faux123
Regular Contributor
What is Snort? It is an open source intrusion prevention system (IPS) capable of real-time traffic analysis and packet logging.
Snort is an open source project under Gnu Public License (GPL) 2.0, it is an open source alternative to some of the proprietary IDS/IPS such as TrendMicro's AiProtect (which Asus has bundled with many Asus routers).

Quick background: Snort classic (2.x series) is single threaded (means it could only use 1 core regardless of the CPU architecture), this was a great limiting factor for its IPS performance and so not as widely adopted as Suricata (which was multi-threaded to begin with). Snort 3 was a HUGE rewrite from the Snort team to bring multi-threading capability to snort, now with 3.0+, snort has the same performance benefits as Suricata allowing the Snort IPS to scale with more CPU cores. One COOL thing about snort3 is the integration of OpenAppID (allows you to track specific apps such as Facebook, Twitter etc etc).
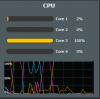
The Challenge: Snort3 is quite resource intensive in terms of both CPU and RAM (a resource hog, pun intended ). It was really designed for beefy computers or network appliances using Intel CPUs and with at least 2 Gigabytes of RAM. It needs the beefy CPUs in order to process many different rule sets and plenty of RAM to keep those rule sets in memory to perform Deep Packet Inspection (DPI) with minimal effect on overall network performance. By default, if you run snort3 on RT-AC86U with its laughable 512 MB of RAM, it would instantly crash with Out Of Memory (OOM) exception. To get it running on my setup, I had to read all its manuals and source code to understand how it uses the RAM and figure out what to enable and what to disable. After a few days of intensive reading, I have settled on a set of tweaks to allow snort 3 to run in IPS mode on the RT-AC86U.
). It was really designed for beefy computers or network appliances using Intel CPUs and with at least 2 Gigabytes of RAM. It needs the beefy CPUs in order to process many different rule sets and plenty of RAM to keep those rule sets in memory to perform Deep Packet Inspection (DPI) with minimal effect on overall network performance. By default, if you run snort3 on RT-AC86U with its laughable 512 MB of RAM, it would instantly crash with Out Of Memory (OOM) exception. To get it running on my setup, I had to read all its manuals and source code to understand how it uses the RAM and figure out what to enable and what to disable. After a few days of intensive reading, I have settled on a set of tweaks to allow snort 3 to run in IPS mode on the RT-AC86U.
Installation:
[prerequisite]:
1. You will need to have 2 GB of swap enabled and of course Entware installed already and functioning.
2. You want to disable TrendMicro's AiProtect and TrendMicro's Adaptive QoS (these options will interfere with Snort3 due to proprietary modules used bypass normal packet processing).
[Compatibility]:
1. Snort3 is compatible with Skynet
2. Snort3 is compatible with Unbound
3. Snort3 is compatible with YazFi
4. Snort3 is compatible with OpenVPN
5. Snort3 is compatible with CakeQoS (and highly recommended since disabling of AdaptiveQoS will need a replacement and CakeQoS just works)
6. Snort3 is compatible with Wireguard (alternative to OpenVPN)
Snort3 has many similar dependencies as Snort classic. At this moment, snort classic is available as part of Entware. So the best way to install snort3 is to install snort classic first, then delete snort classic and install my packages afterwards which are specific to snort3.
SSH into your router:
after snort classic installation, remove it by:
then download snort3 specific packages from my repo here:
 github.com
github.com
At this moment, you should test your snort3 installation by typing the following command:
this validates your snort version (3.0.0) and you should see information about the build feature sets
then follow by below:
Next is to register with snort.org, so you can download the latest snort3 rule sets here:
(above can only be accessible to registered users)
Oh and grab their community rules here as well:
(I put my community rules under: /opt/lib/snort3/ folder but you can put it anywhere you want, just change the -R option in the init.d file).
Oh and definitely grab the OpenAppID here:
(I put my OpenAppID folder 'odp' under '/opt/lib/', but you can put it anywhere you want, just change snort.lua file with the right locations).
