You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
AB-Solution webpage/antivirus problems
- Thread starter TheLyppardMan
- Start date
I still need to keep the SSL/TLS feature switched off in ESET
Just to add to the above, you probably need to import the cert into ESET as well to be able to turn on the TLS feature again without it blasting warnings.
sentinelvdx
Very Senior Member
I did that long time ago and it didn't work... eset will still shownpop ups
Sent from S.G. S9+ Duos
Just to add to the above, you probably need to import the cert into ESET as well to be able to turn on the TLS feature again without it blasting warnings.
Sent from S.G. S9+ Duos
Last edited:
I did that long time ago and it didn't work... eset will still shownpop ups
Did you import the CA or the TLS cert?
Last edited:
TheLyppardMan
Very Senior Member
I followed these instructions...
- Open your browser and visit http://192.168.1.2/ca.crt.
- Select "Trust this CA to identify websites" on the screen pop-up (I also ticked the e-mail box as I wasn't sure if that was needed as well).
- Click "Ok"
- Double click on `ca.crt' to start Keychain's import wizard.
- Select keychain "system" and click "Add".
Attachments
I just realized the language I used was confusing, and have modified my comment to clarify.By the way, what is the difference between a "CA" and a "cert"? The instructions refer to a "CA Certificate".
When you set up an HTTPS server (pixelserv-tls is one) you will be creating two certs, one for the server itself and one as a CA that would sign/certify the previous one, hence the distinction.
I was just wondering if the wrong cert was imported so @sentineldvx is still seeing cert errors in ESET.
sentinelvdx
Very Senior Member
Could be[emoji39], I'll try again and updateI just realized the language I used was confusing, and have modified my comment to clarify.
When you set up an HTTPS server (pixelserv-tls is one) you will be creating two certs, one for the server itself and one as a CA that would sign/certify the previous one, hence the distinction.
I was just wondering if the wrong cert was imported so @sentineldvx is still seeing cert errors in ESET.
Sent from S.G. S9+ Duos
TheLyppardMan
Very Senior Member
So based on all the above, what do I need to resolve this issue? Also, I have received a reply from ESET at follows, but I'm not sure it makes much sense (to me at least):-
------------ Begin Quote ------------
Thank you for contacting ESET Technical Support.
Disabling SSL scanning does present an increased risk and is not recommended. It should be possible to allow the untrusted certificate by following the instructions in this article - https://support.eset.com/kb6407
Alternatively, you should be able to add the certificate and set it to allow, via ESET > Setup > Advanced Setup > Web And Email > SSL/TLS > List of known certificates (Edit) > Add - https://help.eset.com/eis/11.1/en-US/idh_config_epfw_ssl_known.html
If you have any problems or require any further assistance then please feel free to call us on 01202 405 405 and select option 3, one of our technical staff should be able to help. Our opening hours are 08:30-20:00 weekdays. It would be helpful if you could be at this page when you call: https://www.eset.com/uk/remote-support/
------------ End Quote ------------
------------ Begin Quote ------------
Thank you for contacting ESET Technical Support.
Disabling SSL scanning does present an increased risk and is not recommended. It should be possible to allow the untrusted certificate by following the instructions in this article - https://support.eset.com/kb6407
Alternatively, you should be able to add the certificate and set it to allow, via ESET > Setup > Advanced Setup > Web And Email > SSL/TLS > List of known certificates (Edit) > Add - https://help.eset.com/eis/11.1/en-US/idh_config_epfw_ssl_known.html
If you have any problems or require any further assistance then please feel free to call us on 01202 405 405 and select option 3, one of our technical staff should be able to help. Our opening hours are 08:30-20:00 weekdays. It would be helpful if you could be at this page when you call: https://www.eset.com/uk/remote-support/
------------ End Quote ------------
TheLyppardMan
Very Senior Member
Do that.Alternatively, you should be able to add the certificate and set it to allow, via ESET > Setup > Advanced Setup > Web And Email > SSL/TLS > List of known certificates (Edit) > Add - https://help.eset.com/eis/11.1/en-US/idh_config_epfw_ssl_known.html
TheLyppardMan
Very Senior Member
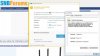
This is the add page in the GUI. What steps do I need to follow and what will this achieve?Do that.
Attachments
This is the add page in the GUI. What steps do I need to follow and what will this achieve?
File > select your pixelserv ca.crt > select ‘Allow’ and click OK to confirm. That will import the CA into ESET so that it knows not to flag it. You then won’t see pop-ups even with SSL/TLS capabilities enabled.
TheLyppardMan
Very Senior Member
Where do I find the Pixelserv certificate?File > select your pixelserv ca.crt > select ‘Allow’ and click OK to confirm. That will import the CA into ESET so that it knows not to flag it. You then won’t see pop-ups even with SSL/TLS capabilities enabled.
TheLyppardMan
Very Senior Member
Where do I find the Pixelserv certificate?
Seriously, just scroll up. How hard are you trying really?
https://www.snbforums.com/threads/ab-solution-webpage-antivirus-problems.46817/#post-407709
I've managed to install it with the URL option, but it still hasn't solved the problem.
Have you restarted ESET? And honestly this would be better answered via the support emails you have sent them.
TheLyppardMan
Very Senior Member
Believe me, I am trying very hard, but your cryptic clues are not exactly very clear to someone who has never done this before. I'll reboot my computer which restart ESET and see if that makes any difference.Seriously, just scroll up. How hard are you trying really?
https://www.snbforums.com/threads/ab-solution-webpage-antivirus-problems.46817/#post-407709
TheLyppardMan
Very Senior Member
Restarting ESET makes no difference. I'm not going to waste any more time on this as it clearly causes more problems than it solves. I'll just use it for mobile devices and use uBlock Origin plug-in for Firefox.
I followed these instructions...
I'm still getting the error message as you can see. Also, I followed the procedure for Chrome on my daughter's laptop, but I didn't see any mention of a keychain as per these instructions...
- Open your browser and visit http://192.168.1.2/ca.crt.
- Select "Trust this CA to identify websites" on the screen pop-up (I also ticked the e-mail box as I wasn't sure if that was needed as well).
- Click "Ok"
By the way, what is the difference between a "CA" and a "cert"? The instructions refer to a "CA Certificate".
- Double click on `ca.crt' to start Keychain's import wizard.
- Select keychain "system" and click "Add".
Keychain is an Apple feature on Mac platform. If you aren't using macOS, you won't find it.
If you're using macOS, double click on "ca.crt" in your download directory that you've downloaded through "http://pixelserv ip/ca.crt" will launch Keychain.
Where do I find the Pixelserv certificate?
When you click on any URL that triggers a download action, on almost all desktop OS, the downloaded file is stored in your download directory.
So to re-iterate. e.g. when you click "http://pixelserv ip/ca.crt", the file ca.crt (also known as Pixelserv CA certificate) is downloaded and saved in your PC's download directory. You'll find the certificate there.
TheLyppardMan
Very Senior Member
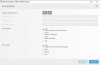
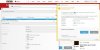
Thanks. I realised that files are usually downloaded to the user's downloads directory, but what I hadn't realised was that visiting the above URL was actually downloading a file to my PC. Anyway, I've just tried again and it seems that it's already installed somewhere (see screenshot 1), but either way, it hasn't solved the problem, so I'm going to leave it switched off wherever I have the option to use a browser-based ad filter. This is easy to achieve with the Merlin firmware (screenshots 2 & 3).Keychain is an Apple feature on Mac platform. If you aren't using macOS, you won't find it.
If you're using macOS, double click on "ca.crt" in your download directory that you've downloaded through "http://pixelserv ip/ca.crt" will launch Keychain.
When you click on any URL that triggers a download action, on almost all desktop OS, the downloaded file is stored in your download directory.
So to re-iterate. e.g. when you click "http://pixelserv ip/ca.crt", the file ca.crt (also known as Pixelserv CA certificate) is downloaded and saved in your PC's download directory. You'll find the certificate there.
Attachments
Latest threads
-
Asuswrt-Merlin 3004.288.8_4 /jffs Partition Nuked on Random Reboot
- Started by garycnew
- Replies: 0
-
Asus 2.4Ghz auto control channel chooses suboptimal channels
- Started by MKLBNS
- Replies: 7
-
-
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 1,856 (members: 13, guests: 1,843)