Hi All,
Trying to figure out how I can access my OpenVPN server router admin from an ASUS-Merlin client through OpenVPN. I can access internet through VPN from client out from server just fine. All my other setups work fine to access the remote router admin.
My setup:
Router0 (Client OpenVPN) -> Main Router1 -> Internet -> Main Router2 -> Router3 (OpenVPN server)
When Client Router0 is dd-wrt, VPN works perfectly, from client I can access internet through Router3 and admin for Router3. This has worked for multiple different dd-wrt routers.
In addition, if I use OpenVPN from Windows 10 or Chromebook on Router1 LAN, can also access Router 3 admin over VPN by just typing in 192.168.0.1.
The problem:
When I use ASUS-Merlin 386.3_2 (ASUS RT86U) for Router0, through VPN, I can access the internet through Router3, but when I try to access admin for Router3, I instead get Router1. I have checked Redirect all traffic on Router0, but when I enter admin 192.168.0.1 to access admin, what I think would be Router3, I instead get the local Router 1. Router0 is not sending 192.168.0.1 to VPN.
Here are sample LANs:
Router0 (Merlin 386.3_2) -> Main Router1 -> Internet -> Main Router2 -> Router3 (OpenVPN server)
LAN:192.168.50.2----------->192.168.0.1-------------------->10.0.0.0---------->192.168.0.1 (VPN: 10.8.0.0)
I have read to avoid having similar subnets in VPN, but this set up works fine in all other cases except when I use the ASUS-Merlin as router0. It seems like the Merlin router VPN does not redirect the 192.168.0.1 request through the tunnel (where it would hit Router 3) but instead just routes it to Router1. I do have “Redirect Internet traffic through tunnel” selected as “Yes (all)”.
Anybody have any ideas how I can access my router 3 admin using an asus-merlin for router0?
When I look at routing table I can now see why on router0 a request to 192.168.0.1 goes to WAN, but I don’t have any idea how to change the routing table nor why this works fine when I hook up dd-wrt routers as router0? Since the routing table is built automatically--is there anyway can force the Asus-Merlin to behave like ddwrt routers and pass the 192.168.01 request to VPN?
I don’t want to change anything upstream of client router0, since it works fine with other routers. Any help is greatly appreciated!
Thank you
Router0, Merlin 386.3_2, ASUS RT86U
IPv4 Routing table:
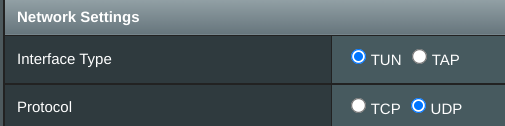
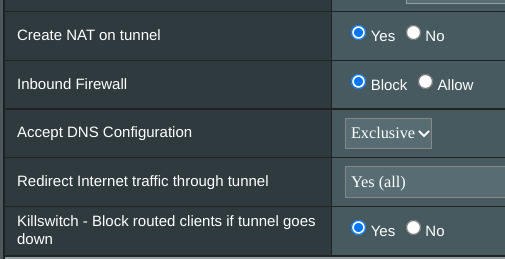
OpenVPN client settings, pretty much all default:

Thank you,
SunSkyPi
Trying to figure out how I can access my OpenVPN server router admin from an ASUS-Merlin client through OpenVPN. I can access internet through VPN from client out from server just fine. All my other setups work fine to access the remote router admin.
My setup:
Router0 (Client OpenVPN) -> Main Router1 -> Internet -> Main Router2 -> Router3 (OpenVPN server)
When Client Router0 is dd-wrt, VPN works perfectly, from client I can access internet through Router3 and admin for Router3. This has worked for multiple different dd-wrt routers.
In addition, if I use OpenVPN from Windows 10 or Chromebook on Router1 LAN, can also access Router 3 admin over VPN by just typing in 192.168.0.1.
The problem:
When I use ASUS-Merlin 386.3_2 (ASUS RT86U) for Router0, through VPN, I can access the internet through Router3, but when I try to access admin for Router3, I instead get Router1. I have checked Redirect all traffic on Router0, but when I enter admin 192.168.0.1 to access admin, what I think would be Router3, I instead get the local Router 1. Router0 is not sending 192.168.0.1 to VPN.
Here are sample LANs:
Router0 (Merlin 386.3_2) -> Main Router1 -> Internet -> Main Router2 -> Router3 (OpenVPN server)
LAN:192.168.50.2----------->192.168.0.1-------------------->10.0.0.0---------->192.168.0.1 (VPN: 10.8.0.0)
I have read to avoid having similar subnets in VPN, but this set up works fine in all other cases except when I use the ASUS-Merlin as router0. It seems like the Merlin router VPN does not redirect the 192.168.0.1 request through the tunnel (where it would hit Router 3) but instead just routes it to Router1. I do have “Redirect Internet traffic through tunnel” selected as “Yes (all)”.
Anybody have any ideas how I can access my router 3 admin using an asus-merlin for router0?
When I look at routing table I can now see why on router0 a request to 192.168.0.1 goes to WAN, but I don’t have any idea how to change the routing table nor why this works fine when I hook up dd-wrt routers as router0? Since the routing table is built automatically--is there anyway can force the Asus-Merlin to behave like ddwrt routers and pass the 192.168.01 request to VPN?
I don’t want to change anything upstream of client router0, since it works fine with other routers. Any help is greatly appreciated!
Thank you
Router0, Merlin 386.3_2, ASUS RT86U
IPv4 Routing table:
| IPv4 Routing table | |||||||
| Destination | Gateway | Genmask | Flags | Metric | Ref | Use | Iface |
| default | 192.168.0.1 | 0.0.0.0 | UG | 0 | 0 | 0 | WAN |
| 10.8.0.5 | * | 255.255.255.255 | UH | 0 | 0 | 0 | tun12 |
| 192.168.0.0 | * | 255.255.255.0 | U | 0 | 0 | 0 | WAN |
| 192.168.0.1 | * | 255.255.255.255 | UH | 0 | 0 | 0 | WAN |
| 192.168.50.0 | * | 255.255.255.0 | U | 0 | 0 | 0 | LAN |
OpenVPN client settings, pretty much all default:
Thank you,
SunSkyPi
