Hi all.
I'm running an Adguard container as my local DNS. It's a proxmox container, not the one you can install on the router. That one no longer works on whatever the latest version is for AX86U).
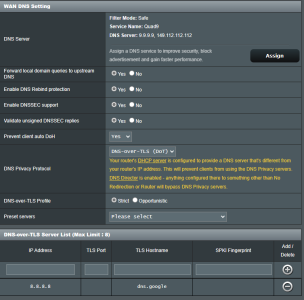
The WAN DNS section is set to Adguard (their public DNS, not my container). This is or should be used only by the router itself.
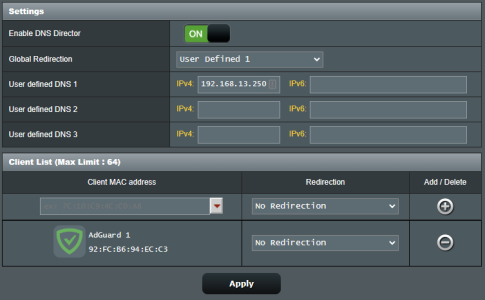
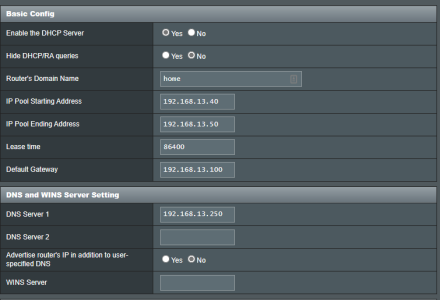
Everything else uses my local DNS via DHCP and/or is enforced by the director. The only "no redirection" is for the adguard container. Everything works well.
If a client doesn't use the DHCP assigned DNS, or is just a static client, the redirect still works. The problem is it will show up with the router's IP in the logs, and not the client that made the request.
Is there any way to see the IP of the client that made the redirected request, and ideally if it was a redirect?
Scenario: Have 10 "smart things" on an isolated YazFi guest network all using "hard coded" IP for some imaginary DNS, or just 5 computers with a preferred DNS option set.
Goal: To be able to tell which of them are behind a request, and ideally, if it was a redirect (be able to tell if the device is not using the DHCP DNS)
Did I misconfigure something or this is not possible?
PS: Sorry if this was asked before. I think I've gone through 20-30 posts here and on Reddit >.<
I'm running an Adguard container as my local DNS. It's a proxmox container, not the one you can install on the router. That one no longer works on whatever the latest version is for AX86U).
The WAN DNS section is set to Adguard (their public DNS, not my container). This is or should be used only by the router itself.
Everything else uses my local DNS via DHCP and/or is enforced by the director. The only "no redirection" is for the adguard container. Everything works well.
If a client doesn't use the DHCP assigned DNS, or is just a static client, the redirect still works. The problem is it will show up with the router's IP in the logs, and not the client that made the request.
Is there any way to see the IP of the client that made the redirected request, and ideally if it was a redirect?
Scenario: Have 10 "smart things" on an isolated YazFi guest network all using "hard coded" IP for some imaginary DNS, or just 5 computers with a preferred DNS option set.
Goal: To be able to tell which of them are behind a request, and ideally, if it was a redirect (be able to tell if the device is not using the DHCP DNS)
Did I misconfigure something or this is not possible?
PS: Sorry if this was asked before. I think I've gone through 20-30 posts here and on Reddit >.<