.255.255.0"
additionally I also add the command:
route 10.10.10.0 255.255.255.0
but this give a fail in the log:
Ignore conflicted routing rule: 10.10.10.0 255.255.255.0
I need to route the Fritzbox at 10.10.10.1 to the clients.
Any help?