To unzip the archives:
Then grab my init.d script from my repo here:
To get started you want to first edit a couple of files:
open /opt/etc/snort/snort.lua and change:
from line 32 to line 35: add -- in front of all those lua path settings
to
line 55: from HOME_NET = 'any' to HOME_NET='192.168.1.1/24' (whatever your internal LAN address was assigned to)
line 123: from --app_detector_dir = 'directory to load appid detectors from' to app_detector_dir='/opt/lib', (this assumes you put your odp folder under /opt/lib/)
line 201: from --enable_builtin_rules = true, to enable_builtin_rules = true, (remove the -- in front of that line)
and finally change
line 261: from --alert_fast = { } to alert_fast = { file = true, }
then create the folder for the logs by:
Final validation to ensure all the settings are correct!
Now to finally get it started:
This will kick start snort3 in IPS mode (assuming all the settings are working, since snort is a very heavy process and resource intensive, it may take up to 45 seconds or more to have it up and fully running).
To stop it, simply do:
NOTE: Often time it would say 'failed', but that's not the case, it simply 'timed out' because the shutdown process is also VERY HEAVY (it doesn't die immediately as it needs to flush all its memory content, free up the swap usage etc etc), it may take up to 2 min or more for the process to finally shutdown (patience is required here).
To see the logs, they are located in /opt/var/log/snort/ folder and you should see alert_fast.txt file to log all activities.
I have captured my own configurations here as a reference:
 github.com
(this is assuming you have community rules downloaded, the VRT rules downloaded for registered users, OpenAppID download and all of them placed in the folders based on my own settings).
github.com
(this is assuming you have community rules downloaded, the VRT rules downloaded for registered users, OpenAppID download and all of them placed in the folders based on my own settings).
With the above tweaks and settings, this will allow RT-AC86U (and RT-AX88U) to have a functioning IPS with Snort3. This is JUST the beginning, I hope this will get some users started to think about IPS for home and then develop rule sets which we can all benefit from and share with everyone else here as I have shared my work here.
One other note, I'm pretty busy normally, so I won't be "supporting" users here often, but I'm hoping the community members here to help each other out with issues, I will focus more on the code aspect!
Enjoy, have fun and keep the Open Source Spirit going!
Special shout out to @rgnldo with his Suricata thread to get me started and of course to @RMerlin for his Merlin magic.
Snort is an open source project under Gnu Public License (GPL) 2.0, it is an open source alternative to some of the proprietary IDS/IPS such as TrendMicro's AiProtect (which Asus has bundled with many Asus routers).
Quick background: Snort classic (2.x series) is single threaded (means it could only use 1 core regardless of the CPU architecture), this was a great limiting factor for its IPS performance and so not as widely adopted as Suricata (which was multi-threaded to begin with). Snort 3 was a HUGE rewrite from the Snort team to bring multi-threading capability to snort, now with 3.0+, snort has the same performance benefits as Suricata allowing the Snort IPS to scale with more CPU cores. One COOL thing about snort3 is the integration of OpenAppID (allows you to track specific apps such as Facebook, Twitter etc etc).
The Challenge: Snort3 is quite resource intensive in terms of both CPU and RAM (a resource hog, pun intended
WARNING (RT-AC86U): To run snort3, it is recommended to have ACTIVE COOLING solution as the demands of Snort3 will CAUSE the router to HEAT UP. An external USB Fan or equivalent solution IS RECOMMENDED! You have been WARNED! (RT-AX88U users have reported to be okay, just be careful)
Installation:
[prerequisite]:
1. You will need to have 2 GB of swap enabled and of course Entware installed already and functioning.
2. You want to disable TrendMicro's AiProtect and TrendMicro's Adaptive QoS (these options will interfere with Snort3 due to proprietary modules used bypass normal packet processing).
[Compatibility]:
1. Snort3 is compatible with Skynet
2. Snort3 is compatible with Unbound
3. Snort3 is compatible with YazFi
4. Snort3 is compatible with OpenVPN
5. Snort3 is compatible with CakeQoS (and highly recommended since disabling of AdaptiveQoS will need a replacement and CakeQoS just works)
6. Snort3 is compatible with Wireguard (alternative to OpenVPN)
Snort3 has many similar dependencies as Snort classic. At this moment, snort classic is available as part of Entware. So the best way to install snort3 is to install snort classic first, then delete snort classic and install my packages afterwards which are specific to snort3.
