Asus GT-AX11000 (3004.388.4_beta3) OPENVPN Server help needed vith Site to Site:
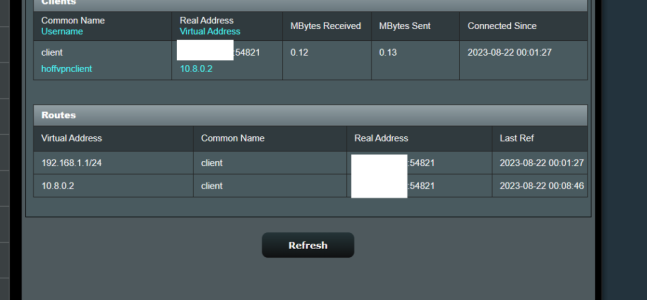
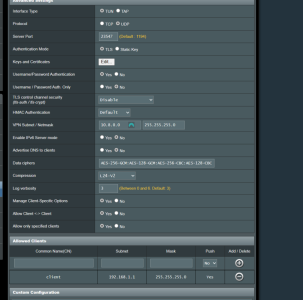
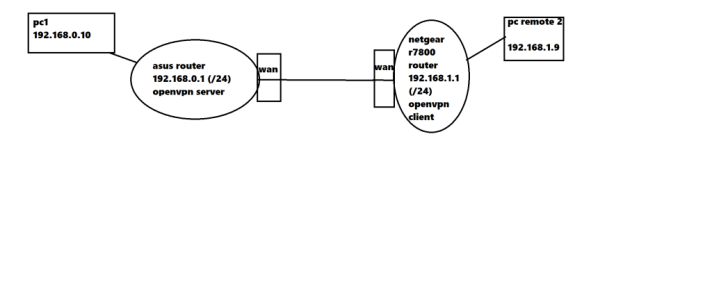
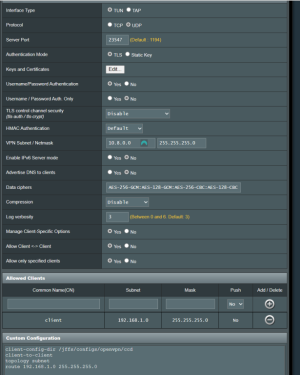
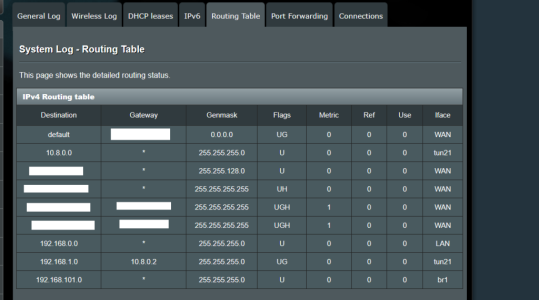
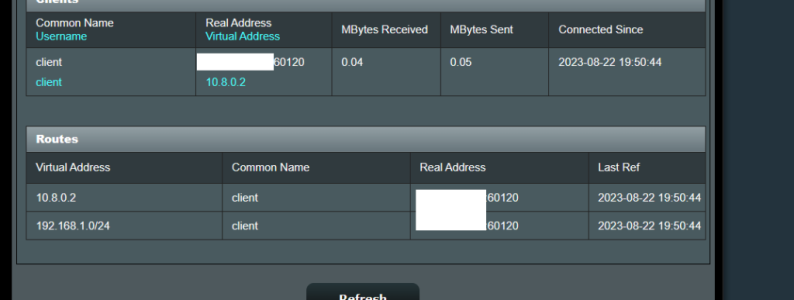
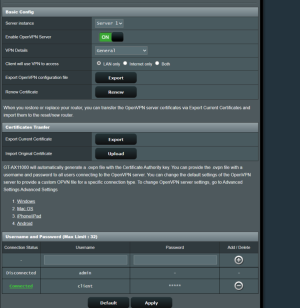
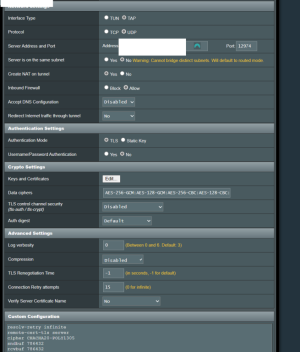
I have problem, with Asus GT-AX11000 (3004.388.4_beta3) OPENVPN Server network 1 (subnet: 192.168.0.0/24), i cannot access client (netgear 7800 with latest voxel firmware) network 2 (subnet: 192.168.1.0/24). Client is connected to my asus router's vpn server.
When i write on network 1, in some pc (example in pc 1: 192.168.0.10), network 2's ip, example pc remote 2: 192.168.1.9, the pc1's browser cannot resolv pc remote 2's ip address. What i'm doing wrong? Below pictures from server config.
UPDATE:
NEWER DETAILS/PICTURES FROM THE SETTINGS BELOW THIS LINK: https://www.snbforums.com/threads/a...p-needed-vith-site-to-site.86433/#post-860145
I have problem, with Asus GT-AX11000 (3004.388.4_beta3) OPENVPN Server network 1 (subnet: 192.168.0.0/24), i cannot access client (netgear 7800 with latest voxel firmware) network 2 (subnet: 192.168.1.0/24). Client is connected to my asus router's vpn server.
When i write on network 1, in some pc (example in pc 1: 192.168.0.10), network 2's ip, example pc remote 2: 192.168.1.9, the pc1's browser cannot resolv pc remote 2's ip address. What i'm doing wrong? Below pictures from server config.
UPDATE:
NEWER DETAILS/PICTURES FROM THE SETTINGS BELOW THIS LINK: https://www.snbforums.com/threads/a...p-needed-vith-site-to-site.86433/#post-860145
Attachments
Last edited: