It used to be "piece of cake" (easy) to install a new client1.ovpn file, but this time I had several problems. On my android mobil it demanded a newer ovenovp - which worked OK, but on my computer the same solution failed. I have checked the new client1 file against the old and there is some small differences: The two lines about chipers!
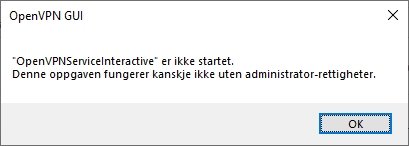
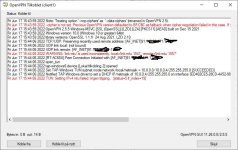
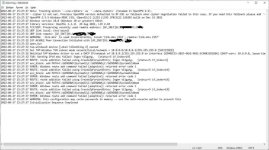
I enclose these (client0 is the old) and also the popup with red warnings and the client1.log and a small popup about "not started" when i start Openvpn Gui (which seems to start anyway).
I have installed the new openvpn on my computer.
Hope this forum can help me.
I enclose these (client0 is the old) and also the popup with red warnings and the client1.log and a small popup about "not started" when i start Openvpn Gui (which seems to start anyway).
I have installed the new openvpn on my computer.
Hope this forum can help me.