SSH into your router:
ssh your_username@your_router_ip
Bash:
opkg update
opkg install snort
Bash:
opkg remove snortRelease Initial snort3 release for Merlin firmware · faux123/snort3
this is the first release for snort3 running on Merlin firmware (specifically for HND models such as RT-AC86U and RT-AX88U).
Bash:
wget https://github.com/faux123/snort3/releases/download/3.0.0.0-beta4/libpciaccess_0.16-1_aarch64-3.10.ipk
wget https://github.com/faux123/snort3/releases/download/3.0.0.0-beta4/libhwloc_2.1.0-1_aarch64-3.10.ipk
wget https://github.com/faux123/snort3/releases/download/3.0.0.0-beta4/snort3_3.0.0-beta-4_aarch64-3.10.ipk
opkg install libpciaccess_0.16-1_aarch64-3.10.ipk
opkg install libhwloc_2.1.0-1_aarch64-3.10.ipk
opkg install snort3_3.0.0-beta-4_aarch64-3.10.ipkAt this moment, you should test your snort3 installation by typing the following command:
Bash:
snort -Vthen follow by below:
Next is to register with snort.org, so you can download the latest snort3 rule sets here:
Snort - Network Intrusion Detection & Prevention System
Snort is an open-source, free and lightweight network intrusion detection system (NIDS) software for Linux and Windows to detect emerging threats.
www.snort.org
Oh and grab their community rules here as well:
(I put my community rules under: /opt/lib/snort3/ folder but you can put it anywhere you want, just change the -R option in the init.d file).
Oh and definitely grab the OpenAppID here:
(I put my OpenAppID folder 'odp' under '/opt/lib/', but you can put it anywhere you want, just change snort.lua file with the right locations).
To unzip the archives:
tar -xzf your_filename.tar.gzThen grab my init.d script from my repo here:
Bash:
wget https://raw.githubusercontent.com/faux123/snort3_config/master/init.d/S81Snort3
cp S81Snort3 /opt/etc/init.d/
chmod 755 /opt/etc/init.d/S81Snort3To get started you want to first edit a couple of files:
open /opt/etc/snort/snort.lua and change:
from line 32 to line 35: add -- in front of all those lua path settings
Code:
lua_path = os.getenv('LUA_PATH')
if ( not lua_path ) then
package.path = '/opt/include/snort/lua/?.lua;?;'
end
Code:
--lua_path = os.getenv('LUA_PATH')
--if ( not lua_path ) then
-- package.path = '/opt/include/snort/lua/?.lua;?;'
--endline 123: from --app_detector_dir = 'directory to load appid detectors from' to app_detector_dir='/opt/lib', (this assumes you put your odp folder under /opt/lib/)
line 201: from --enable_builtin_rules = true, to enable_builtin_rules = true, (remove the -- in front of that line)
and finally change
line 261: from --alert_fast = { } to alert_fast = { file = true, }
then create the folder for the logs by:
Bash:
mkdir /opt/var/log/snort/Final validation to ensure all the settings are correct!
Bash:
snort -T -z 1 --daq afpacket --daq-dir /opt/lib/daq --daq-var buffer_size_mb=32 -Q -i eth0:br0 -c /opt/etc/snort/snort.luaNow to finally get it started:
Bash:
/opt/etc/init.d/S81Snort3 startTo stop it, simply do:
Bash:
/opt/etc/init.d/S81Snort3 stopTo see the logs, they are located in /opt/var/log/snort/ folder and you should see alert_fast.txt file to log all activities.
I have captured my own configurations here as a reference:
GitHub - faux123/snort3_config: repo to track snort3 config lua over time
repo to track snort3 config lua over time. Contribute to faux123/snort3_config development by creating an account on GitHub.
With the above tweaks and settings, this will allow RT-AC86U (and RT-AX88U) to have a functioning IPS with Snort3. This is JUST the beginning, I hope this will get some users started to think about IPS for home and then develop rule sets which we can all benefit from and share with everyone else here as I have shared my work here.
One other note, I'm pretty busy normally, so I won't be "supporting" users here often, but I'm hoping the community members here to help each other out with issues, I will focus more on the code aspect!
Enjoy, have fun and keep the Open Source Spirit going!
Special shout out to @rgnldo with his Suricata thread to get me started and of course to @RMerlin for his Merlin magic.
Last edited: