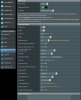
I have mine setup exactly like yours now and when I export the ovpn file in the GUI I still get the empty paste here. In the GUI there is only a static key and no CA. If I try to connect on Android, it gives me the: "OpenVPN core error : PolarSSL: error parsing ca certificate : X509 - The CRT/CRL/CSR format is invalid".
client
dev tun
proto udp
remote xxxx.xxxxx.com 1194
float
cipher AES-128-CBC
auth SHA1
comp-lzo adaptive
keepalive 15 60
auth-user-pass
ns-cert-type server
<ca>
adaptive
</ca>
<cert>
paste client certificate data here
</cert>
<key>
paste client key data here
</key>
resolv-retry infinite
nobind
If I look manually in the router via SSH, i can see the is a ca.crt and server.crt. Shouldn't these cert be showing in the export OVPN file instead of empty and the paste here?
/tmp/etc/openvpn/server1
-rw-rw-rw- 1 admin root 3803 May 10 21:01 01.pem
-rw-rw-rw- 1 admin root 3675 May 10 21:01 02.pem
-rw-rw-rw- 1 admin root 1172 May 10 21:01 ca.crt
-rw------- 1 admin root 916 May 10 21:01 ca.key
-rw-rw-rw- 1 admin root 3675 May 10 21:01 client.crt
-rw-rw-rw- 1 admin root 660 May 10 21:01 client.csr
-rw------- 1 admin root 916 May 10 21:01 client.key
-rw-rw-rw- 1 admin root 307 May 10 21:01 client.ovpn
-rw-rw-rw- 1 admin root 18 May 10 21:07 client_status
-rw------- 1 admin root 349 May 10 21:01 config.ovpn
-rw-rw-r-- 1 admin root 424 May 10 21:01 dh.pem
-rw-rw-rw- 1 admin root 198 May 10 21:01 index.txt
-rw-rw-rw- 1 admin root 21 May 10 21:01 index.txt.attr
-rw-rw-rw- 1 admin root 21 May 10 21:01 index.txt.attr.old
-rw-rw-rw- 1 admin root 100 May 10 21:01 index.txt.old
-rw-rw-rw- 1 admin root 3 May 10 21:01 serial
-rw-rw-rw- 1 admin root 3 May 10 21:01 serial.old
-rw-rw-rw- 1 admin root 3803 May 10 21:01 server.crt
-rw-rw-rw- 1 admin root 664 May 10 21:01 server.csr
-rw------- 1 admin root 916 May 10 21:01 server.key
-rw------- 1 admin root 559 May 10 21:07 status