Woofer Wrecker
Occasional Visitor
Greetings All, my first post here, and I apologize in advance for my ignorance. I know just enough to be dangerous. Hence why I have come begging for help!
I have successfully set up my RT-AX88U running Merlin 386.7, to run the Nord VPN OVPN on board. All my devices are currently run through the tunnel.
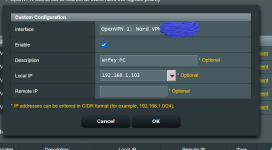
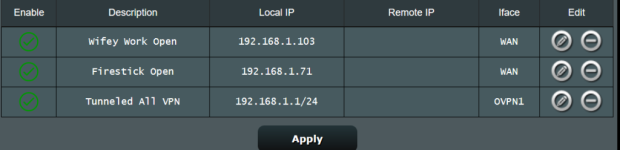
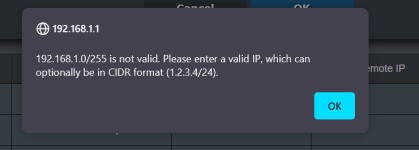
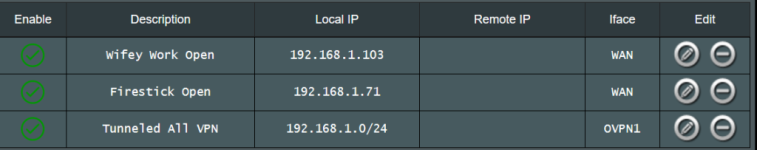
My issue arises when I set a specific device IP to not use the VPN, which I do by setting the router to use VPN director polices, and then adding the device IP as a new rule. I set the interface to the client I want, and do not enter a remote IP. Add the rule, apply it, and re boot the router. When restarted all devices are now bypassing the VPN tunnel, exposing my real IP address, which I do not want.
I need to exclude certain devices as wifey works remotely and has complained that she can not access certain work related sites due to VPN.
If there is any suggestions anyone has to help me get this resolved, I would be most grateful.
Thank you in advance!
WW
I have successfully set up my RT-AX88U running Merlin 386.7, to run the Nord VPN OVPN on board. All my devices are currently run through the tunnel.
My issue arises when I set a specific device IP to not use the VPN, which I do by setting the router to use VPN director polices, and then adding the device IP as a new rule. I set the interface to the client I want, and do not enter a remote IP. Add the rule, apply it, and re boot the router. When restarted all devices are now bypassing the VPN tunnel, exposing my real IP address, which I do not want.
I need to exclude certain devices as wifey works remotely and has complained that she can not access certain work related sites due to VPN.
If there is any suggestions anyone has to help me get this resolved, I would be most grateful.
Thank you in advance!
WW