Hi everyone!
I've been using Asus since n66u and now sit on multiple routers from them with a continued appreciation of the power in these products!
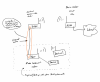
My question to all you networkers: Can I secure access from a router in AP mode to another router in repeater mode as the one AP mode is exposed outside my home, to avoid anyone just plugging in a cable and automatically given an IP address, as the repeater mode router is directly connected to the main router with DHCP enabled?
Background: With two n66u serving as APs to my ac86 I have made a connection down to the apartment building basement via an ethernet cable. Down there I have put my 3d printer (have permission from the board to use the basement for this stuff) and one of the APs is located with the printer to be able to have wifi down there and connect other equipment as well. As this is a huge security flaw in my network I would like to create an authentication between the APs in the picture and put a watchdog for any changes on this link, either breaking or new devices. if something happens it should disconnect the basement AP immediately.
I'm looking for a solution that doesnt involve disabling automatic DHCP. Anyone come across a similar challenge before and does the ASUS routers support such config tweaks/setup?
Very thankful for any guidance on this matter!
I've been using Asus since n66u and now sit on multiple routers from them with a continued appreciation of the power in these products!
My question to all you networkers: Can I secure access from a router in AP mode to another router in repeater mode as the one AP mode is exposed outside my home, to avoid anyone just plugging in a cable and automatically given an IP address, as the repeater mode router is directly connected to the main router with DHCP enabled?
Background: With two n66u serving as APs to my ac86 I have made a connection down to the apartment building basement via an ethernet cable. Down there I have put my 3d printer (have permission from the board to use the basement for this stuff) and one of the APs is located with the printer to be able to have wifi down there and connect other equipment as well. As this is a huge security flaw in my network I would like to create an authentication between the APs in the picture and put a watchdog for any changes on this link, either breaking or new devices. if something happens it should disconnect the basement AP immediately.
I'm looking for a solution that doesnt involve disabling automatic DHCP. Anyone come across a similar challenge before and does the ASUS routers support such config tweaks/setup?

Very thankful for any guidance on this matter!
Last edited:
