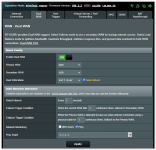
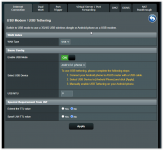
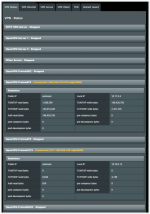
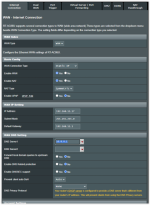
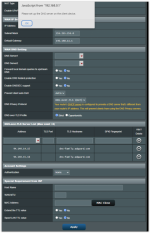
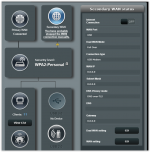
I'm trying to get Dual WAN working (backup connectivity provided via a USB-connected Android phone) but getting erratic behavior when I "cut" the connectivity to my primary WAN:
My AC86U with the latest Merlin is constantly switching between the two WANs which I suspect is due to me using a VPN config on my primary WAN.
Can anyone confirm this can be an issue? Attached system log and screenshots.
Many thanks!
My AC86U with the latest Merlin is constantly switching between the two WANs which I suspect is due to me using a VPN config on my primary WAN.
Can anyone confirm this can be an issue? Attached system log and screenshots.
Many thanks!