WildWurger
Occasional Visitor
Hi all gurus, I really need some help on my own test lab, I am creating multiple networks and building a test lab. So therefore i need to create a few networks.
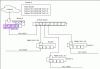
As attached,
there is 1 internet from WAN then goes to Router A, which is RT-N66U from asus with Merlin firmware 3.0.0.4.270.26b. it has 2 OpenVPN instance currently.
This is the first network segment 10.0.1.0/24 which all my usual clients will connect to like wireless, wired and so on.
then i want to create 3 more networks as shown,
and there are 3 more routers connected to the switch which the switch is connected to Router A.
10.1.0.0/24 (Router 1, Tomato USB) WAN: 10.0.1.30
10.1.1.0/24 (Router 2, Linksys Stock) WAN: 10.0.1.31
10.1.2.0/24 (Router 3, OpenWRT) WAN: 10.0.1.32
I did try on TomatoUSB, Linksys, OpenWRT, dd-WRT, Microsoft RRAS, pfSense.... with similar settings
in my Router A, i have the static routing set as shown as attached
an all the router below the Router A. I had set to "Router Mode" which disable NAT.
I can ping from Router A segment to all the hosts of other segments no problem.
however i cannot ping in reverse, that is a Host from 10.0.1.100 can ping to 10.1.0.100 and 10.1.1.100 and 10.1.2.100 (sorry for the IP addressing convention) but not the other way round, host 10.1.0.100, 10.1.1.100 and 10.1.2.100 are unable to ping 10.0.1.100
IF, i set to "Gateway Mode", which i believe not the right way... the situation reverse, all the 10.1.0.100, 10.1.1.100 and 10.1.2.100 can ping 10.0.1.100 but not the other way round.
In either way, all networks can access internet alright.
Router 1, 2 and 3 can ping host in 10.0.1.0/24 no problem, but its DHCP leases cannot....
clients from the 10.1.0.100, 10.1.1.100 and 10.1.2.100 can ping each other hosts no problem.
Please all gurus take a look and enlighten me, where did i do wrong... it driving me nuts!
Thanks in advance
As attached,
there is 1 internet from WAN then goes to Router A, which is RT-N66U from asus with Merlin firmware 3.0.0.4.270.26b. it has 2 OpenVPN instance currently.
This is the first network segment 10.0.1.0/24 which all my usual clients will connect to like wireless, wired and so on.
then i want to create 3 more networks as shown,
and there are 3 more routers connected to the switch which the switch is connected to Router A.
10.1.0.0/24 (Router 1, Tomato USB) WAN: 10.0.1.30
10.1.1.0/24 (Router 2, Linksys Stock) WAN: 10.0.1.31
10.1.2.0/24 (Router 3, OpenWRT) WAN: 10.0.1.32
I did try on TomatoUSB, Linksys, OpenWRT, dd-WRT, Microsoft RRAS, pfSense.... with similar settings
in my Router A, i have the static routing set as shown as attached
an all the router below the Router A. I had set to "Router Mode" which disable NAT.
I can ping from Router A segment to all the hosts of other segments no problem.
however i cannot ping in reverse, that is a Host from 10.0.1.100 can ping to 10.1.0.100 and 10.1.1.100 and 10.1.2.100 (sorry for the IP addressing convention) but not the other way round, host 10.1.0.100, 10.1.1.100 and 10.1.2.100 are unable to ping 10.0.1.100
IF, i set to "Gateway Mode", which i believe not the right way... the situation reverse, all the 10.1.0.100, 10.1.1.100 and 10.1.2.100 can ping 10.0.1.100 but not the other way round.
In either way, all networks can access internet alright.
Router 1, 2 and 3 can ping host in 10.0.1.0/24 no problem, but its DHCP leases cannot....
clients from the 10.1.0.100, 10.1.1.100 and 10.1.2.100 can ping each other hosts no problem.
Please all gurus take a look and enlighten me, where did i do wrong... it driving me nuts!
Thanks in advance