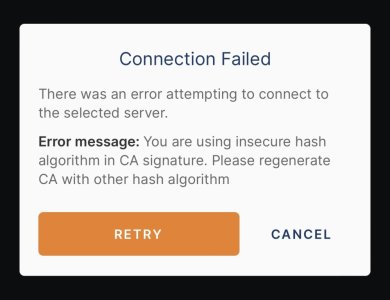
After updating to the latest iOS Open VPN client, I can no longer connect to the server side on the Asus AX86U. I think the iOS client has updated to the newest open VPN version while the Asus Merlin server implementation is out of spec at this point. Is there a fix coming?
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Open VPN App No Longer Working
- Thread starter David2001
- Start date
The problem is not due to the OpenSSL (or OpenVPN) software. The cause of the error & the solution are spelled out in your screenshot.After updating to the latest iOS Open VPN client, I can no longer connect to the server side on the Asus AX86U. I think the iOS client has updated to the newest open VPN version while the Asus Merlin server implementation is out of spec at this point. Is there a fix coming?
----------------------------------------------------
"Error message: you are using insecure hash algorithm in CA signature. Please regenerate CA with other hash algorithm."
----------------------------------------------------
IOW, when you generated your current OpenVPN CA certificate, the signature hash algorithm that was used is no longer supported by the updated OpenVPN client s/w (likely because that hash algorithm is now deprecated), so you must now regenerate your CA certificate using the "Renew" button on the router's webGUI and then export the new client configuration file.
After the CA certificate has been regenerated, you can check what the signature hash algorithm is with the following command (via an SSH terminal session):
Bash:
openssl x509 -noout -text -in "/jffs/openvpn/vpn_crt_server1_ca" | grep "Signature Algorithm"
Last edited:
Similar threads
- Replies
- 3
- Views
- 330
- Replies
- 14
- Views
- 1K
- Replies
- 7
- Views
- 569
Similar threads
Similar threads
-
-
How to open ipv6 firewall to a port on the router?
- Started by John Tetreault
- Replies: 4
-
-
-
Why does my RT-AX88u show ports 80,443 & 21 open from WAN?
- Started by Jammy456
- Replies: 0
-
-
-
Assigned IP address to the WAN interface via VPN director: no internet connection - why?
- Started by OB1
- Replies: 1
-
-
Latest threads
-
-
-
-
Can't get 2gbps to my unraid server
- Started by zekesdad
- Replies: 2
-
changed AC68U to AX86U Pro, same guest network setting but all devices gone?
- Started by Heronimos
- Replies: 4
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!