Hi All 
At work we're using a BT BusinessHub as our main router. Previously we used an AC86U but now we have BT's 4G Assure failover, which is essential for our SIP phones we've had to revert back.
Our LAN address is 192.168.48.0
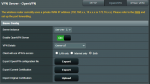
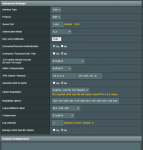
I currently have the AC86U sitting on it's own network of 192.168.49.0 as a VPN Server & Guest Access WiFi AP. All works great, other than when I try to restrict VPN clients to use the VPN for LAN access only. Before 4G assure, the AC86U was also the main router and just toggling the "Client will use VPN to access" to LAN only did the trick. This toggle now doesn't work as it's on it's own network, so has to be set to "Both" to allow clients to access the 48.0 LAN.
Does anyone know how I can get around this issue server side? I wondered if there was a custom configuration I could input?
Attached are screenshots of our current config.
Many thanks!
At work we're using a BT BusinessHub as our main router. Previously we used an AC86U but now we have BT's 4G Assure failover, which is essential for our SIP phones we've had to revert back.
Our LAN address is 192.168.48.0
I currently have the AC86U sitting on it's own network of 192.168.49.0 as a VPN Server & Guest Access WiFi AP. All works great, other than when I try to restrict VPN clients to use the VPN for LAN access only. Before 4G assure, the AC86U was also the main router and just toggling the "Client will use VPN to access" to LAN only did the trick. This toggle now doesn't work as it's on it's own network, so has to be set to "Both" to allow clients to access the 48.0 LAN.
Does anyone know how I can get around this issue server side? I wondered if there was a custom configuration I could input?
Attached are screenshots of our current config.
Many thanks!