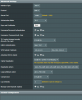
I need to leave VPN enabled from WAN to LAN. WAN works fine, LAN does not. It works with the OEM firmware, but it looks like WRT-Merlin has some issue with LAN. On LAN fail, the client log shows:
2019-12-28 10:42:03 ----- OpenVPN Start ----- OpenVPN core 3.git::2ae73415 ios arm64 64-bit PT_PROXY built on Dec 2 2019 14:44:28
2019-12-28 10:42:03 OpenVPN core 3.git::2ae73415 ios arm64 64-bit PT_PROXY built on Dec 2 2019 14:44:28
2019-12-28 10:42:03 Frame=512/2048/512 mssfix-ctrl=1250
2019-12-28 10:42:03 UNUSED OPTIONS
5 [ncp-ciphers] [AES-256-GCM:AES-128-GCM:AES-256-CBC:AES-128-CBC]
15 [resolv-retry] [infinite]
16 [nobind]
2019-12-28 10:42:03 EVENT: RESOLVE
2019-12-28 10:42:03 Contacting [router wan address removed]:1300/UDP via UDP
2019-12-28 10:42:03 EVENT: WAIT
2019-12-28 10:42:03 Connecting to [ddnsremoved]:1300 (router wan address removed) via UDPv4
2019-12-28 10:42:13 Server poll timeout, trying next remote entry...
2019-12-28 10:42:13 EVENT: RECONNECTING
2019-12-28 10:42:13 EVENT: RESOLVE
2019-12-28 10:42:13 Contacting [router wan address removed]:1300/UDP via UDP
2019-12-28 10:42:13 EVENT: WAIT
2019-12-28 10:42:13 Connecting to [ddnsremoved]:1300 (router wan address removed) via UDPv4
The router log shows:
Dec 28 10:55:30 ovpn-server1[13681]: MULTI: multi_create_instance called
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Re-using SSL/TLS context
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Control Channel MTU parms [ L:1621 D:1212 EF:38 EB:0 ET:0 EL:3 ]
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1601,tun-mtu 1500,proto UDPv4,cipher AES-256-CBC,auth SHA512,keysize 256,key-method 2,tls-server'
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1601,tun-mtu 1500,proto UDPv4,cipher AES-256-CBC,auth SHA512,keysize 256,key-method 2,tls-client'
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 READ [14] from [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 TLS: Initial packet from [AF_INET]192.168.0.143:52687, sid=3829896b cdce2f1e
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 WRITE [26] to [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ 0 ] pid=0 DATA len=0
Dec 28 10:55:31 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 READ [14] from [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Dec 28 10:55:31 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 WRITE [22] to [AF_INET]192.168.0.143:52687: P_ACK_V1 kid=0 [ 0 ]
Dec 28 10:55:32 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 READ [14] from [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Read/Write, Hard Reset received many times.
Any input is appreciated.
2019-12-28 10:42:03 ----- OpenVPN Start ----- OpenVPN core 3.git::2ae73415 ios arm64 64-bit PT_PROXY built on Dec 2 2019 14:44:28
2019-12-28 10:42:03 OpenVPN core 3.git::2ae73415 ios arm64 64-bit PT_PROXY built on Dec 2 2019 14:44:28
2019-12-28 10:42:03 Frame=512/2048/512 mssfix-ctrl=1250
2019-12-28 10:42:03 UNUSED OPTIONS
5 [ncp-ciphers] [AES-256-GCM:AES-128-GCM:AES-256-CBC:AES-128-CBC]
15 [resolv-retry] [infinite]
16 [nobind]
2019-12-28 10:42:03 EVENT: RESOLVE
2019-12-28 10:42:03 Contacting [router wan address removed]:1300/UDP via UDP
2019-12-28 10:42:03 EVENT: WAIT
2019-12-28 10:42:03 Connecting to [ddnsremoved]:1300 (router wan address removed) via UDPv4
2019-12-28 10:42:13 Server poll timeout, trying next remote entry...
2019-12-28 10:42:13 EVENT: RECONNECTING
2019-12-28 10:42:13 EVENT: RESOLVE
2019-12-28 10:42:13 Contacting [router wan address removed]:1300/UDP via UDP
2019-12-28 10:42:13 EVENT: WAIT
2019-12-28 10:42:13 Connecting to [ddnsremoved]:1300 (router wan address removed) via UDPv4
The router log shows:
Dec 28 10:55:30 ovpn-server1[13681]: MULTI: multi_create_instance called
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Re-using SSL/TLS context
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Control Channel MTU parms [ L:1621 D:1212 EF:38 EB:0 ET:0 EL:3 ]
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1601,tun-mtu 1500,proto UDPv4,cipher AES-256-CBC,auth SHA512,keysize 256,key-method 2,tls-server'
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1601,tun-mtu 1500,proto UDPv4,cipher AES-256-CBC,auth SHA512,keysize 256,key-method 2,tls-client'
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 READ [14] from [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 TLS: Initial packet from [AF_INET]192.168.0.143:52687, sid=3829896b cdce2f1e
Dec 28 10:55:30 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 WRITE [26] to [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ 0 ] pid=0 DATA len=0
Dec 28 10:55:31 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 READ [14] from [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Dec 28 10:55:31 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 WRITE [22] to [AF_INET]192.168.0.143:52687: P_ACK_V1 kid=0 [ 0 ]
Dec 28 10:55:32 ovpn-server1[13681]: 192.168.0.143:52687 UDPv4 READ [14] from [AF_INET]192.168.0.143:52687: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Read/Write, Hard Reset received many times.
Any input is appreciated.
Attachments
Last edited: